Ladislav Zezula
@ladislavzezula
Reverse Engineer, Malware Analyst and Toolmaker at @AVAST
ID: 157597270
http://www.zezula.net 20-06-2010 08:22:13
153 Tweet
713 Followers
118 Following


#Retadup #worm taken down by Avast Threat Labs and Gendarmerie nationale #C3N ✔️decoded.avast.io/janvojtesek/pu…







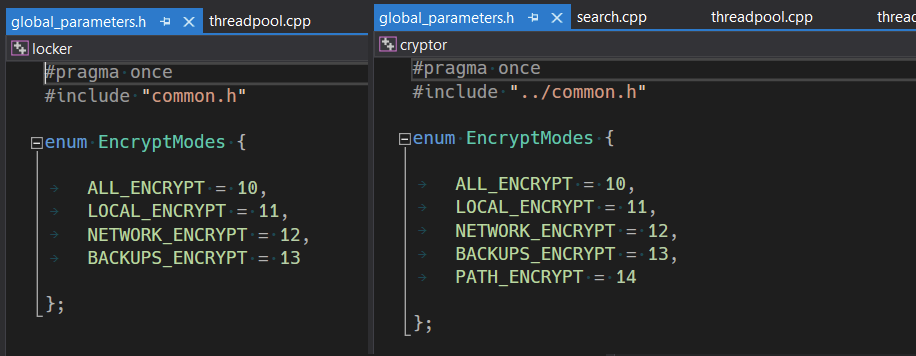
While the sources published by conti leaks yesterday are indeed newer than those published before (see picture), they still don't correspond to the binaries that I see today.







In cooperation with Cisco Talos Intelligence Group and Dutch Politie Nederland 🇳🇱, Avast is releasing an updated version of the Avast #Babuk #ransomware decryption tool, capable of restoring files encrypted by the #Babuk variant called #Tortilla. Details on decoded.avast.io/threatresearch….