Netwrix
@netwrix
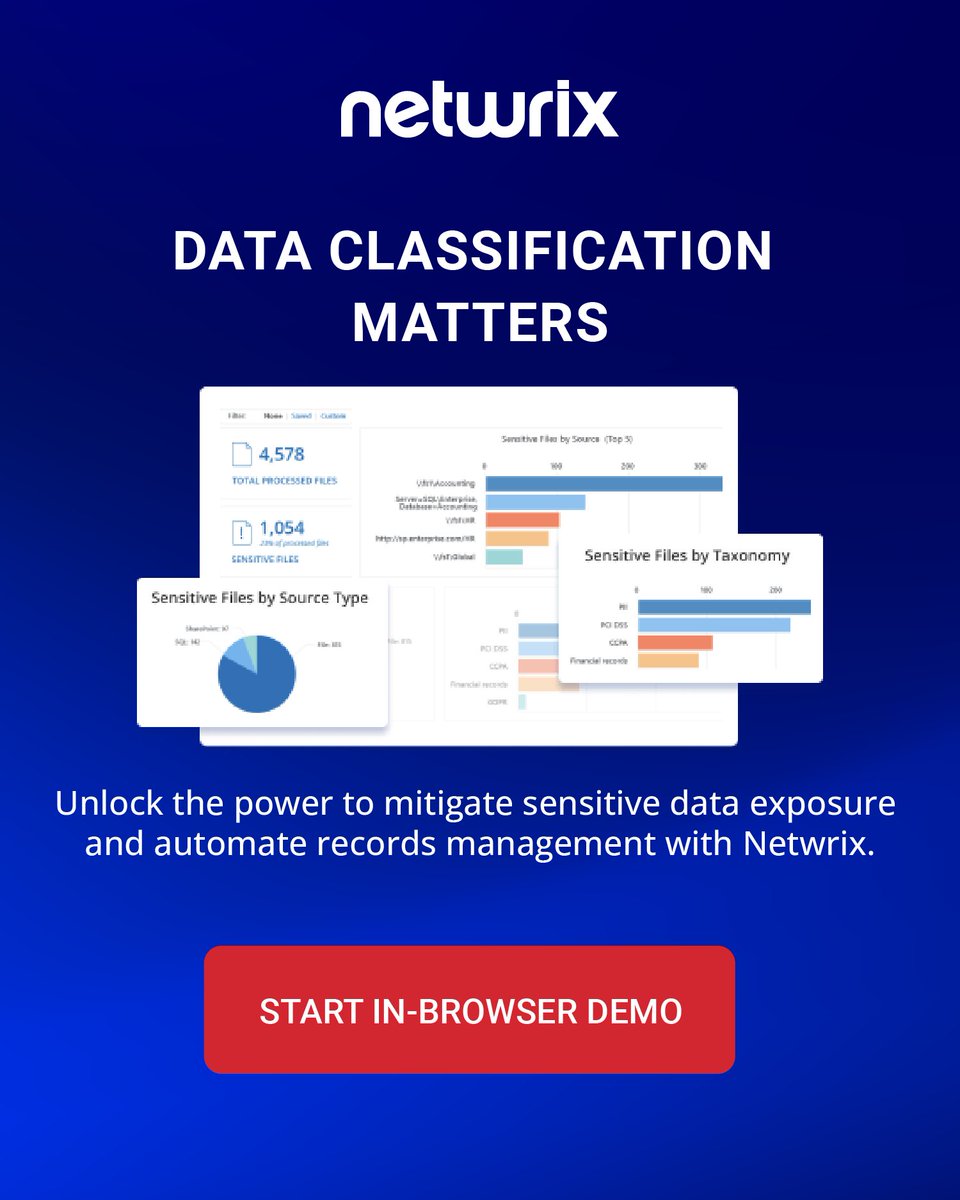
Netwrix enables security pros to identify & protect sensitive data and detect, respond to, & recover from attacks.
ID: 32118187
https://www.netwrix.com 16-04-2009 19:17:58
4,4K Tweet
2,2K Followers
323 Following















The biggest threats aren’t always obvious. Business logic flaws hide in plain sight—spotting them takes connecting insights across identities, data & infrastructure. Dirk Schrader explains why in Dark Reading Read here: darkreading.com/vulnerabilitie…