João Marques
@jcmarques15
ID: 2891590607
25-11-2014 02:45:08
329 Tweet
69 Followers
238 Following



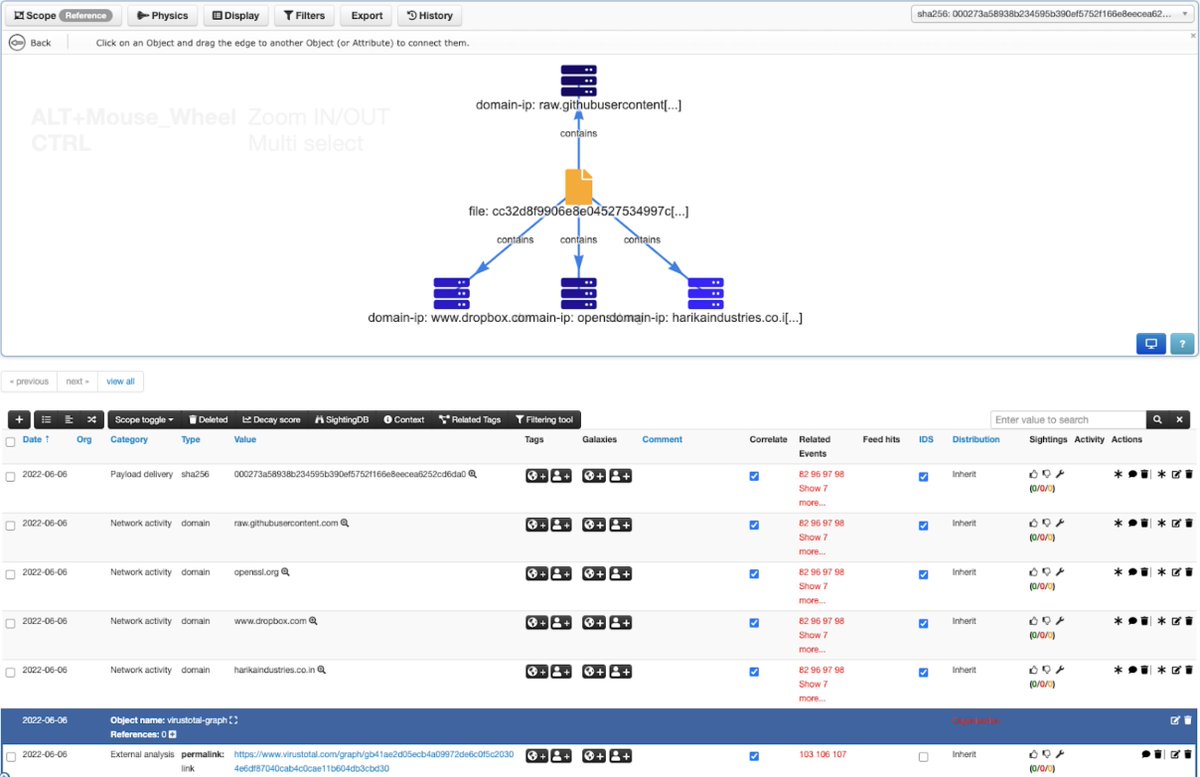
Good news for the MISP (@[email protected])'s user community! Now you can export your VT Graph into a MISP event (Download as>MISP Event) including all relationships and (optionally) the VT report for all the indicators.

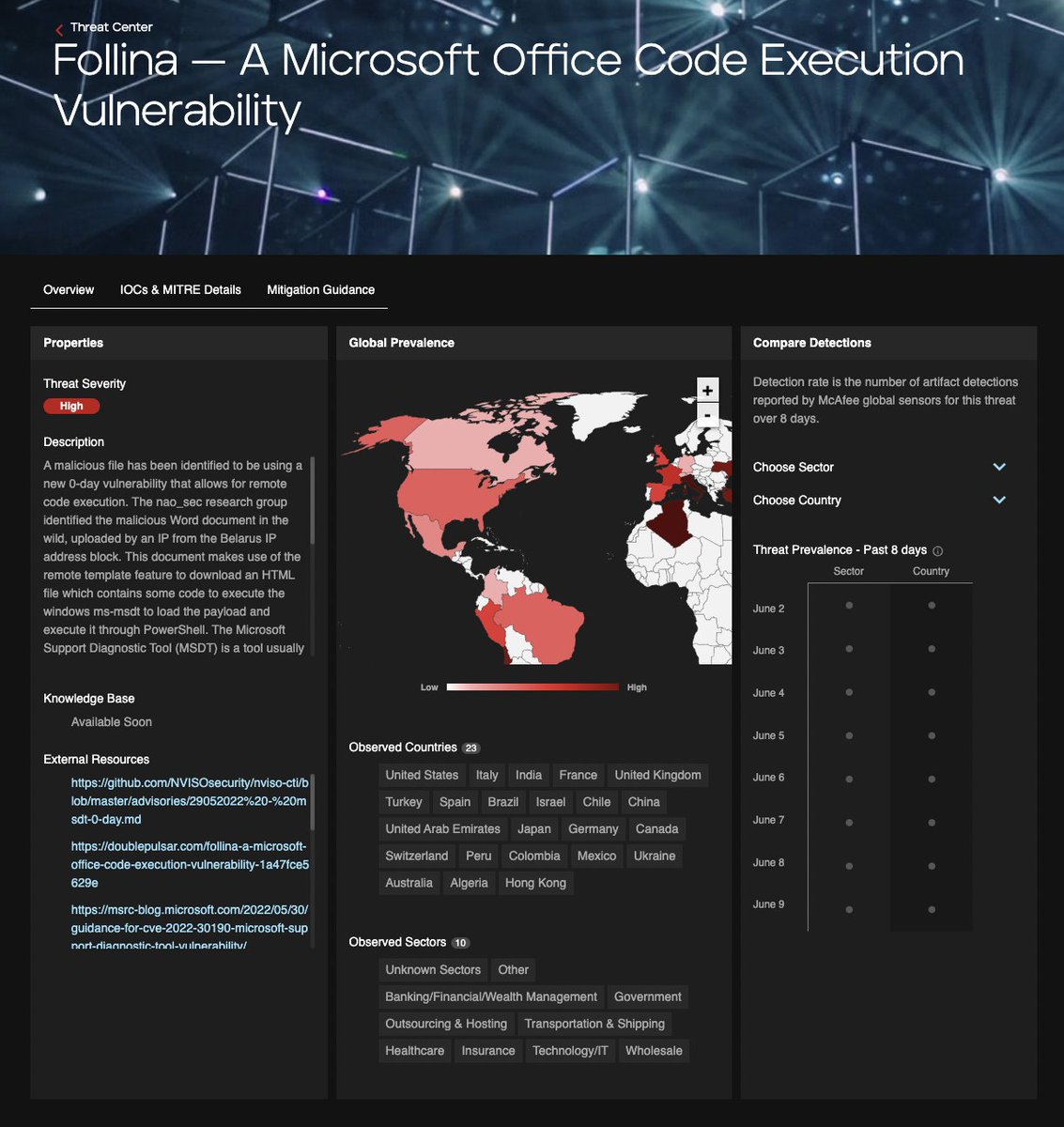
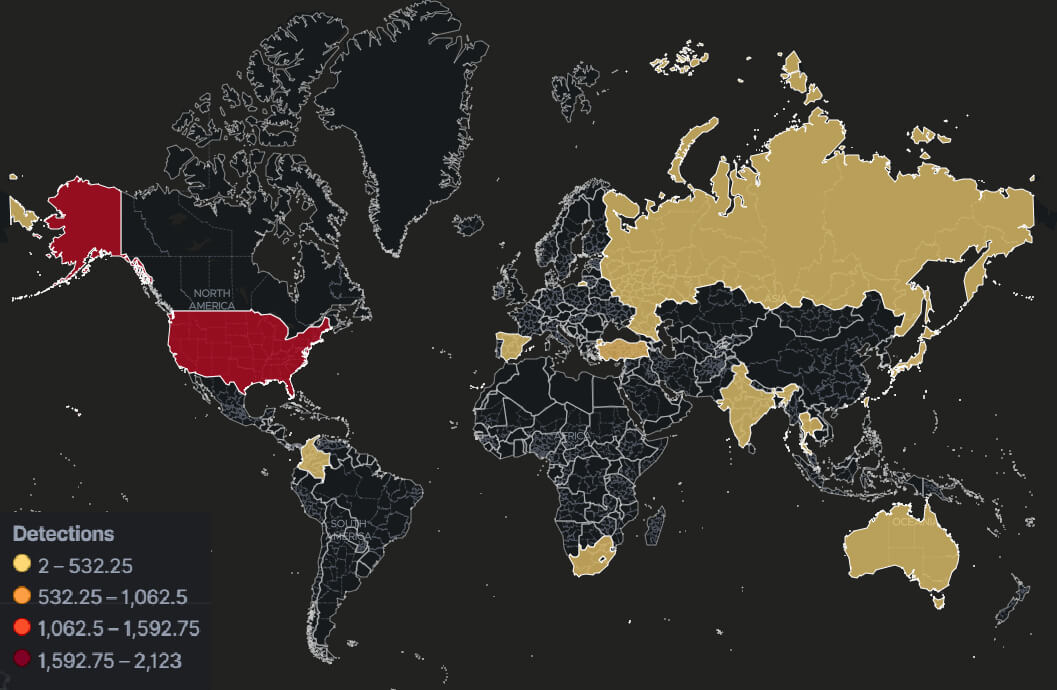
Exploitation of Follina — A Microsoft Office Code Execution Vulnerability appears to be hitting 23 countries, details/IoCs via @TrellixLabs trellix.com/en-us/threat-c… #cybersecurity #malware H/T Jeffrey Sman The Brofessor Alfred Alvarado Tim Hux John Fokker João Marques



Here’s her gofundme legal fund. Internet do your thing. Thanks to priyadesai for the find. gofundme.com/f/teen-arreste…

“Don’t focus on flashy visualization - choose the way that fits. We are not in a casino - sometimes a simple spreadsheet may be the best visualization of data. It needs to make sense for the user.” A reality check by John Fokker - Trellix Advanced Research Center during #cyberconf22




John Fokker, Alfred Alvarado, Tim Hux, Jeffrey Sman, & João Marques shared our take on the global ESXiArgs ransomware attack, exploiting CVE-2021-21974. More: bit.ly/3JViwXO


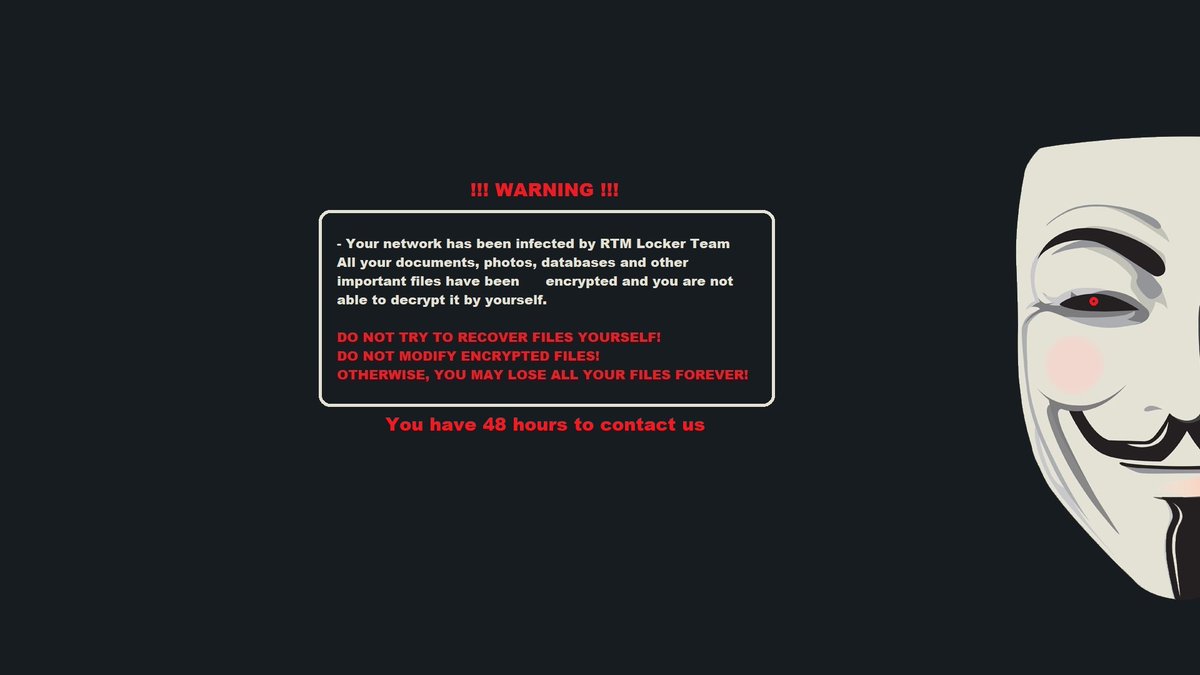
Malware Analyst Max 'Libra' Kersten provides a technical look at the “Read The Manual” (RTM) Locker gang, including a deep dive into their Windows ransomware executable, on the blog. bit.ly/3KrAnEo

Head of Threat Intelligence John Fokker shares our observations on cybercriminal behavior from over a year virtually staked out in the Genesis Marketplace — these insights ultimately assisted law enforcement in the market’s takedown. Hear more. bit.ly/43pvfsz

Despite takedown attempts in 2021, Emotet resurfaced, and threat actors continue to use it today. Trellix Advanced Research Center’s Adithya Chandra, João Marques, and Raghav Kapoor explore its evolution and current TTPs. Read to learn more. bit.ly/3PnExkI


In June, we debuted Ghidra scripts for analyzing Go-based malware. Max 'Libra' Kersten, in collaboration with Dorka Palotay, updated the scripts to now include: ➡️ Support for Golang 1.20 ➡️Support for MachO files ➡️Resolved to-do segments Find the scripts here: bit.ly/46Pd55d

Over two years, our team analyzed & enhanced threat intelligence for Operation Morpheus. Learn about the data we shared with law enforcement to assist in the dismantling of Cobalt Strike's infrastructure from John Fokker, joao marcelo, & Leandro Velasco. bit.ly/4cOOYpZ