Richard Zhu
@rz_fluorescence
ID: 842856569444302848
17-03-2017 21:54:00
17 Tweet
5,5K Followers
37 Following


Confirmed! Our 1st attempt at #Pwn2Own Tokyo becomes our 1st successful entry. fluoroacetate (Amat Cama and Richard Zhu) used an out-of-bounds write in WebAssembly to get code execution via NFC on the #Xiaomi Mi6. They earn $30K USD and 6 Master of Pwn points!

Confirmed! The team of fluoroacetate successfully got code execution by using a heap overflow in the baseband component. The exploit earns them $50,000 USD and 15 more Master of Pwn points.

Confirmed! The dynamic fluoroacetate duo used a JIT bug followed by an Out-Of-Bounds write to get code execution on the #iPhoneX. They earned themselves an additional $60K and 10 more Master of Pwn points.

Confirmed! The fluoroacetate duo combined a bug in JIT with an Out-Of-Bounds Access to exfiltrate data from the iPhone. In the demo, they grabbed a previously deleted photo. In doing so, they earn themselves $50K and 8 Master of Pwn points. #P2OTokyo

Confirmed! The fluoroacetate duo used an integer overflow in the JavaScript engine of the #Xiaomi web browser to exfiltrate a picture from the phone. They earn $25K and 6 Master of Pwn points.

That brings to an end #Pwn2Own Tokyo 2018! Congrats to team fluoroacetate on earning 45 points and being crowned Master of Pwn! #P2OTokyo


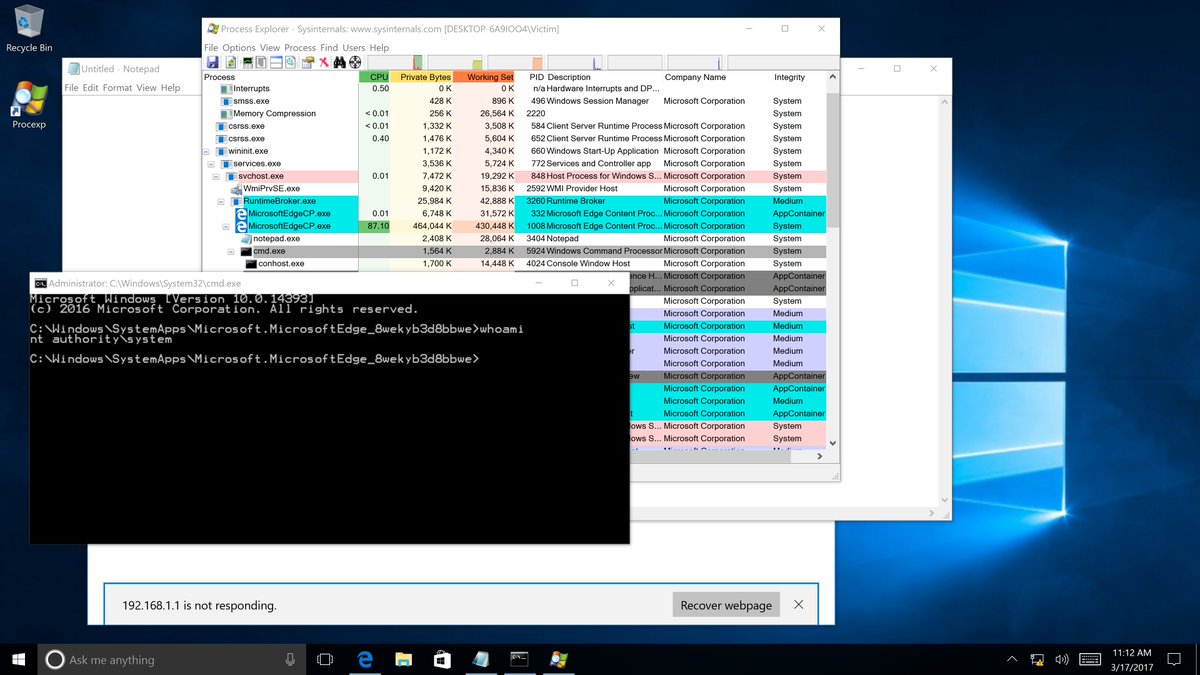
The fluoroacetate duo does it again. They used a type confusion in #Edge, a race condition in the kernel, then an out-of-bounds write in #VMware to go from a browser in a virtual client to executing code on the host OS. They earn $130K plus 13 Master of Pwn points.



That's a wrap! Congrats to fluoroacetate on winning Master of Pwn. There total was $375,000 (plus a vehicle) for the week. Superb work from this great duo.




Confirmed! After plenty of drama -including reworking his exploit live, on the clock, in front of a crowd- Richard Zhu used 2 UAFs in Edge and an integer overflow in the kernel to win $70,000 and 7 points towards Master of Pwn. #Pwn2Own

Boom! No drama for Richard Zhu today as he takes down FireFox on his first attempt. Now off to the disclosure room for confirmation and vendor notification.
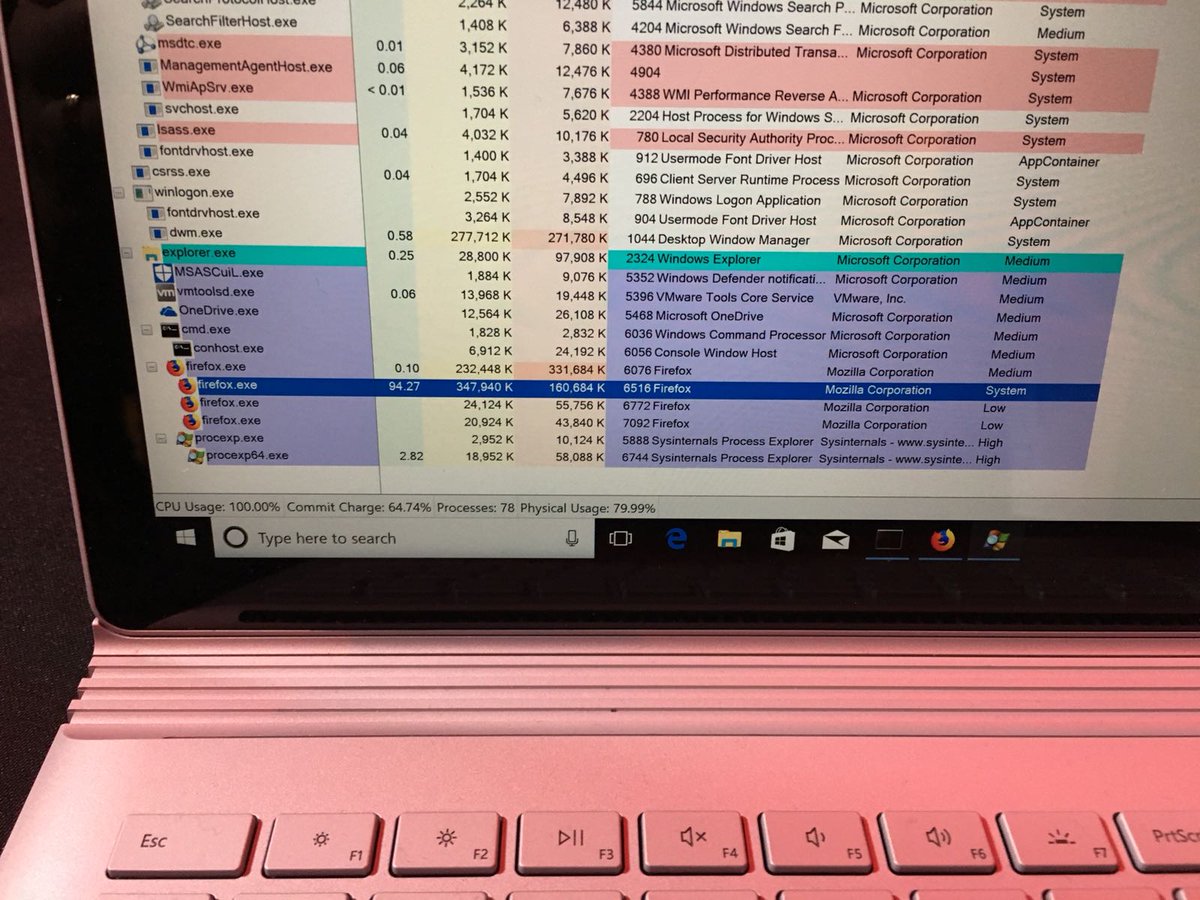

Confirmed! Richard Zhu used an OOB write in the browser & an integer overflow in the Windows kernel to pop #FireFox and execute his code w/ elevated privileges. Earns $50K & 5 Master of Pwn points. His event total is now $120,000.

Congrats to Richard Zhu on being named Master of Pwn for #Pwn2Own 2018! His exploits for Edge and Firefox earned him $120,000, this sweet jacket, and the trophy. We hope he returns in the future to defend his title.