CIRCL is the CERT (Computer Emergency Response Team) for the private sector, communes and non-governmental entities in Luxembourg.
ID: 184762389
http://www.circl.lu/ 30-08-2010 12:32:08
11,11K Tweet
13,13K Followers
1,1K Following




Post by Black Lotus Labs on a large multi-tiered botnet operated by Flax Typhoon. Tier2 nodes can be identified by TLS certificate with random alphanumeric domain name in subject/issuer DN. blog.lumen.com/derailing-the-… #CTI #botnet #iot



Omg, Saâd Kadhi (M: https://infosec.exchange/@saadk) , Adel Ka , Alexandre Dulaunoy @[email protected] , Raphaël Vinot - @[email protected], Thomas Patzke, tomchop, David -- 🇪🇺 😈 🇧🇪 , Ange , Hilko Bengen / @[email protected] and so many more. What is this, a conference or a DREAM team from all recorded speakers ever from Cooper? What a line up.


New features in vulnerability lookup includes sighting from different sources including MISP (@[email protected]) communities. The example below is a vulnerability in Android but the CVE is not yet published. You can track the sighting evolution. vulnerability.circl.lu/vuln/CVE-2024-… #vulnerability #cve


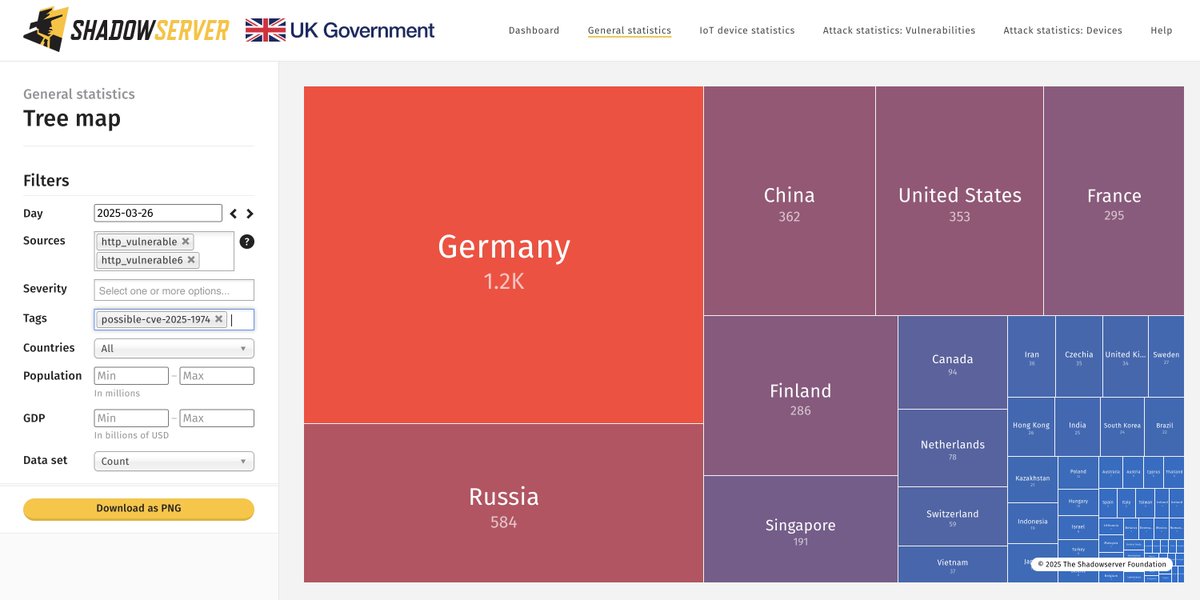
CVEs have now been assigned: unit42.paloaltonetworks.com/cve-2024-0012-… security.paloaltonetworks.com/CVE-2024-0012 security.paloaltonetworks.com/CVE-2024-9474 6642 IPs found exposed on 2024-11-17 (down from around 11K): dashboard.shadowserver.org/statistics/iot… As a reminder, IP data is shared in our Device ID report daily: shadowserver.org/what-we-do/net…


We see CVE-2024-0012 exploitation attempts since Nov 18th. We are now also observing CVE-2024-9474. IoCs: unit42.paloaltonetworks.com/cve-2024-0012-… Check for signs of compromise and patch: security.paloaltonetworks.com/CVE-2024-0012 security.paloaltonetworks.com/CVE-2024-9474 For additional background - labs.watchtowr.com/pots-and-pans-…




There's a wealth of useful threat data available via Rösti, Repackaged Öpen Source Threat Intelligence. Formats include STIX, JSON, CSV and MISP. Provided by Johannes Bader . And now also available as a default MISP (@[email protected]) feed. Check out rosti.bin.re


If you’re using Let's Encrypt certificates it becomes time to setup a certificate expiration monitor (if you haven’t done already).




I created a small parser for Minimedusa (the MegaMedusa configuration, an L7 DDoS tool). It uses TEAM CYMRU Whois, CIRCL - @[email protected] Passive DNS service and an RDNS lookup for enrichment. There's also a MISP JSON to import the feed in MISP (@[email protected]) github.com/cudeso/tools/t…


CFP REMINDER: D-15 Hurry up, it's time to submit your Security & Free SW talk or workshop! ➡️ cfp.pass-the-salt.org/pts2025/cfp 📅 deadline: sunday March, 30 midnight! ✉️ a question? send it to [email protected] 👍 🙏RT appreciated!