Mahesh Bheema
@0xmahesh
Security Enthusiast | OSCP | OSWP | Null Hyderabad Chapter Lead
ID: 190786633
14-09-2010 20:54:53
330 Tweet
558 Followers
432 Following




Some pics from NULL Hyderabad July meet. Talks: News Bytes by Karan Cloud Security & S3 by Aravind V Cloud Security Zero to One by Ravi Teja Intro to Threat Hunting by Donny Venue sponsor: ServiceNow #nullHyd #InfoSec null - The Open Security Community






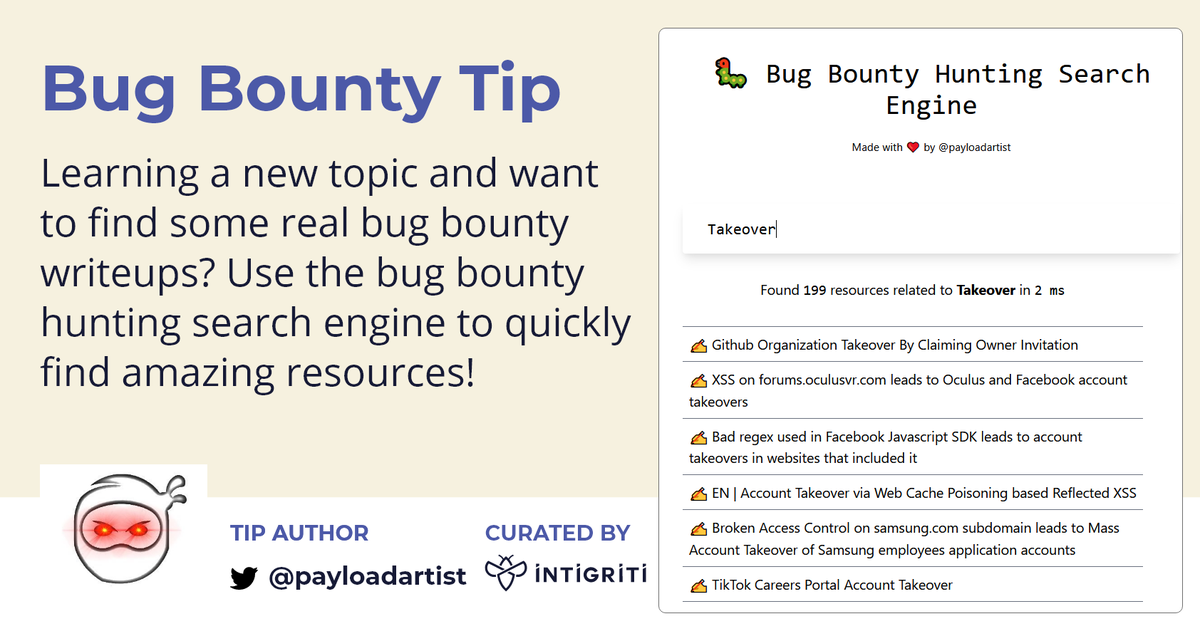
Learning from others is amazing, but how do you find the content you're looking for? payloadartist solved that problem by creating the Bug Bounty Hunting Search Engine! hubs.li/Q01B0C100 #bugbounty #bugbountytips 👇




We've just published a quick write up on CVE-2023-23397, which allows a remote adversary to leak NetNTLMv2 hashes: mdsec.co.uk/2023/03/exploi… by Dominic Chell 👻




April meet registrations are open. Register before it's too late. Date: April 22 Venue: EPAM Systems nullhydapr2023.eventbrite.com #NullHyd null - The Open Security Community Hari Mahesh Bheema badc0d3r Pavan

May meet registrations are open. Register before it's too late here nullhydmay2023.eventbrite.com. Date: May 27th Venue:@Servicenow #NullHyd null - The Open Security Community Hari Pavan badc0d3r Mahesh Bheema