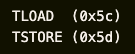Thomas Xu
@thomas_xu29
Smart Contract Auditor/Developer
ID: 1580941446022324224
14-10-2022 15:19:56
31 Tweet
13 Followers
87 Following













. TheStandard.io was exploited due to the lack of slippage protection when swapping out the collateral, and the loss is ~$290K. The attacker first created a CDP (SmartVaultV2) with 10 WBTC as collateral to mint 290,000 EUROs. Subsequently, the attacker forced the SmartVaultV2





⚡️Proud to share our research on Salus Lightning Cat, a smart contract audit tool, is featured in Scientific Reports, a prestigious scientific publication by Nature Portfolio. Explore deep learning and smart contract security in our work in the Nature Journal. nature.com/articles/s4159…