S̀͆̚h͂ͬ͆̇̋̍̒e͐ͬͤ͑͂ͯ̌lͦdo̓̄̆n̄̋ͦ̍ͦ̏
@poppa_shell
Christ Follower | Husband | Father | InfoSec Nerd | Beard Enthusiast | ESTJ | GSEC, GPEN, CISSP | Co-Host @DCG940 | @hacknotcrime Advocate
ID: 30004536
09-04-2009 15:28:37
2,2K Tweet
994 Followers
1,1K Following

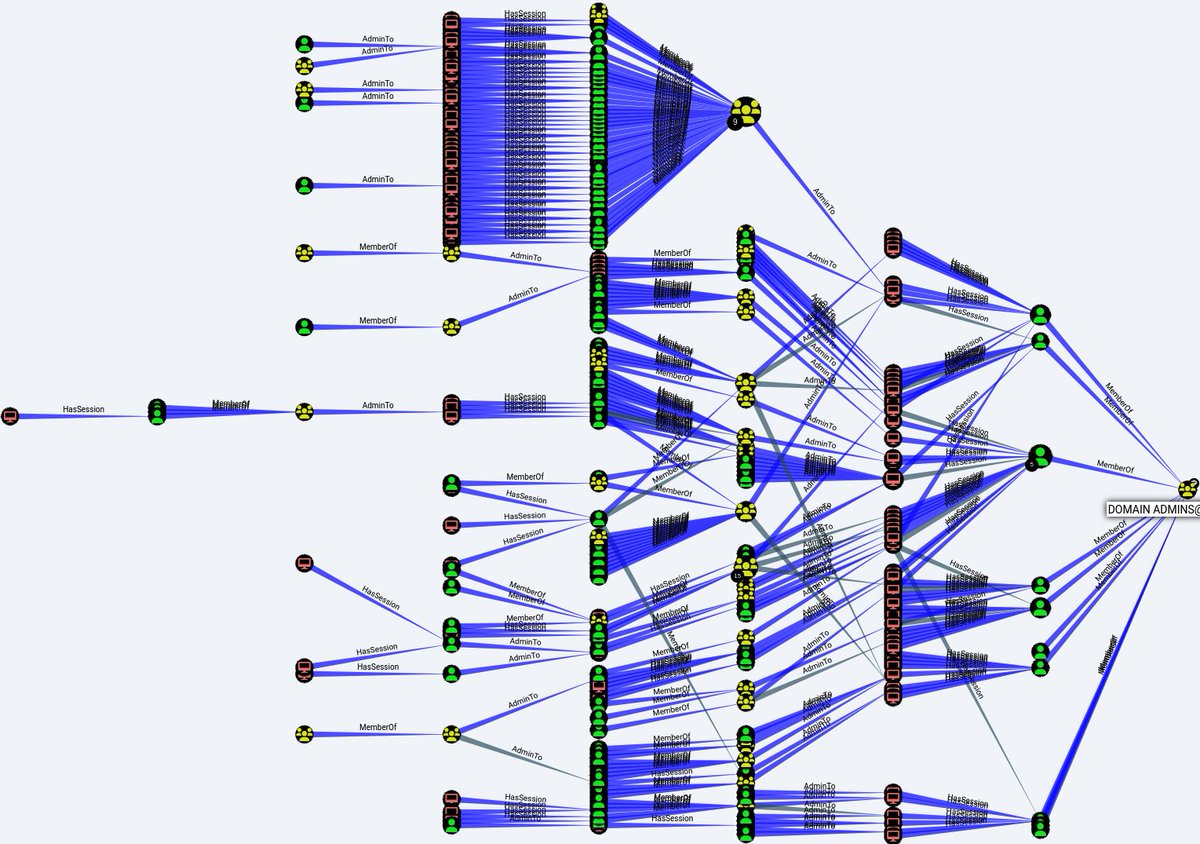
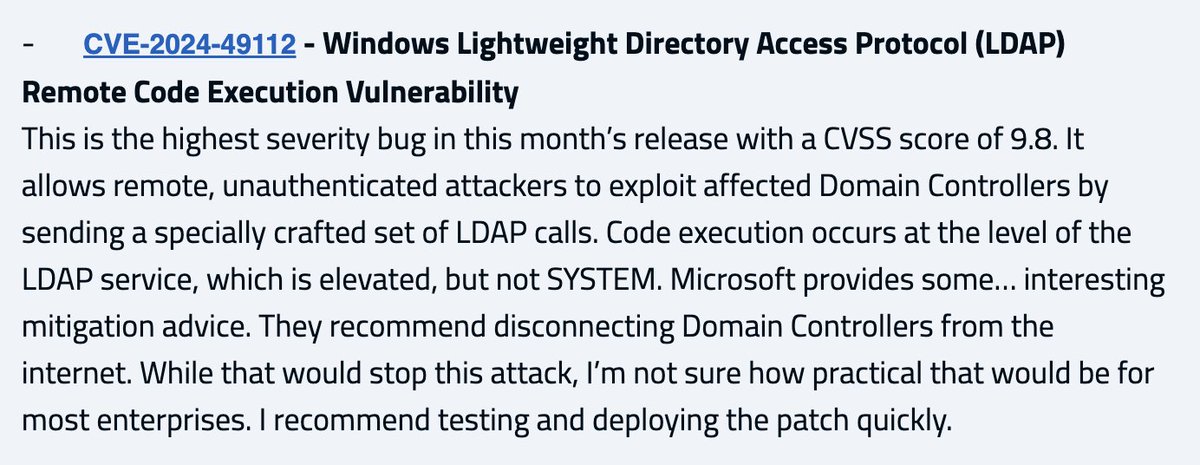
Unauthenticated Remote Code Execution (RCE) on Domain Controllers (DC). It does not get worse than that. Probably will be included in #ransomware campaigns. Any technical analysis of CVE-2024-49112 published? CC: 🥝🏳️🌈 Benjamin Delpy Will Schroeder Andy Robbins






Ross Ulbricht When you're feeling up for it, I'd love to sit down with you for an interview. But get some rest, catch your breath, and let the reality sink in for a while. Enjoy yourself.




What an awesome merge/acquisition! TrustedSec is already an awesome company. And bringing on Sean Metcalf & Trimarc is a huge flex! Congrats Dave Kennedy.




Thanks to Black Hills Information Security for the free Backdoors & Breaches set w/ 20-sided dice at B-Sides Tampa IT Security Conference! Snagged this set to give away at a future DC940 meet.


Truly humbled to share I had the honor of being a guest on the legendary Darknet Diaries. We talked about some wild stories, the epic screw ups, and others adventures. Really grateful for the chance to tell a few tales and hope it resonates with some darknetdiaries.com/episode/160/