
Kent Landfield
@bitwatcher
ID: 34609999
23-04-2009 13:24:01
403 Tweet
145 Followers
97 Following


Never let a good international sporting event go to waste... Trellix Advanced Research Center article of "Email Cyberattacks on Arab Countries Rise in Lead to Global Football Tournament" trellix.com/en-gb/about/ne…

During his panel, our Chief Standards and Technology Policy Strategist Kent Landfield (Kent Landfield) emphasized the need to establish SBOM standard practices and addressed their role in supply chain security. #CyberNextDC2022

As criminals extort #healthcare victims with #ransomware, victims urged to prepare rather than pay, especially for false data-wiping promises bit.ly/3uTvvk5 by Mathew J Schwartz POV: Coveware John Fokker Trellix Sophos Allan “Ransomware Sommelier🍷” Liska Recorded Future



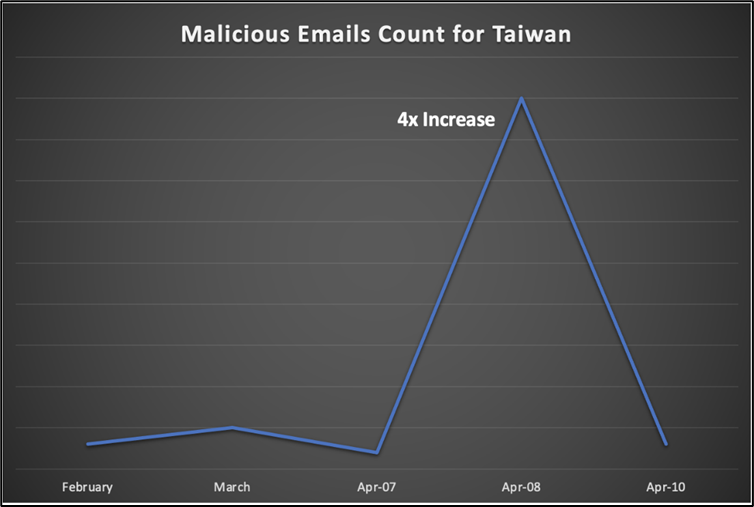
For several months, we saw increased cyberattacks against Taiwanese organizations. In April 2023, we observed a surge over the course of four days — 4x the average at its peak. Researchers Daksh Kapur and Leandro Velasco explain our findings on the blog. bit.ly/3pNkyl7

As always, John Fokker does a fantastic job explaining the “what” and “why” behind a cyber threat. Read his explanation of the global rise in hacktivism in @secinfowatch. bit.ly/41B6BnS

While investigating vulns in the ICS & SCADA space, we uncovered 2 CVEs in Triangle MicroWorks’ SCADA Data Gateway — CVE-2023-2186 & CVE-2023-2187. Charles McFarland shares insights from the manufacturing industry threat landscape exemplified by this discovery. bit.ly/3L4iTyz



Head of Threat Intelligence John Fokker shares our observations on cybercriminal behavior from over a year virtually staked out in the Genesis Marketplace — these insights ultimately assisted law enforcement in the market’s takedown. Hear more. bit.ly/43pvfsz

NIST in 2022 “also celebrated 50 years of work in the cybersecurity space and [the National Cybersecurity Center of Excellence] celebrated a 10-year anniversary since inception.” Cybersecurity @ NIST

CISA considers next steps for zero trust guidance with work on applications, OT under development insidecybersecurity.com/daily-news/cis… CISA Cyber CloudSecurityAlliance






“Diversity leads to better #cybersecurity outcomes, and better cybersecurity outcomes lead to better business outcomes," says Cory Bullock. #Diversity in the cyber #workforce is more than a moral imperative, it’s key to biz continuity. #CyberNextDC


Dive into the latest episode of Distilling Cyber Policy! Alex Botting and Jen Ellis chat with John Banghart and Kent Landfield about the National Vulnerability Database. Tune in to learn about the NVD's history, challenges, and future: centerforcybersecuritypolicy.org/insights-and-r…




