SummoningTeam
@summoningteam
Independent Security Research Team managed by @SinSinology
ID: 1586289923992207360
https://summoning.team 29-10-2022 09:33:01
89 Tweet
564 Followers
2 Following

#RomHack2025 #Training we’re hosting Advanced .NET #Exploitation Training with SinSinology Instead of spending 8 months of your time, you will be up to date with the latest tools, techniques, tactics, and procedures in just 4 days! romhack.io/training/2025/…




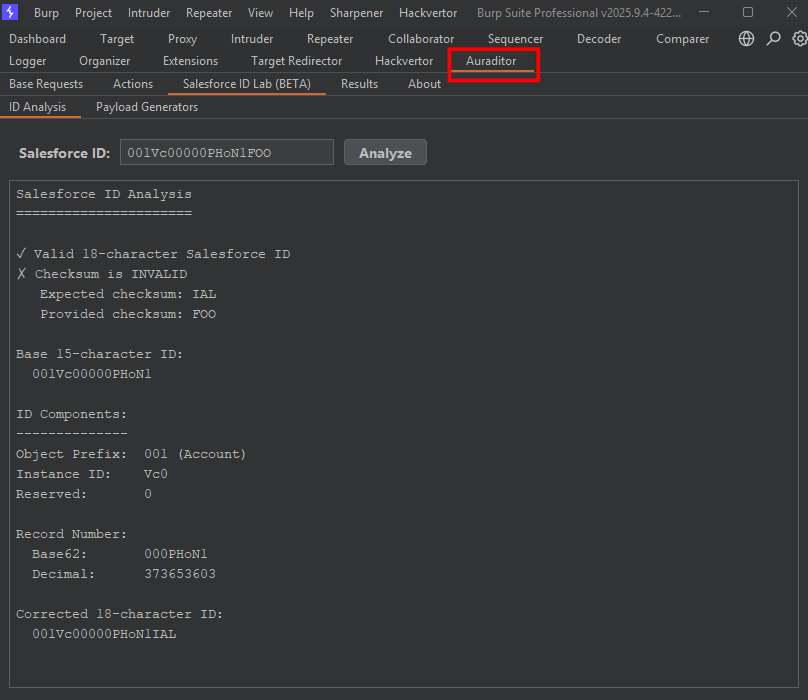
[ZDI-25-628|CVE-2025-25271] (Pwn2Own) Phoenix Contact CHARX SEC-3150 OCPP Authentication Bypass Vulnerability (CVSS 3.1; Credit: Sina Kheirkhah (SinSinology) of Summoning Team (SummoningTeam)) zerodayinitiative.com/advisories/ZDI…

(^-^) Don't rush, 4 seats left for "Advanced .NET Exploitation" September edition at RomHack 2025 (Cyber Saiyan | RomHack Conference, Training, Camp) summoning.team


only 3 seats left for the "Advanced .NET Exploitation" September edition at RomHack (Cyber Saiyan | RomHack Conference, Training, Camp), come on lads, make it happen, wanna go brag about selling out 😅 grab your seat 🪑 🪑 🪑 summoning.team

It’s happening today Advanced .NET Exploitation hosted by Sina Kheirkhah - Pwn2Own "Master of Pwn" (SinSinology - x.com/SinSinology) 🔥🔥🔥 #workshop #BSidesTirana #PyramidofTirana



Spent the weekend teaching my "Basic .NET Exploitation workshop" at BSides Tirana (BSides Tirana), and wow, what an experience! Massive shoutout to Rio (Rio) & Paulina (Paulina Cakalli ) for organizing hands-down the best BSides I've ever been part of 💜🔥 Here are some of


Amazing workshop SinSinology 🚀🎉🙌

Getting feedback like this makes it all worth it! 💜 Just finished teaching 4 days (32 hrs) of "Advanced .NET Exploitation" at RomHack (Cyber Saiyan | RomHack Conference, Training, Camp) 15 brilliant students, 16 CVEs, and plenty of pop-calc moments. See you in the next one... (to be anounced)


Thanks SinSinology for the .NET exploitation training! Appreciate the effort you put into the slides, lab-guide and the VM! It was great fun and I loved the fact that it had plenty of real world targets/CVEs.

SinSinology thank you so much for the .NET advanced exploitation training.. you gave a lot of awesome insights and tricks, I would recommend it to everyone that is interested in taking their exploitation skills to the next level!



Seconds to spare and $40,000 on the line: SinSinology of SummoningTeam and the @theZDI team celebrate his successful exploit of Synology DiskStation DS925+ in the Network Attached Storage category at Pwn2Own Ireland. trendmicro.com/en_us/zero-day… #Pwn2Own

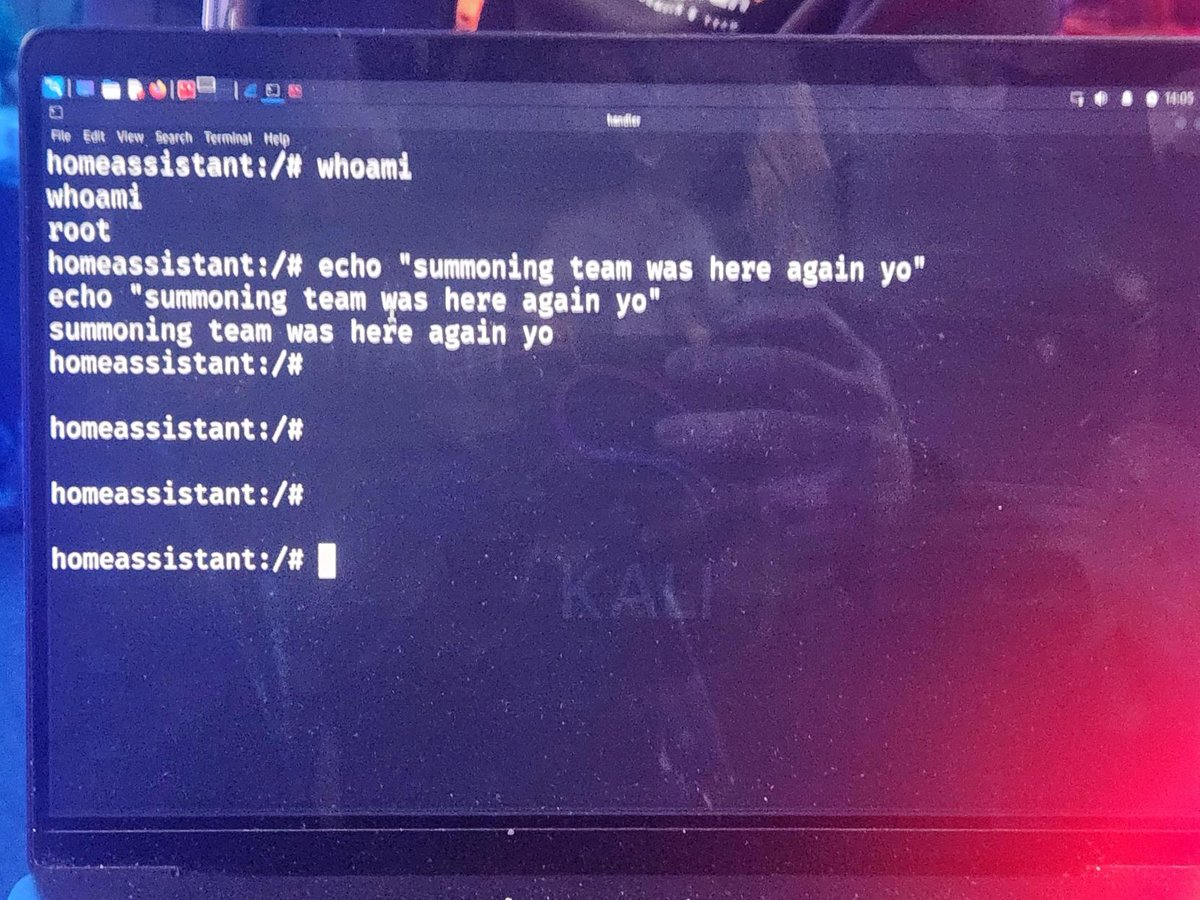
🏡 McCaulay Hudson (McCaulay) of SummoningTeam just cracked Home Assistant Green wide open! (and it still isn't green) Smart homes beware. He's off to the disclosure room to explain himself. #Pwn2Own