
Chris Beckett
@cbecks_2
Infosec and the Green Bay Packers. Interested in all things DFIR, Detection Engineering, Purple, and CTI. Opinions are mine, certainly not those of my employer.
ID: 1064678389146103808
20-11-2018 00:34:43
732 Tweet
785 Followers
2,2K Following



Florian Roth ⚡️ I think so - at some point in time these "logs" will be sync'ed to the cloud, because, "cloud". Then, on a Friday, random announcement, breach that affected a "limited number of customers", the "hackers were looking for Recall logs from certain customers". Sounds familiar? 😃

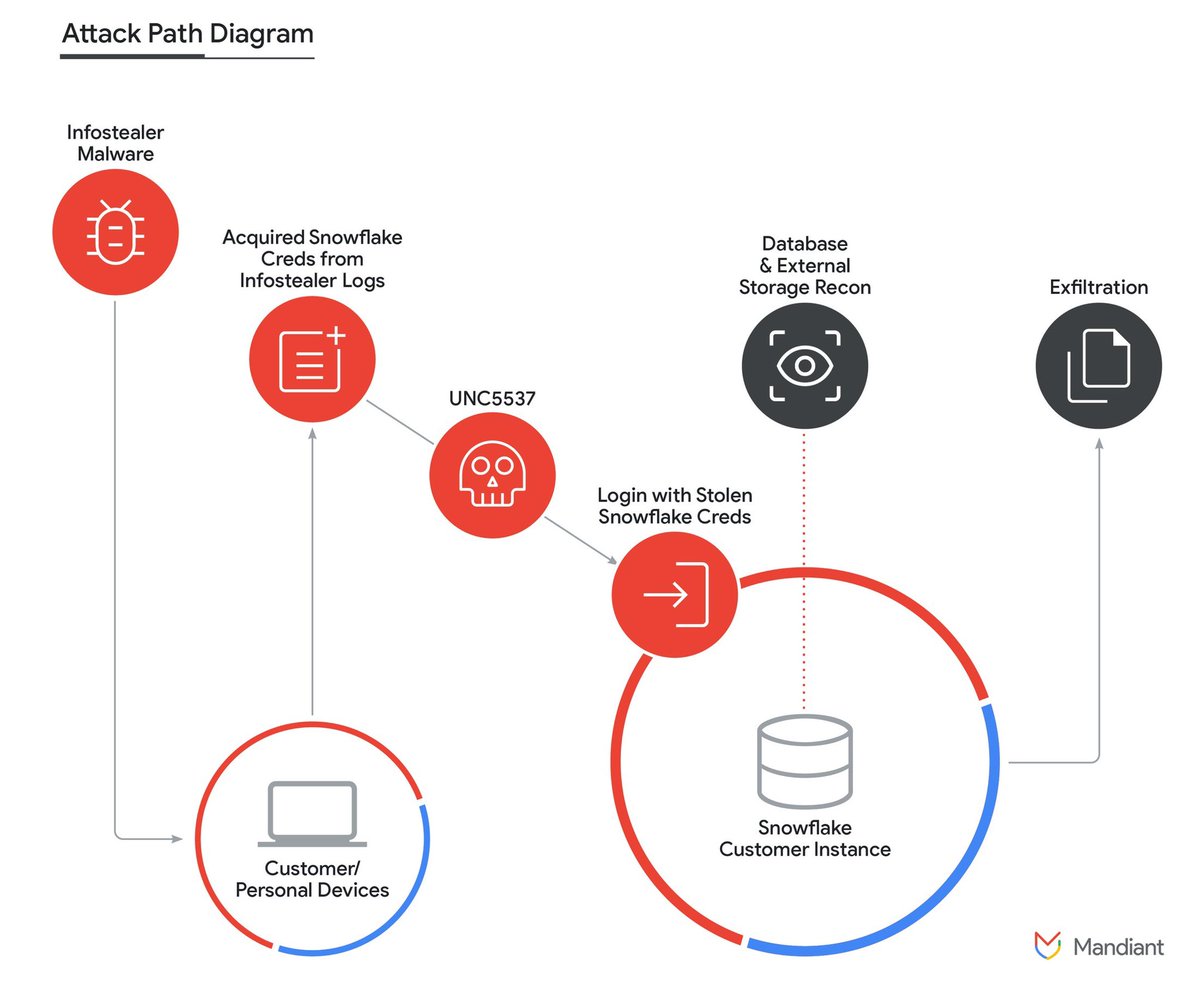
Mandiant (part of Google Cloud) is releasing details on a data theft and extortion campaign undertaken by UNC5537, targeting Snowflake customer instances. Since April, UNC5537 has leveraged stolen credentials to target over 100 organizations. cloud.google.com/blog/topics/th…






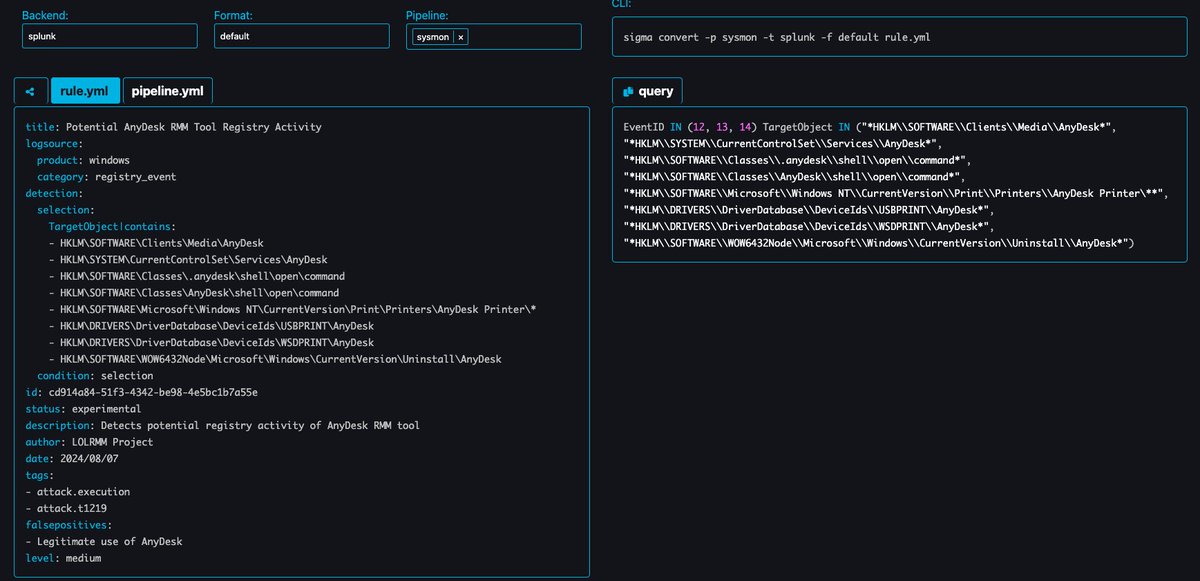
🚨LOLRMM Update 🚂 You thought we were done? Nope. 🔥 Deduplication efforts are in the works 🔥 Experts (Jose Enrique Hernandez) are reviewing the site code to ensure we deliver the most epic LOLRMM experience. 🔥 More and more RMMs are being completed (Kostas Nasreddine Bencherchali ) 🔥 Who


Florian Roth ⚡️ It's also regrettable that you can't properly manage VSCode on enterprise level: you can't blanket-disable extensions/only allow verified ones/only allow allowlisted ones; let alone manage it in a useful way via e.g. group policies. github.com/microsoft/vsco… code.visualstudio.com/docs/setup/ent…





