
Douglas
@dglife
Noites estreladas, luzes da cidade vindo sobre mim.
Vi meus olhos refletidos pelos seus :)
ID: 67196941
20-08-2009 02:06:23
2,2K Tweet
367 Followers
3,3K Following


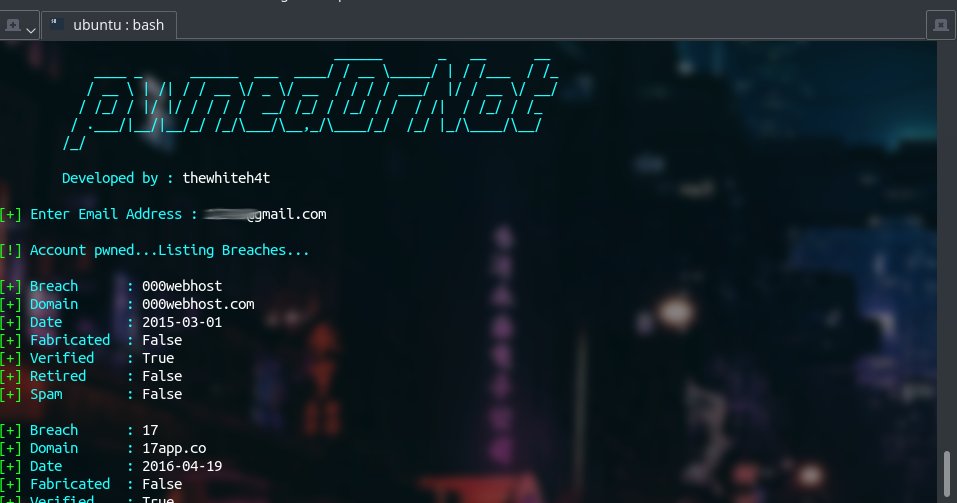
pwnedOrNot - Tool To Find Passwords For Compromised Email Accounts Using HaveIBeenPwned API dlvr.it/QVPl5P ☣ KitPloit - Hacker Tools

Similar Request Excluder. A Burp Suite extension that automagically marks similar requests as 'out-of-scope'. Now available in the BApp Store! 😀 github.com/tijme/similar-…

ssh-auditor The best way to scan for weak ssh passwords on your network > I 💛 this tool by NCSAatIllinois cause it satisfies all my usability needs github.com/ncsa/ssh-audit…



Deste do dia 06/10/2020 com a internet horrível da Claro Brasil e @NEToficial , o técnico estão cancelando as visitas técnicas e no atendimento automático não tem nenhum problema na região. Até nenhum informação do que está acontecendo. Vergonha :/














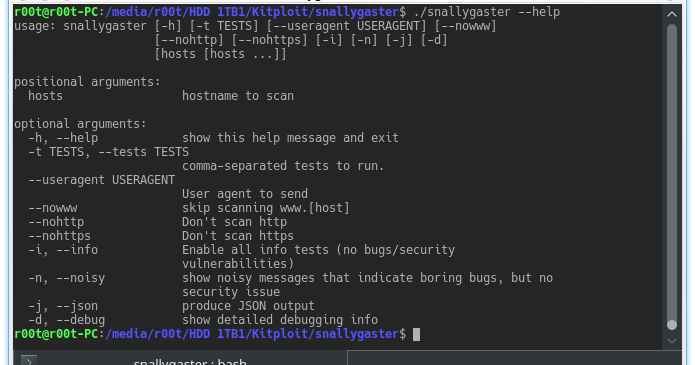
Snallygaster - Tool To Scan For Secret Files On HTTP Servers dlvr.it/QQsMnF ☣ KitPloit - Hacker Tools


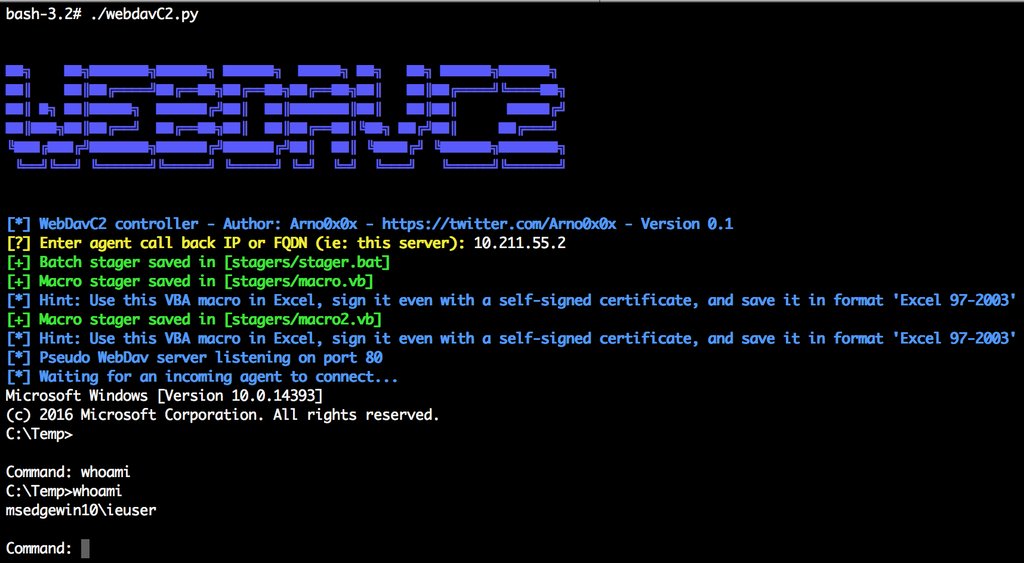
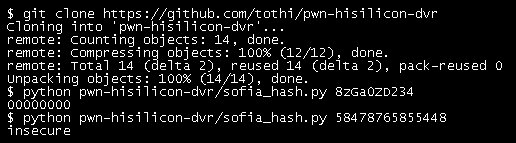
![Julio Della Flora (@jcldf) on Twitter photo Auto exploiter & get all server sites & bing dorker
Installation
git clone ift.tt/2GuzEAt
BadMod tool
Detect website cms & website scanner =&> Auto exploiter
Exploit :
[!] Wordpress
[+] joomla
[!] drupal
[+] Cms made simple
Video
Downloa… ift.tt/2pVsajt Auto exploiter & get all server sites & bing dorker
Installation
git clone ift.tt/2GuzEAt
BadMod tool
Detect website cms & website scanner =&> Auto exploiter
Exploit :
[!] Wordpress
[+] joomla
[!] drupal
[+] Cms made simple
Video
Downloa… ift.tt/2pVsajt](https://pbs.twimg.com/media/DZuc-xtXcAA7HR3.jpg)