Craig S. Blackie
@craigsblackie
Hacker, network admin, ale drinking geek and lover.
ID: 66860762
19-08-2009 00:57:20
3,3K Tweet
310 Followers
475 Following












Managed to get BitPixie exploit working in VM and hardware with Darren McDonald . Cool hack, specially with an fTPM.

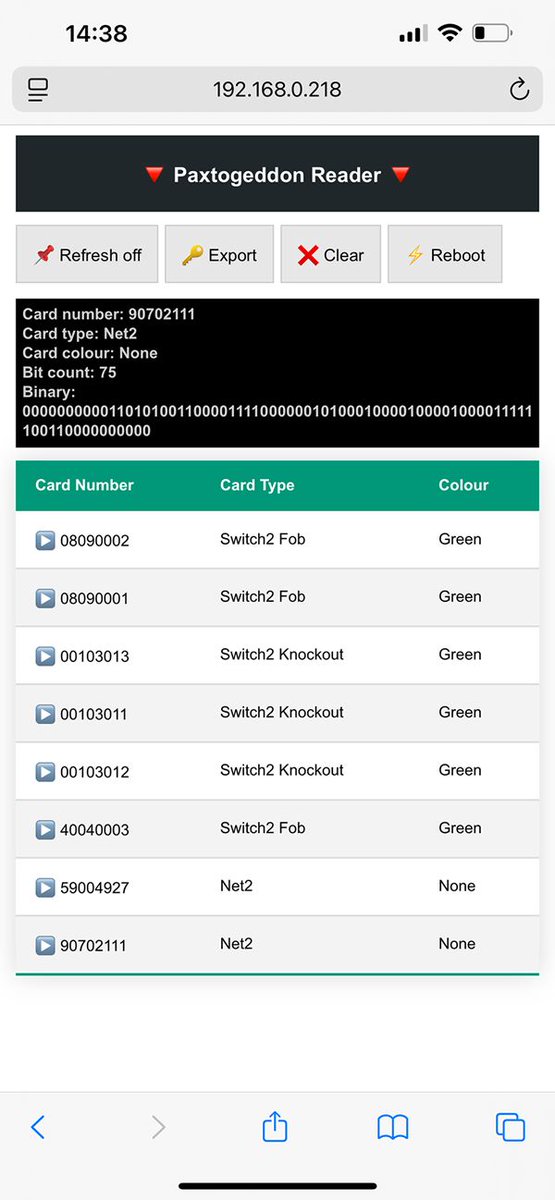
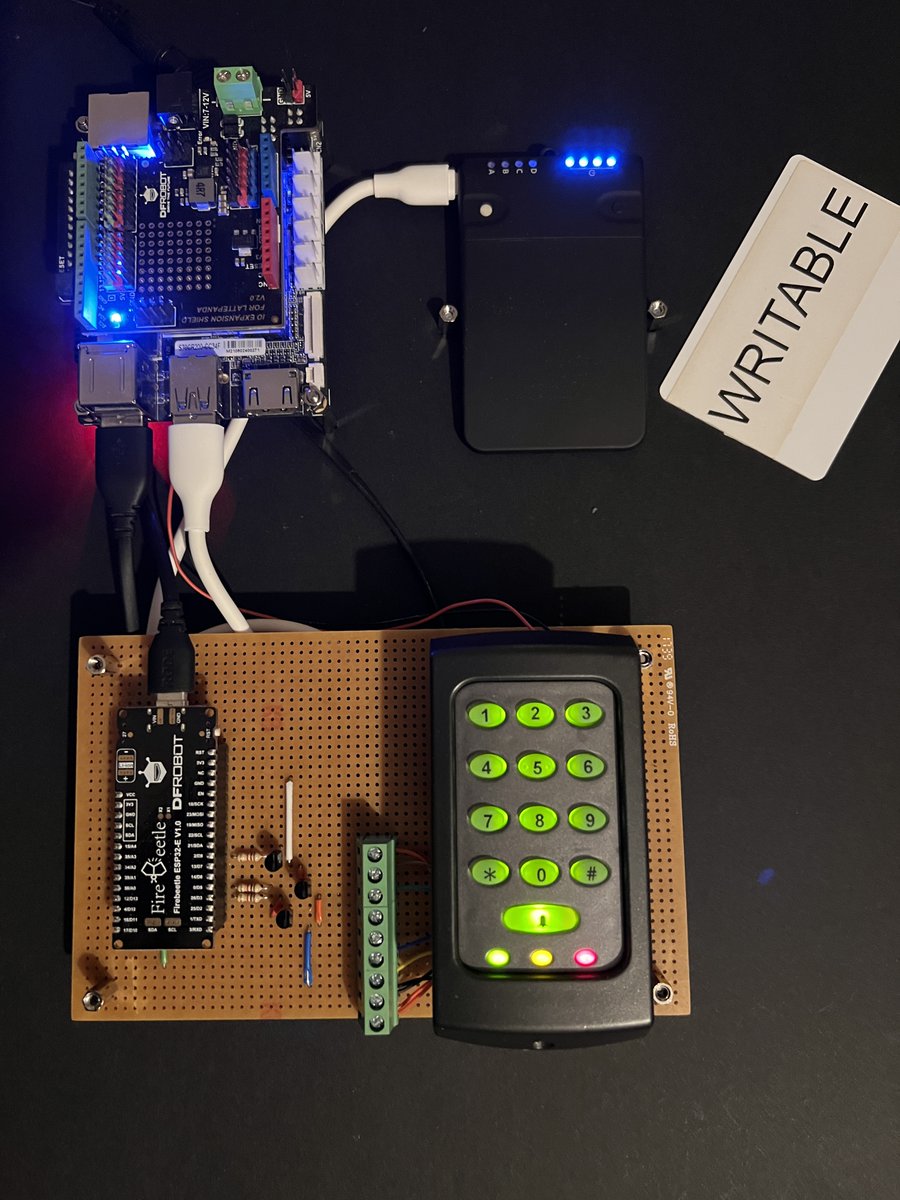
#Proxmark3 RDv4.01 all setup and working with Iceman - next stop Troopers! Iceman firmware. Working in conjunction with my Paxtogeddon Reader for card/fob reading and logging, we use this device to clone the exported data. Works like an absolute charm. 😍 #CardCloning #RFIDHacking