
Cyber Security Tribe
@cybrsectribe
An online resource providing thought leadership including insights from the most renowned cyber security professionals.
ID: 1614764887791620103
https://www.cybersecuritytribe.com/ 15-01-2023 23:22:20
153 Tweet
77 Followers
105 Following




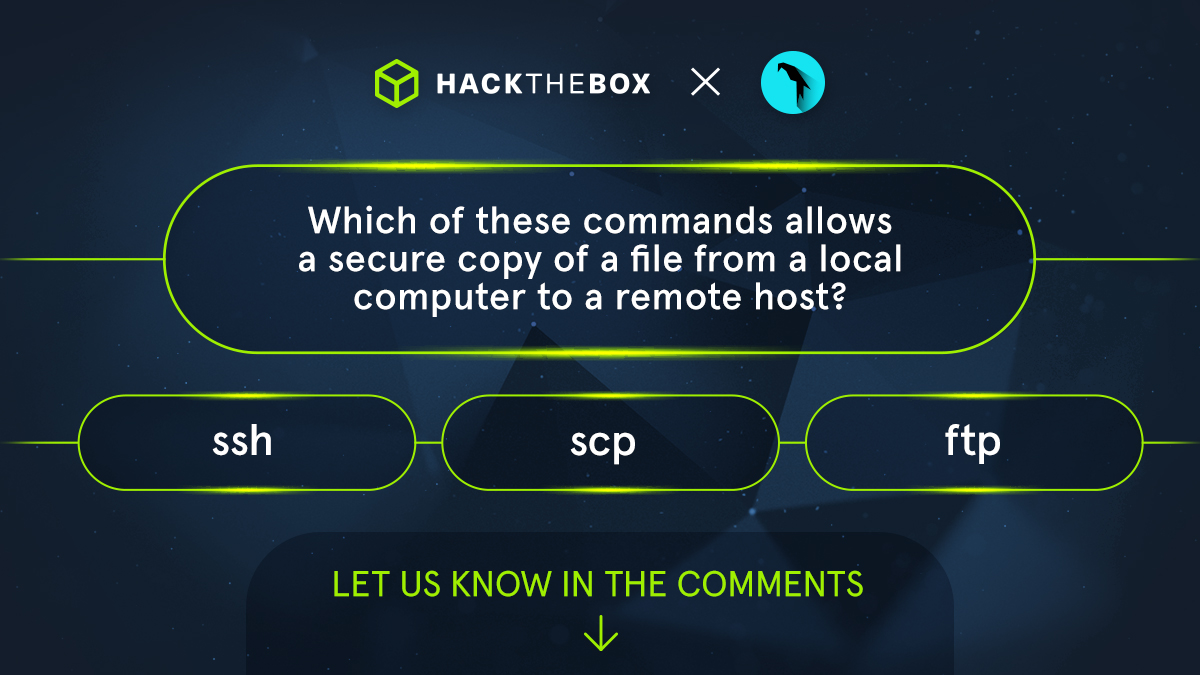
💡 Let's put your #hacking trivia to the test: Can you guess this #command? Let us know in the comments 👇 #HackTheBox #HTB #Hacking #Cybersecurity Parrot Security





Data breach at French govt agency exposes info of 10 million people - Bill Toulas bleepingcomputer.com/news/security/…



hubs.ly/Q0247bTV0 To shed light on the critical importance of risk management, Cyber Security Tribe recently had the privilege of chatting with a prominent figure in the field: Randall Frietzsche, the Chief Information Security Officer (CISO) at Denver Health.



Network security resilience is the ability to withstand & recover from cyber-attacks. To achieve this, organizations need to use DDI technology. DDI stands for DNS, DHCP & IPAM. These are 3 services that help devices connect & communicate on a network. jefforr.ventanaresearch.com/build-network-…



🛡️ Kate Bolseth, CEO at Fortra, spoke to Cyber Security Tribe about Fortra’s vision and how we’re helping CISOs solve the challenges they face. Check out the full interview here. ➡️ hubs.la/Q02dHSJ20 #cybersecurity #CISO #CybersecurityAlly


🚨 New #Cybersecurity Advisory: Cybersecurity and Infrastructure Security Agency & FBI released details on #Androxgh0st Malware, including #TTPs, #IOCs & mitigations. Organizations are strongly advised to implement recommended mitigations. Stay proactive against cyber threats! 🛡️cisa.gov/news-events/cy…



AI was one of the top of mind topics last week at #RSAC. Will Schroeder shared his perspective on how #AI is shaping #cybersecurity defenses against evolving threats. Read more from Cyber Security Tribe. ghst.ly/3yqh8sN




