
SlowMist
@slowmist_team
SlowMist is a Blockchain security firm established in 2018, providing services such as security audits, security consultants, red teaming, and more.
ID: 988385053800517632
https://www.slowmist.com/ 23-04-2018 11:52:14
3,3K Tweet
87,87K Followers
406 Following








👏We’re excited to announce that Haust Network has successfully passed a comprehensive security audit of the Haust Wallet mobile application! Thanks for prioritizing user safety and choosing us as your audit partner. 🤝 Together, we’re making crypto safer.🛡️🚀


🚨SlowMist Security Alert🚨 We detected potential suspicious activity related to Cork Protocol. As always, stay vigilant!
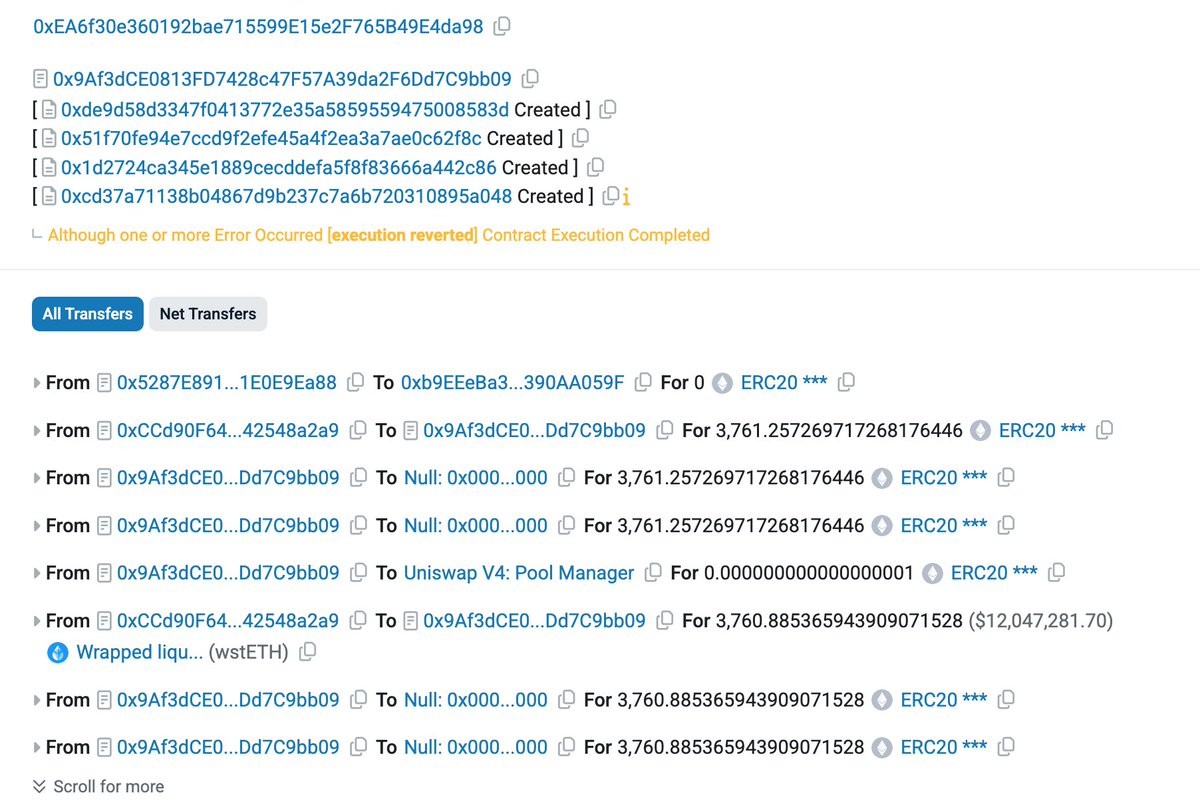

🚨Sometimes, solutions or tools that claim to enhance “security” may actually exploit the user’s trust to launch attacks. Today, 0x猫宁 | Crypto & AI reached out to the SlowMist Security Team after spotting phishing behavior in the browser extension Osiris. Our deep dive revealed this


🎉 SlowMist x Foresight News Dragon Boat Festival Giveaway 🎉 Your mnemonic phrase is the lifeline of your crypto — keep it safe, keep it in mind. 🧠⛓️ Foresight News just dropped a cool new collectible, we're giving away 3 to the community! To enter: 1⃣ Follow










