
Nitesh Surana
@_niteshsurana
Examining Cloud w/ Trend Micro | Top 10 Microsoft MVRs 2024 | Black Hat USA/Asia Speaker | Opinions/retweets != official endorsements | If you can, be kind ♥️☮️
ID: 1548059695679606791
http://niteshsurana.com 15-07-2022 21:39:41
381 Tweet
654 Followers
984 Following


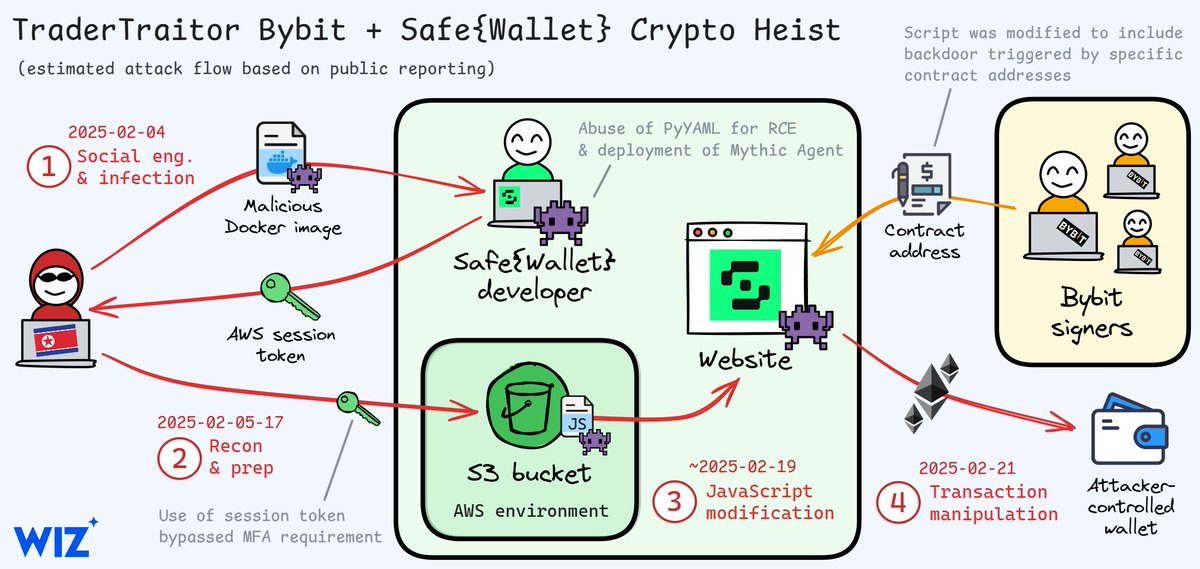
Diagram of the Bybit and Safe{Wallet} crypto heist attributed to DPRK actor TraderTraitor, based on currently available public reporting by Mandiant (part of Google Cloud), Sygnia, SlowMist, & Verichains.

[ZDI-25-205] Amazon AWS CloudFormation Templates Uncontrolled Search Path Element Remote Code Execution Vulnerability (CVSS 9.8; Credit: Nitesh Surana (Nitesh Surana) of Trend Micro Research) zerodayinitiative.com/advisories/ZDI…

[ZDI-25-206] Amazon AWS CloudFormation Templates Uncontrolled Search Path Element Remote Code Execution Vulnerability (CVSS 9.8; Credit: Nitesh Surana (Nitesh Surana) of Trend Micro Research) zerodayinitiative.com/advisories/ZDI…





It's a mild release from #Microsoft and a record-breaking release from #Adobe. There's a single 0-day to deal with in WEBDAV and, as always, a few deployment challenges. The Dustin Childs provides all the details at zerodayinitiative.com/blog/2025/6/10…

CVE-2025-20281: Cisco ISE API Unauthenticated Remote Code Execution Vulnerability: Trend ZDI analyst Bobby Gould details this bug and another that may be a dupe. He also shows how it can be exploited. zerodayinitiative.com/blog/2025/7/24…

I’m stoked to be presenting at fwd:cloudsec EU, along with William Gamazo Sanchez, on the broken threads of the cloud spider web. We’ll be showcasing real-world impact of cloud resource takeovers and cloud-powered supply chain attacks. fwdcloudsec.org/conference/eur…


[ZDI-25-858] Axis Communications Autodesk Plugin AzureBlobRestAPI axiscontentfiles Remote Code Execution Vulnerability (CVSS 8.8; Credit: Nitesh Surana (Nitesh Surana) of Trend Micro Research) zerodayinitiative.com/advisories/ZDI…

[POC2025] KEYNOTE SPEAKER UPDATE 👤 Brian Gorenc(Brian Gorenc) – "From Buffer Overflows to Breaking AI: Two Decades of ZDI Vulnerability Research" ZDI(Trend Zero Day Initiative) also stands with their 20 years! Now AI finds 0days— but the bugs? still the same old mess. #POC2025
![POC_Crew 👨👩👦👦 (@poc_crew) on Twitter photo [POC2025] KEYNOTE SPEAKER UPDATE
👤 Brian Gorenc(<a href="/MaliciousInput/">Brian Gorenc</a>) – "From Buffer Overflows to Breaking AI: Two Decades of ZDI Vulnerability Research"
ZDI(<a href="/thezdi/">Trend Zero Day Initiative</a>) also stands with their 20 years!
Now AI finds 0days—
but the bugs? still the same old mess.
#POC2025 [POC2025] KEYNOTE SPEAKER UPDATE
👤 Brian Gorenc(<a href="/MaliciousInput/">Brian Gorenc</a>) – "From Buffer Overflows to Breaking AI: Two Decades of ZDI Vulnerability Research"
ZDI(<a href="/thezdi/">Trend Zero Day Initiative</a>) also stands with their 20 years!
Now AI finds 0days—
but the bugs? still the same old mess.
#POC2025](https://pbs.twimg.com/media/Gz_Wa_lboAAzE6c.jpg)



Nice one Petrus Germanicus 🔥🔥🔥!

Crafting a Full Exploit RCE from a Crash in Autodesk Revit RFA File Parsing: Trend ZDI researcher Simon Zuckerbraun shows how to go from a crash to a full exploit - & he provides you tools to do the same, including his technique used to get ROP execution. zerodayinitiative.com/blog/2025/10/6…

Don't forget to also checkout the cloud side of the attack in the blog written by Nitesh Surana trendmicro.com/en_us/research…



