Christian Posta
@christianposta
VP, Global Field CTO @soloio_inc, author #Istio in Action, contributor & steering committee @IstioMesh, architect, speaker, #API #ServiceMesh #Microservices
ID: 244131858
http://blog.christianposta.com 28-01-2011 15:52:42
12,12K Tweet
11,11K Followers
410 Following


Christian Posta AI is exposing everyone's auth weakness. We always had these problems. Now they are being brought to light


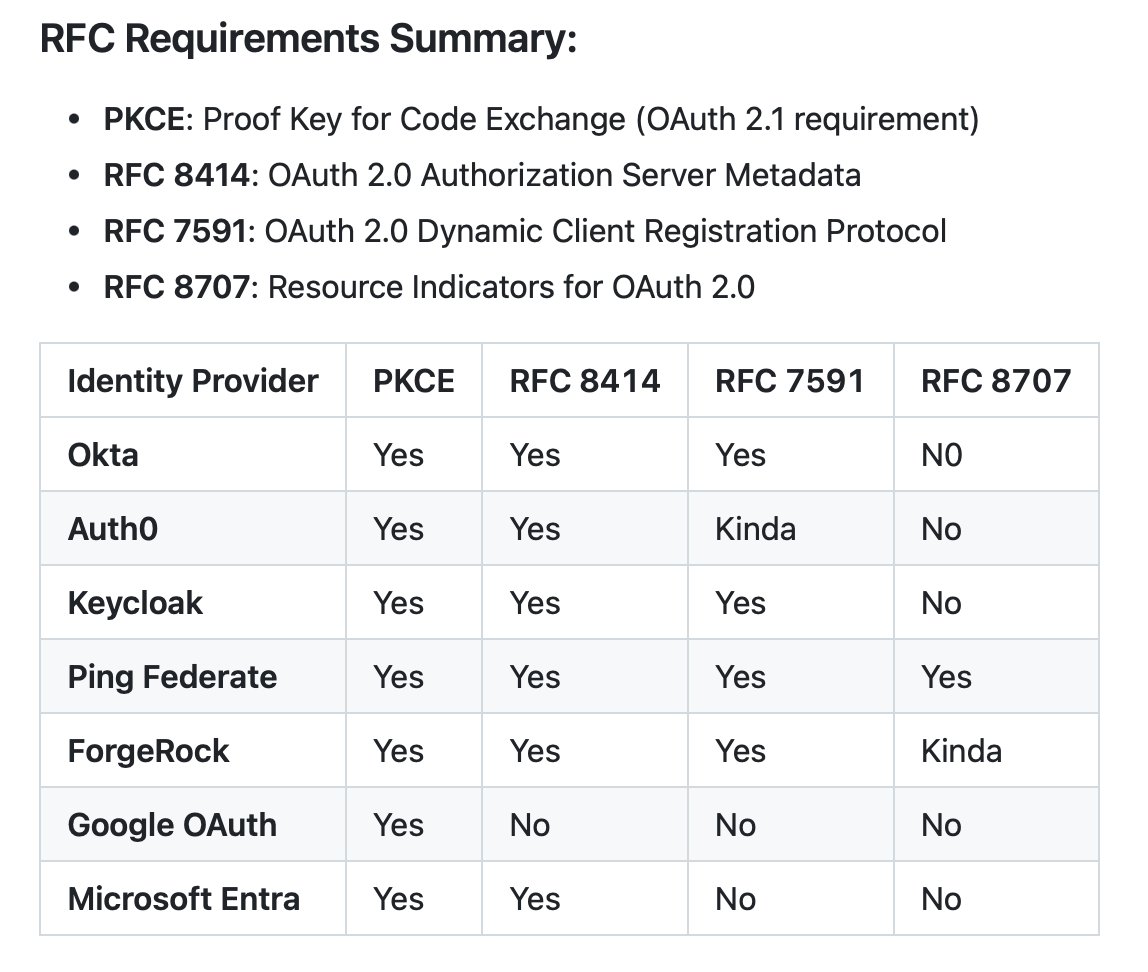
Christian Posta AI agents demand stricter identity and auth, what key principles from microservices can we keep, and where must we rethink security?


🎙️Gloo’d In Ep. 1 is live! Anuj Singh chats with Christian Posta about Solo.io’s open source work in AI—covering MCP, Kagent, and Kgateway. 🎧 Tune in:youtu.be/UprfqOi5LdU #AI #OpenSource #Kagent #Kgateway #MCP #CloudNative #Soloio


Agent identity is critical for authorization. In his latest blog, Christian Posta explores how SPIFFE fits in today’s AI-driven infra like Kubernetes & Istio—and what may need to change. 🧠 Read it here: bit.ly/44CbJfI #AI #SPIFFE #AgenticAI #Kubernetes #Identity





After 3 years, I am thrilled to be able to announce that the Argo CD book that Christian Hernandez and I have written is now available! Learn how to leverage the full set of features included within Argo CD which implement GitOps principles based on years of industry experience with





Join us for this week’s #vClusterFriday as we take a closer look at kgateway, a CNCF sandbox project for Kubernetes-native API gateways. Saiyam Pathak & kramm are joined by Lin Sun and Christian Posta to walk through how it works. 🎥 youtube.com/watch?v=J4YSbn…