Jonas Bülow Knudsen
@jonas_b_k
Manager, Research @ SpecterOps
ID: 2926704915
https://github.com/JonasBK 17-12-2014 10:20:29
709 Tweet
1,1K Followers
424 Following





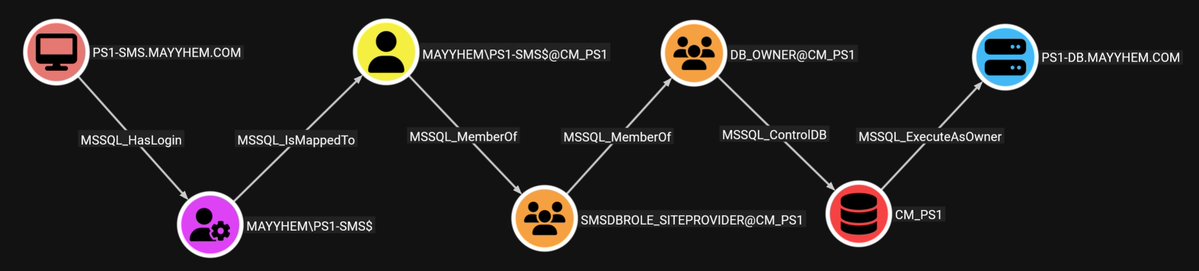
MSSQLHound leverages BloodHound's OpenGraph to visualize MSSQL attack paths with 7 new nodes & 37 new edges, all without touching the SharpHound & BloodHound codebases. Chris Thompson unpacks this new feature in his blog post. 👇 ghst.ly/4leRFFn

The AD CS security landscape keeps evolving, and so does our tooling. 🛠️ Valdemar Carøe drops info on Certify 2.0, including a suite of new capabilities and refined usability improvements. ghst.ly/45IrBxI



Don't forget to grab your BloodHound 8.0 t-shirt! Everything raised from this fundraiser will support Hope for HIE ☀️, the global voice for families affected by Hypoxic Ischemic Encephalopathy. ➡️ ghst.ly/bh8-tshirt


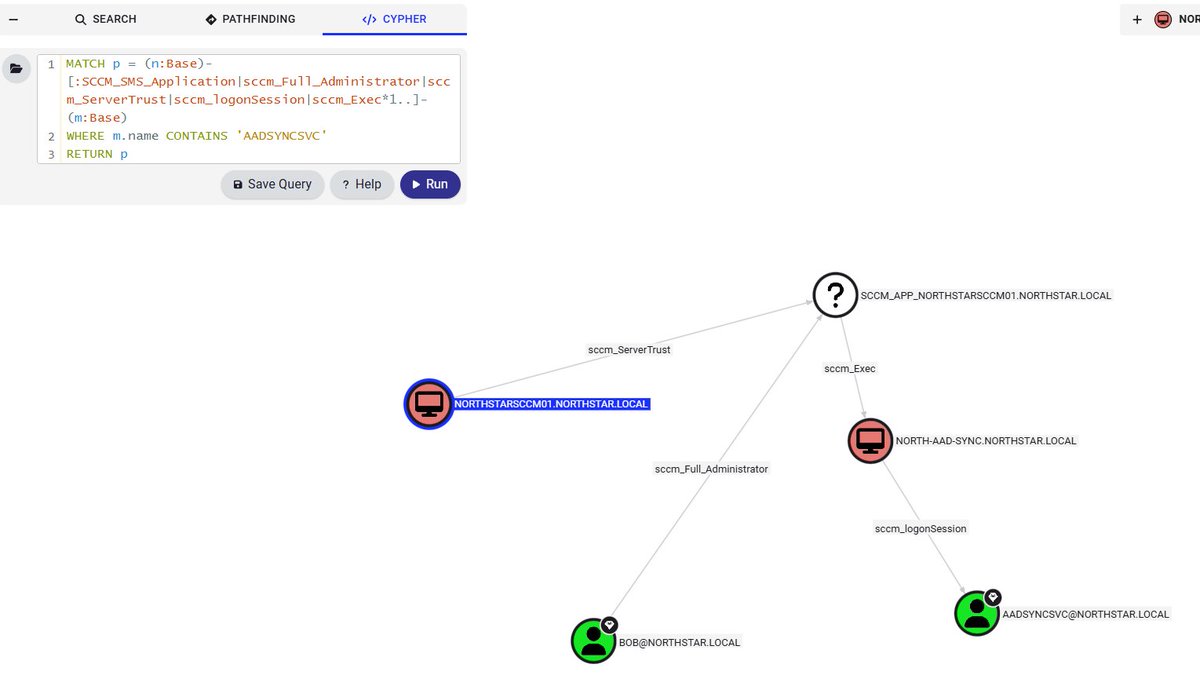
BloodHound isn't just for Active Directory anymore. 🤯 Walter.Legowski dives into the BloodHound OpenGraph functionality & demonstrates the new PowerShell cmdlets added to the BloodHound Operator module to work with the OpenGraph feature. ghst.ly/4peTTrB


Excited to present with Matt Johnson at #BHEU Black Hat where we'll be sharing our research on attacking System Center Operations Manager! SpecterOps





Lateral movement getting blocked by traditional methods? werdhaihai just dropped research on a new lateral movement technique using Windows Installer Custom Action Server, complete with working BOF code. ghst.ly/4pN03PG


Certificate-based privilege escalation vulnerabilities are the attack vector enterprises keep overlooking. Join Emily Leidy at #BSidesNYC on Oct. 18 to learn a structured approach to ADCS remediation using attack path analysis and BloodHound Enterprise. ghst.ly/3J0BxKt


EPA can shut down NTLM relay attacks, but there's no public way to enumerate enforcement across protocols like MSSQL & HTTP. The solution? RelayInformer. Join Nick Powers & Matt Creel on Oct. 30 as they discuss the tool & their research: ghst.ly/web-oct-tw


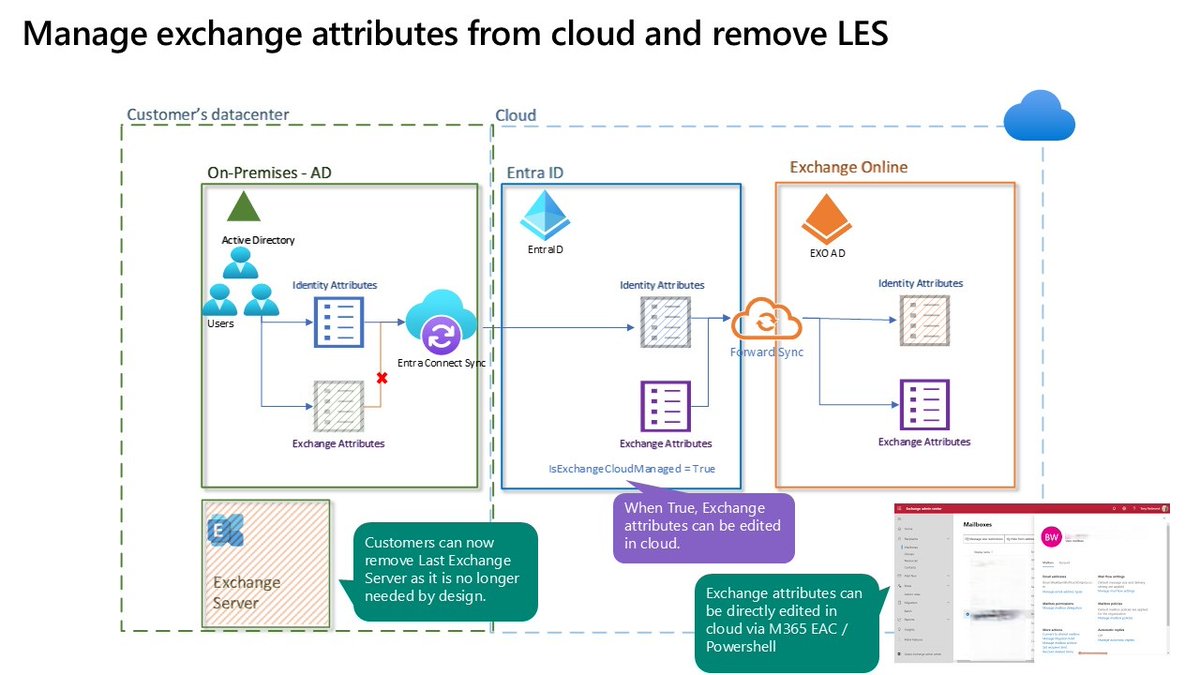
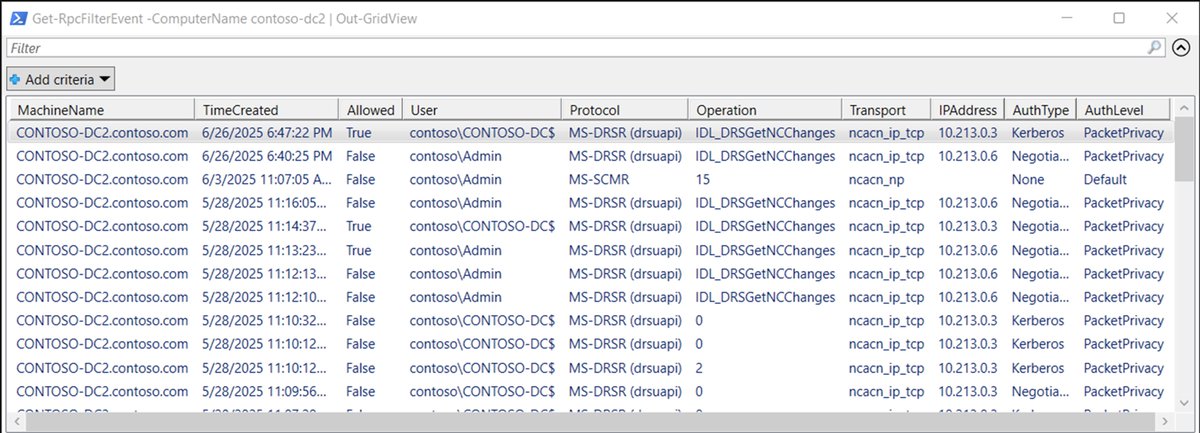
Credential Guard was supposed to end credential dumping. It didn't. Valdemar Carøe just dropped a new blog post detailing techniques for extracting credentials on fully patched Windows 11 & Server 2025 with modern protections enabled. Read for more ⤵️ ghst.ly/4qtl2rm