qu35t
@qu35t_tv
Pentester @vaadata 💻 - #Exegol maintainer - @GoToolSharing owner - Bug Hunter - #BSCP #CBBH #CPTS #CRTO #CRTP #Dante #Offshore
ID: 1283540441938501632
https://bento.me/qu35t 15-07-2020 23:14:35
804 Tweet
694 Followers
867 Following


















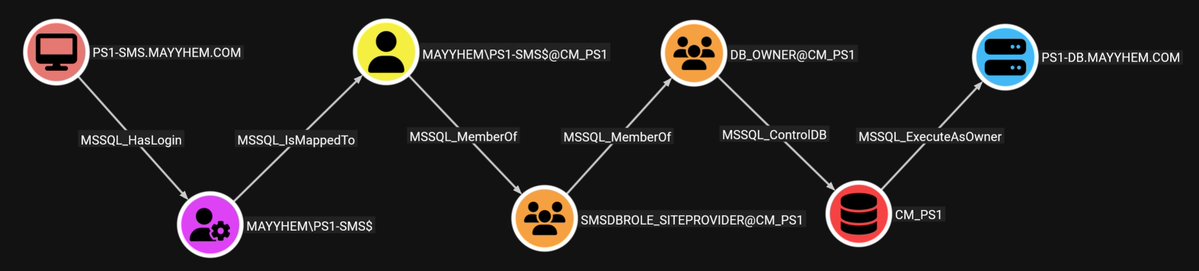
Some weeks ago, TrustedSec has posted a really interesting blog post about the MDT shares, and credentials that can be found inside. But one question remained unanswered: where are they? I have tried to answer this question: hideandsec.sh/books/windows-…