
nohehf
@nohehf
security, software, engineering, experimentations & fun @ escape . tech
ID: 1602855410
18-07-2013 07:50:49
325 Tweet
99 Followers
300 Following






I’ll be talking tomorrow apidays Global Paris 🔥

Interesting session by Tristan Kalos & Antoine Carossio "GraphQL Security Vulnerabilities In The Wild" at apidays Global Paris! #ApiDays #GraphQL #ApiDaysParis










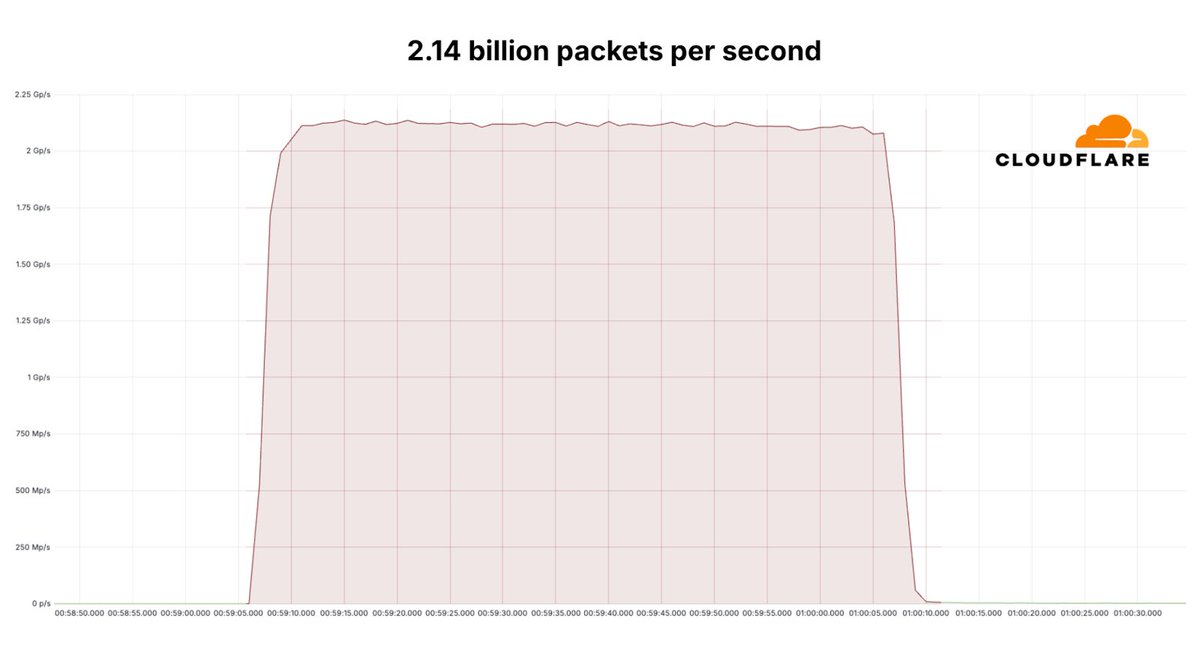
Not all records you’re happy about breaking: Cloudflare recently mitigated the largest ever reported hyper-volumetric #DDoS attack. 3.8 terabits per second (Tbps) and 2.14 billion packets per second (Bpps). Handled automatically any without any customer impact. Details to come.





![ludwig (@ludwigabap) on Twitter photo This is the biggest mindset issue that many, many devs suffer from imo.
"Why would you roll your own lib? Just [popular lib instead]"
"Why are you building your own game engine? Use Unity/Godot"
"Rolling your own JS frameowrk? Just use React bro."
"Why would you write your own This is the biggest mindset issue that many, many devs suffer from imo.
"Why would you roll your own lib? Just [popular lib instead]"
"Why are you building your own game engine? Use Unity/Godot"
"Rolling your own JS frameowrk? Just use React bro."
"Why would you write your own](https://pbs.twimg.com/media/GNXwZT0WEAEzGTH.png)

