Dr. Ch33r10
@ch33r10
#CTI • #PurpleTeam • Latina 🇲🇽 • Opinions are my own
ID: 816221
http://github.com/ch33r10 06-03-2007 22:49:15
39,39K Tweet
12,12K Followers
7,7K Following


📢Giveaway! 🎁 I'm sponsoring 5 people to join the The DFIR Report's DFIR Labs CTF for FREE on March 8th! To enter: Like this post, comment, and follow (so I can DM if you win). Winners will be chosen this Sunday! #DFIR








📢Giveaway! 🎁 I'm sponsoring 5 people to join the The DFIR Report's DFIR Labs CTF for FREE on June 7th! To enter: Like this post, comment, and follow (so I can DM if you win). Winners will be chosen this Sunday (June 1st)! #DFIR



Looking forward to giving my first TEAM CYMRU research webinar tomorrow! I shall be discussing a hot topic for many: DPRK IT Workers👨🏻💻 Tune into this tomorrow if you’re interested in how you can use NetFlow data to detect the 🇰🇵 activities 🔍 Reg here: team-cymru.zoom.us/webinar/regist…

Join me tomorrow for a live Recorded Future briefing on the conflict between Israel and Iran. We’ll address specific geopolitical risks, cybercriminal and hacktivist groups, state-sponsored cyber threats, influence operations, and more. Registration: …cordedfuture.registration.goldcast.io/webinar/4b7227…





Interested in learning how to build a lab VM for malware analysis and reversing? You can download a 40+ page chapter on this topic, taken from my book Evasive Malware. Get the PDF from my blog, here: 🤓 evasivemalware.com/EvasiveMalware… CC No Starch Press

Injecting to a remote process with reduced process access (PROCESS_CREATE_THREAD and PROCESS_QUERY_LIMITED_INFORMATION only). No ROP gadgets needed. Just clever use of Native API calls. Post by Thanos (trickster0). Good job, sir! trickster0.github.io/posts/Primitiv… #redteam #maldev
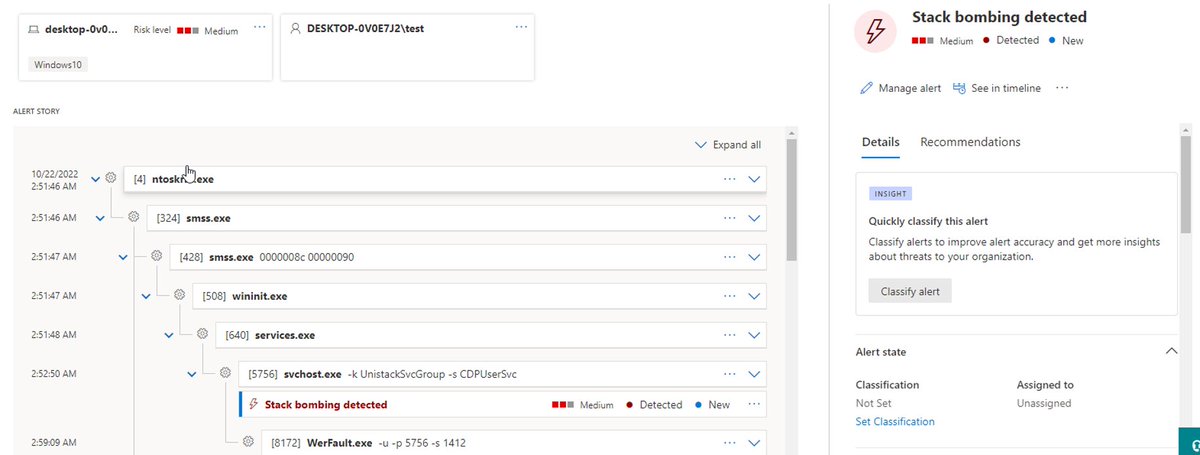









![Stephan Berger (@malmoeb) on Twitter photo I successfully tested a LSASS dumping technique on a Windows 10 lab machine, which we encountered on a recent Incident Response engagement (no EDR, default Defender installed).
The "MiniDumpWriteDump" technique, as described here [1], was successful in writing the LSASS process I successfully tested a LSASS dumping technique on a Windows 10 lab machine, which we encountered on a recent Incident Response engagement (no EDR, default Defender installed).
The "MiniDumpWriteDump" technique, as described here [1], was successful in writing the LSASS process](https://pbs.twimg.com/media/Gtyv3ICWQAApMKf.jpg)

