Ismail
@ismailpy_crypto
ID: 1426689471278460931
14-08-2021 23:37:48
269 Tweet
29 Followers
334 Following







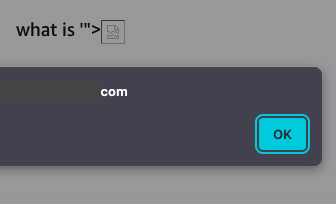
Insecure Direct Object Reference (IDOR) Checklist credit : sylvain prevost #bugbounty #bugbountytips #bughunting #penetrationtesting #pentesting #pentest #ethicalhacking #hacking #cybersecuritytips #cybersecurity #informationsecurity #infosec #bugcrowd #bugbountytips #bugbounty



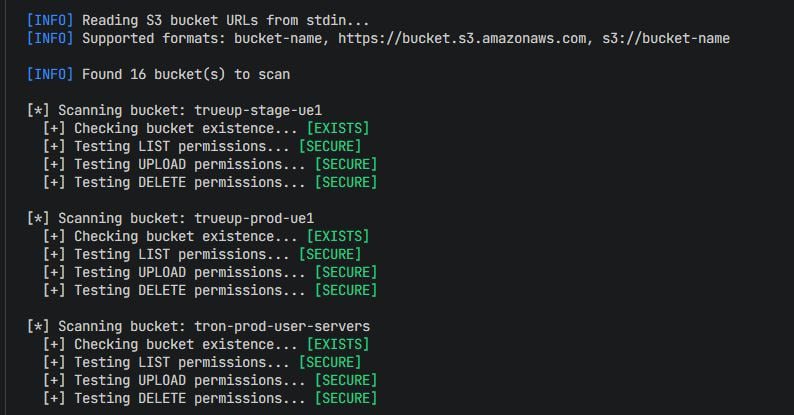
Find the origin servers of websites protected by Cloudflare, Sucuri, or Incapsula with a misconfigured DNS. ⚔️ - github.com/MrH0wl/Cloudma… Credit: Md Ismail Šojal 🕷️ #infosec #bugbountytips #Cybersecurity














![Dark Web Informer - Cyber Threat Intelligence (@darkwebinformer) on Twitter photo BreachForums has possibly returned at their original Onion address with what looks like it's original data.
I verified the Canary with the PGP and it is valid.
http://breached26tezcofqla4adzyn22notfqwcac7gpbrleg4usehljwkgqd[.]onion BreachForums has possibly returned at their original Onion address with what looks like it's original data.
I verified the Canary with the PGP and it is valid.
http://breached26tezcofqla4adzyn22notfqwcac7gpbrleg4usehljwkgqd[.]onion](https://pbs.twimg.com/media/GwuxFPsWoAA4NQd.jpg)