AppSecEngineer
@appsecengineer
Painless Application Security Training for Enterprises.
Empower Your Teams. Build Secure Applications.
ID: 978820200240906240
https://appsecengineer.com/ 28-03-2018 02:24:56
5,5K Tweet
4,4K Followers
207 Following

Zero Trust has become a widely discussed security model, but how do you actually threat model a Zero Trust system? Here’s Abhay Bhargav ’s take on it: ➩ For new (green-field) developments – Zero Trust shouldn’t be the starting assumption. Instead, it should be something you





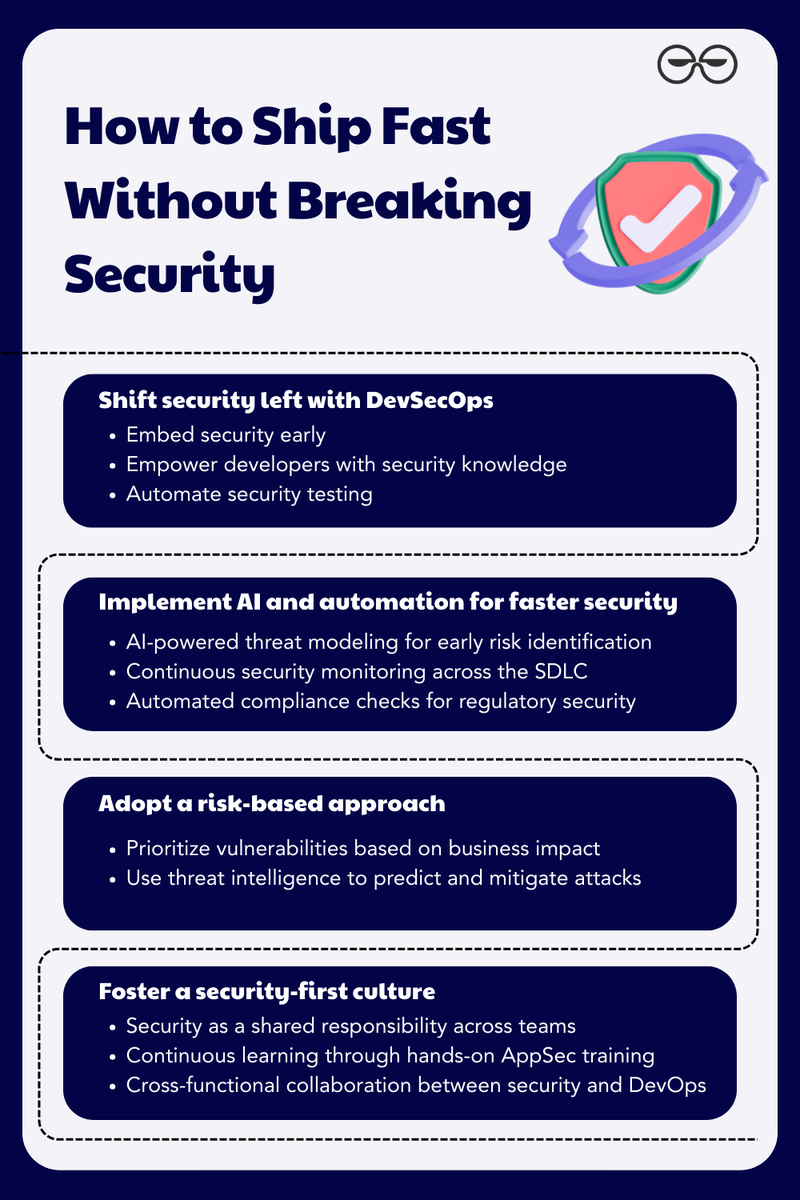
Spring Boot apps are everywhere. So are the vulnerabilities. In this short hands-on session, Abhay Bhargav dives into real-world security flaws in Java Spring Boot applications, how they’re exploited and how to defend against them. Watch how we break and fix them using






We've been waiting for this… and it's finally here! 🎉 SecurityReviewAI just launched and it's changing the way we do code reviews forever. Built for speed. Backed by real security expertise. Go check it out → SecurityReviewAI

A chatbot in healthcare isn’t just a nice-to-have. It could be the difference between privacy and a breach. Between automation and a life-or-death decision. Watch Abhay Bhargav break down a real risk healthcare orgs are overlooking. Link to full webinar: