Tomer Peled
@tomerpeled92
Security Researcher at @Akamai
Checkout my CVE repository github.com/tomerpeled92/C…
ID: 1335555601120829442
https://medium.com/@tomerp_77017 06-12-2020 12:04:30
54 Tweet
229 Followers
17 Following

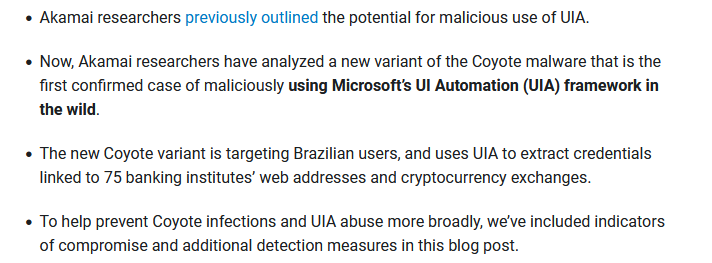
Did you hear that? Akamai researcher Ben Barnea has discovered two vulnerabilities within Windows. Leveraging the infamous custom reminder sound feature, these can be chained together to achieve full 0-click RCE against Outlook. Full write-up: akamai.com/blog/security-…



Command Injection in Kubernetes (<1.28.4) leading to RCE with SYSTEM privileges on all Windows endpoints within a Kubernetes cluster by applying a malicious YAML file (CVE-2023-5528) akamai.com/blog/security-… By Tomer Peled #kubernetest #azure #cybersecurity






Akamai researcher Tomer Peled discovered a design flaw in Kubernetes sidecar project Gitsync that could allow for command injection. No patch was assigned 👀 He originally presented his findings at DEF CON, and the full write-up is now available: akamai.com/blog/security-…

We would like to thank Tomer Peled (Tomer Peled) of Akamai Technologies for sharing details of CVE-2024-38030. This prompted us to take a deeper look at theme files, and allowed us to create micropatches to fix this additional issue for 0patch users.

Sometimes features intended for good can be used maliciously. 🫤 Read how Tomer Peled discovered an attack technique within Microsoft UI Automation that evades EDR. 👀 One of the possible outcomes is theft of credit card information. akamai.com/blog/security-…

Since 2023, 12 security vulnerabilities were discovered in Kubernetes. 4 of those were identified by our very own Tomer Peled. Ready for another one? This one is in Log Query and can achieve RCE with SYSTEM privileges on all endpoints in the cluster. akamai.com/blog/security-…




#Malware That Abuses UI Automation More in-depth research on this topic was published today: akamai.com/blog/security-… Akamai Security Intelligence Group Tomer Peled Thanks for the kind mention! Dodo on Security 🇵🇸 🇺🇦 Germán Fernández