
Andrey Konovalov
@andreyknvl
Security engineer at xairy.io. Focusing on the Linux kernel. Maintaining @linkersec. Trainings at xairy.io/trainings.
ID: 2350019719
https://xairy.io 18-02-2014 12:03:47
1,1K Tweet
6,6K Followers
769 Following



In our final ksmbd research post, 73696e65 provides a detailed walkthrough for exploiting a local privilege escalation vulnerability. If you're interested in learning more about exploitation on modern systems - check it out! blog.doyensec.com/2025/10/08/ksm… #doyensec #appsec #security



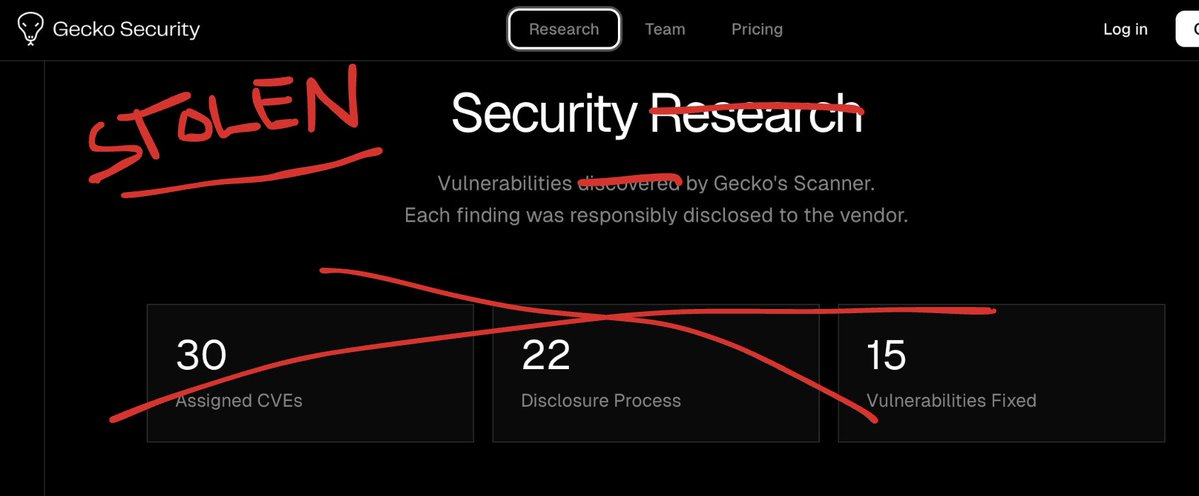
💣 We caught Y Combinator–backed Gecko Security stealing two of our CVEs, one on ollama , one on Gradio. They copied our PoCs, claimed CVE IDs, and even back-dated their blog posts. Here’s the full story 👇









More HW security goodness from Arm: community.arm.com/arm-community-… vMTE (Virtual Memory Tagging) allows to use MTE in a more flexible way, consuming less RAM. POE2 allows to build efficient in-process sandboxes and isolation. More-or-less improvement over x86 Memory Protection Keys.



Faith 🇧🇩🇦🇺 I believe this technique has been known for a while now, first saw it in GoogleCTF and was later used in starlabs.sg/blog/2023/07-a…

🚨 New advisory was just published! 🚨 A Local Privilege Escalation vulnerability was found in Ubuntu, caused by a refcount imbalance in the af_unix subsystem. This vulnerability was disclosed during our TyphoonPWN 2025 Linux category and won first place: ssd-disclosure.com/lpe-via-refcou…

