Threatscape
@threatscape
#CyberSecurity solutions that perform at scale. We secure your critical IT assets at endpoints, across networks, and in the cloud.
ID: 182836368
https://www.threatscape.com/ 25-08-2010 14:27:30
266 Tweet
598 Followers
1,1K Following






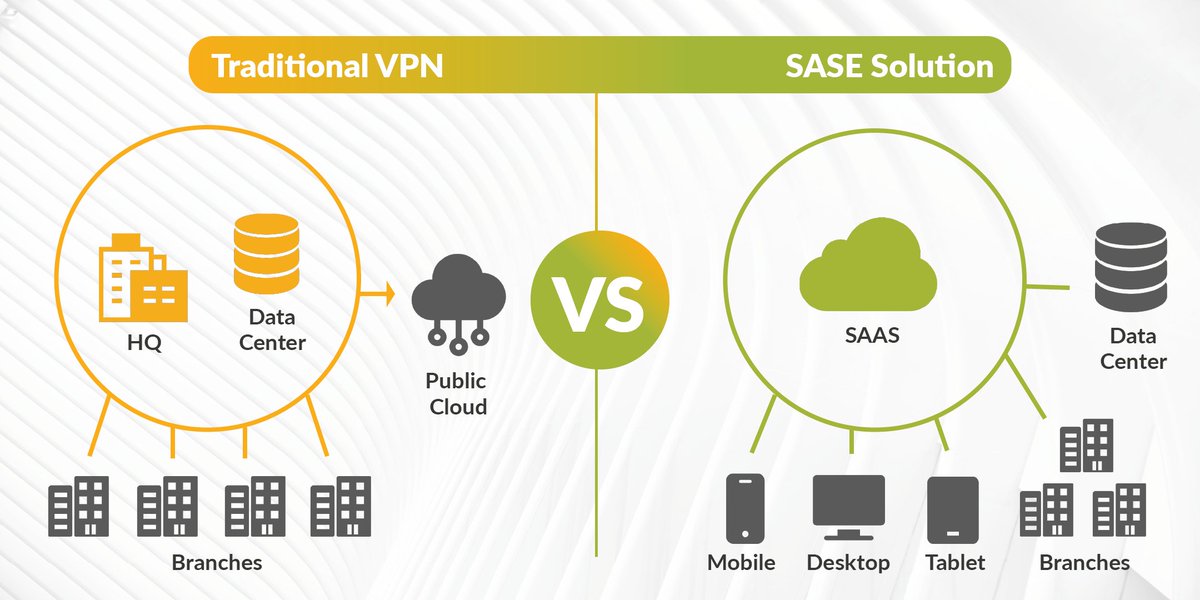
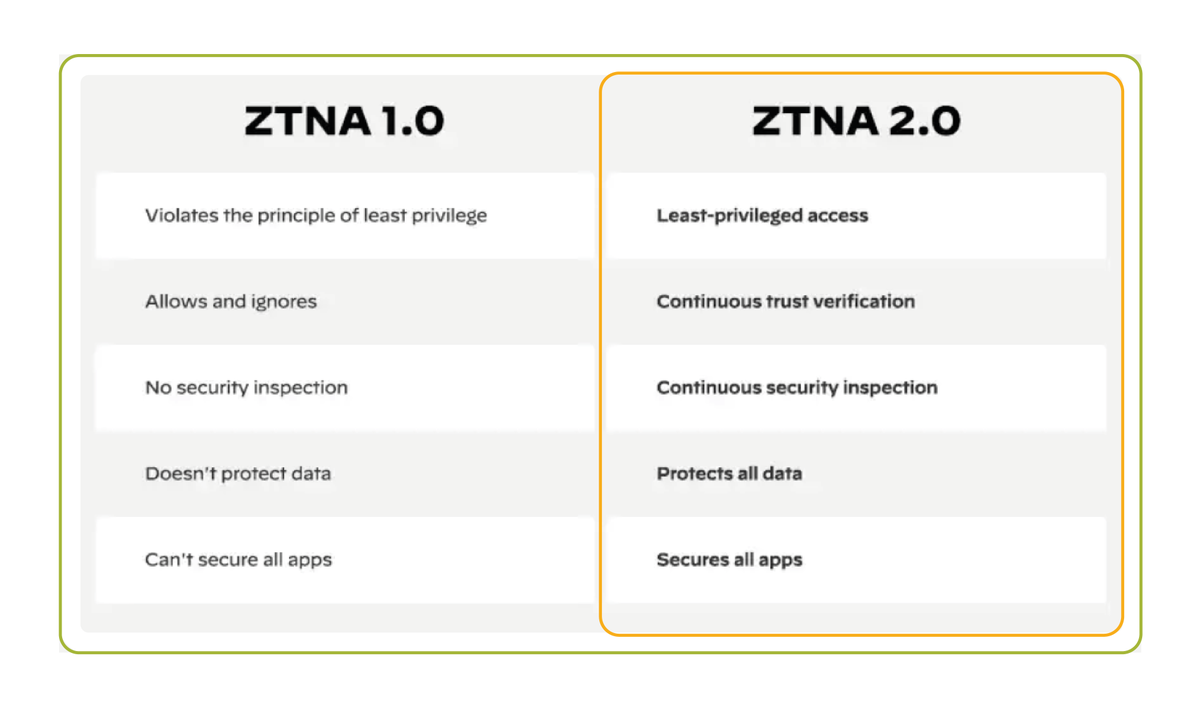
Does your organisation employ a Zero Trust model of verification? And if so, have you considered the move to ZTNA 2.0 in light of the fast-paced network security developments over the past few years? Graphic source: Palo Alto Networks #ZeroTrust #ZTNA #Cybersecurity #sase



Many different scams managed to dupe investors into giving over €9 million in 2023. Niamh Davenport, Banking & Payments Federation Ireland and Dermot Williams, Threatscape joined Matt Cooper. The Last Word todayfm.com/podcasts/the-l…

Learned a ton chatting to Kijo Ninja about Defender for Endpoint on Threatscape's latest podcast: • open-source tools for testing MDE against attacks • other uses for advanced hunting • day-to-day MDE management Check it out! YouTube: youtu.be/bvvIdloaRnc

We did it again! Delighted to be awarded Security Partner of the Year at the Microsoft Ireland Partner of the Year awards last night. Huge thanks to the team for another incredible year!


New video: 5 common Entra Conditional Access mistakes (and how to avoid them) Catch it here: youtube.com/watch?v=IHaGbM… Big shout out to my man Razi at Threatscape for his fantastic work on YouTube thumbnail clickbait gold.









A big shoutout to William Francillette Threatscape for their help and expertise is helping me setup a zero trust conditional access framework. Working with them has been such a great experience.