
Xion
@0x10n
CMU CSD PhD student / 2024 Top#0 Chrome VRP Researcher / Winner of Pwn2Own Vancouver '24, TyphoonPWN '24, DEFCON 31 CTF, ... / PPP, KAIST GoN '18, @zer0pts
ID: 1298620596406743040
https://github.com/leesh3288 26-08-2020 13:57:42
359 Tweet
3,3K Followers
122 Following





🤔 [$55000](CVE-2024-12692)[382291459][wasm]Type Confusion in V8(comparison of canonical struct types) "Compare fields, including a check that the size is the same and compare mutabilities, skipping the check for the size" chromereleases.googleblog.com/2024/12/stable… chromium-review.googlesource.com/c/v8/v8/+/6074… Xion










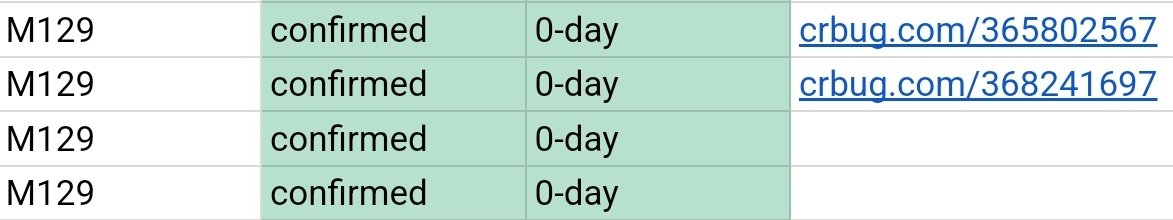
![xvonfers (@xvonfers) on Twitter photo (CVE-2024-9122)[365802567][$55000][wasm]WASM type confusion due to imported tag signature subtyping is now open with PoC and exploit(pops calc from a '--no-sandbox' renderer):
issues.chromium.org/issues/3658025…
<a href="/0x10n/">Xion</a> (CVE-2024-9122)[365802567][$55000][wasm]WASM type confusion due to imported tag signature subtyping is now open with PoC and exploit(pops calc from a '--no-sandbox' renderer):
issues.chromium.org/issues/3658025…
<a href="/0x10n/">Xion</a>](https://pbs.twimg.com/media/Gfq4kiVXoAA6j1I.jpg)
