SecureYeti
@secureyeti
ID: 1057341892738854914
30-10-2018 18:42:06
70 Tweet
209 Followers
5 Following



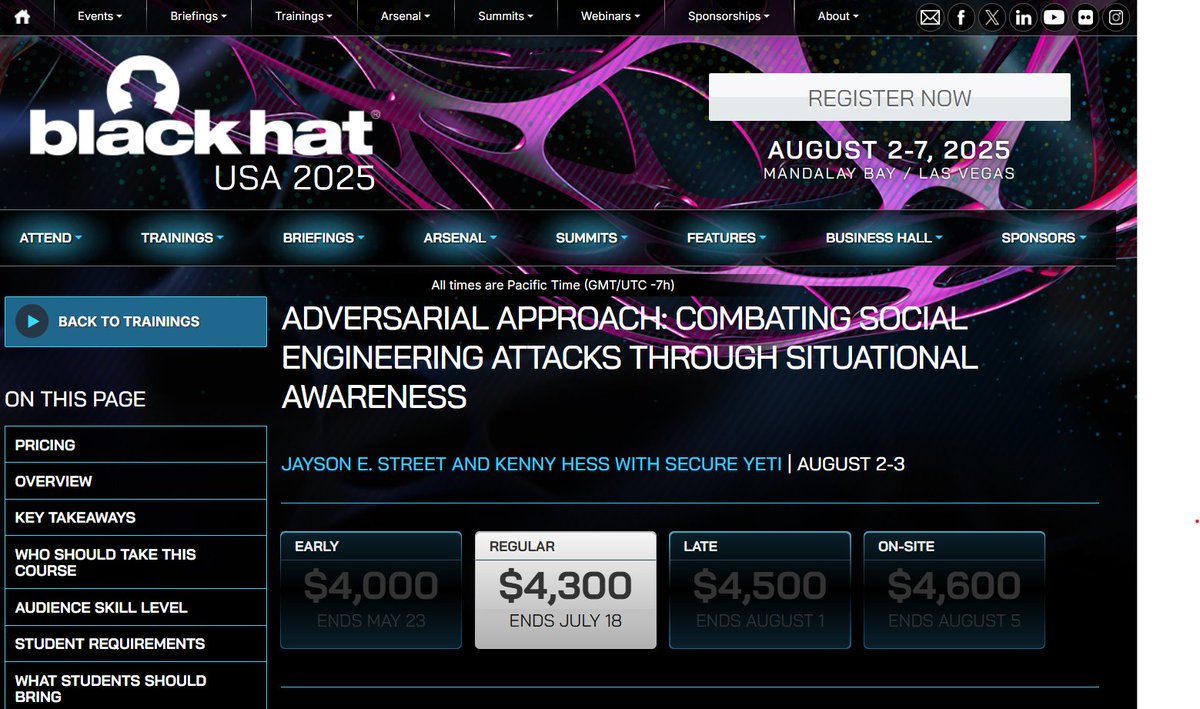
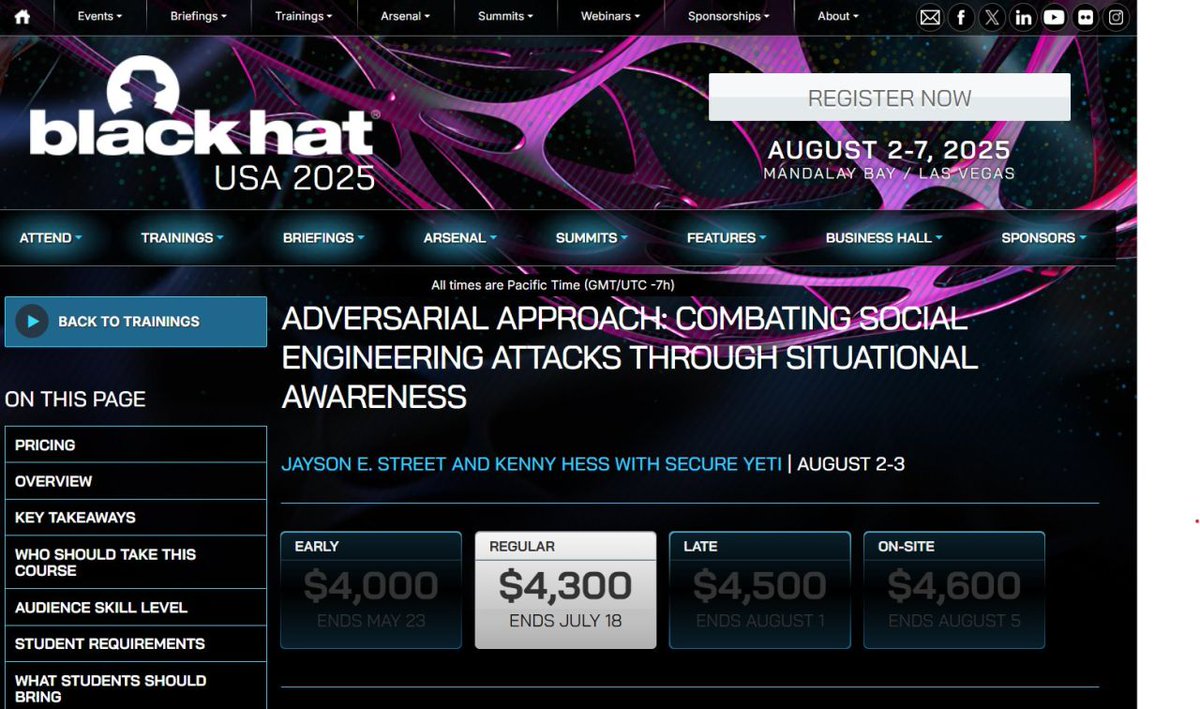
Listen to this #Infosec2025 interview with Jayson E. Street 💙 🤗💛, Chief Adversarial Officer at Secure Yeti, and hear his insights on the evolving landscape of social engineering attacks -- including the integration of artificial intelligence (AI) by threat actors. loom.ly/MpqtAhQ



Ever wanted to unleash your inner “bad guy” in a legal and controlled setting? Learn tactics from Adversary for Hire Jayson E. Street 💙 🤗💛, one of the most twisted minds in the industry, to think and attack like an adversary! Register today at loom.ly/JvnLc-Q #defcon




Ever wanted to unleash your inner “bad guy” in a legal and controlled setting? Learn tactics from Adversary for Hire Jayson E. Street 💙 🤗💛, one of the most twisted minds in the industry, to think and attack like an adversary! Register today at training.defcon.org/lasvegas2025 #defcon



Ever wanted to unleash your inner “bad guy” in a legal and controlled setting? Learn tactics from Adversary for Hire Jayson E. Street 💙 🤗💛, one of the most twisted minds in the industry, to think and attack like an adversary! Register today at loom.ly/JvnLc-Q #defcon





Ever wanted to unleash your inner “bad guy” in a legal and controlled setting? Learn tactics from Adversary for Hire Jayson E. Street 💙 🤗💛, one of the most twisted minds in the industry, to think and attack like an adversary! Register today at zurl.co/Vcdsv #defcon


We hadn’t heard from Jayson E. Street 💙 🤗💛 in a while, then he sent us this. We have no idea where he is right now, but we know where he’ll be soon! See him at Black Hat and DEF CON: tinyurl.com/3tk8b3rh #BHUSA tinyurl.com/y6zfn6w6 #defcon #defcontraining

Ever wanted to unleash your inner “bad guy” in a legal and controlled setting? Learn tactics from Adversary for Hire Jayson E. Street 💙 🤗💛, one of the most twisted minds in the industry, to think and attack like an adversary! Register today at zurl.co/at3PK #defcon




Ever wanted to unleash your inner “bad guy” in a legal and controlled setting? Learn tactics from Adversary for Hire Jayson E. Street 💙 🤗💛, one of the most twisted minds in the industry, to think and attack like an adversary! Register today at zurl.co/rpBWj #defcon