
Daniel Grzelak
@dagrz
Super Serious Internet Guy™️
Founder of Milo Twitter. Peak Milo. At the intersection of cyber security, Milo, and stonks. Chief Innovation Officer @ Plerion.
ID: 121391248
https://linktr.ee/dagrz 09-03-2010 10:37:27
6,6K Tweet
2,2K Followers
1,1K Following



📚 tl;dr sec 258 🤖 Google's AI-powered Fuzzing Oliver Chang, Jonathan Metzman ☁️ What Hackers know about your AWS Account Daniel Grzelak 🔬 Finding vulns in EDR Neodyme ☁️ How to use AWS Resource Control Policies Scott Piper 🤖 Augmenting SAST with AI and more! tldrsec.com/p/tldr-sec-258

📺 AWS re:Invent 2024 Security Talks 33 cloud security talks to up your game Curated by Daniel Grzelak youtube.com/playlist?list=…




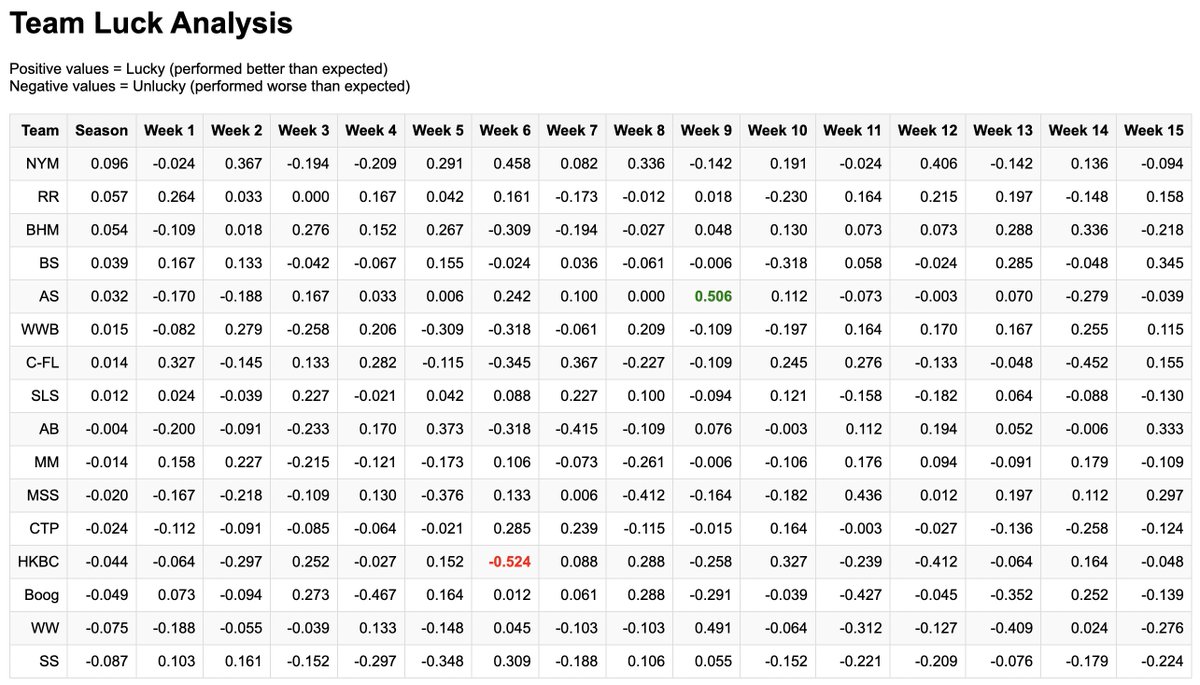
I made a matchup luck calulator for ESPN H2H fantasy basketball leagues. Sometimes you play a really strong, and lose each category by a tiny bit so your team looks terrible when you would have beaten every other team. github.com/dagrz/nba-matc… Josh Lloyd


DynamoDB read operations like "GetItem", "Query", and "Scan" aren’t the only way to retrieve data. Some write operations can also return data, and if you're not careful, you might be leaking information without even realizing it. H/T Aidan W Steele




My maiden voyage interviewing with Patrick Gray is live, and it's a fun one: HD Moore on why vuln scanners are awful and broken - Risky Business Media m.cje.io/45679XN Enjoy!




