diversenok
@diversenok_zero
Aspiring Windows security researcher & system programmer; student.
ID: 1171858390668251137
https://github.com/diversenok 11-09-2019 18:52:58
241 Tweet
1,1K Followers
40 Following






This new book has finally arrived. Thank's to No Starch Press as well as Bill Pollock -- [email protected] for making it happen as well as Lee Holmes as my tech reviewer.


My new blog post for Hunt & Hackett is out! 🥳 It describes how it's possible to create a novel forensic tool that can reconstruct (malicious) executables on Windows without relying on collecting files or parsing attacker-controlled process memory. huntandhackett.com/blog/reconstru…




A new blog post on OS design principles, the purpose of BSOD, and challenges of driver dev "On System Reliability and Why the (Conceptual) Design of the Blue Screen on Windows Is a Good Thing" I cannot lie; the idea was inspired by some recent events 😉 huntandhackett.com/blog/on-system…


Restart Manager is an API to identify & close programs locking a given file. 💡 We're releasing a forensic tool at Hunt & Hackett to parse the artifacts it leaves behind. They exist in a volatile registry key which is not persisted in the hive file. huntandhackett.com/blog/introduci…

After my latest newsletter issue, diversenok reached out to me with an interesting observation: a password can be encrypted and still functions identically to a cleartext one in CreateProcessWithLogonW(). 😮 This brought up two intriguing questions: 1. How can I decrypt


Better socket handle visibility coming soon to System Informer 🔥 When viewing a process handle table, SI will recognize files under \Device\Afd and retrieve information about their state, protocol, addresses, and more. Also works on Bluetooth and Hyper-V sockets 🤩
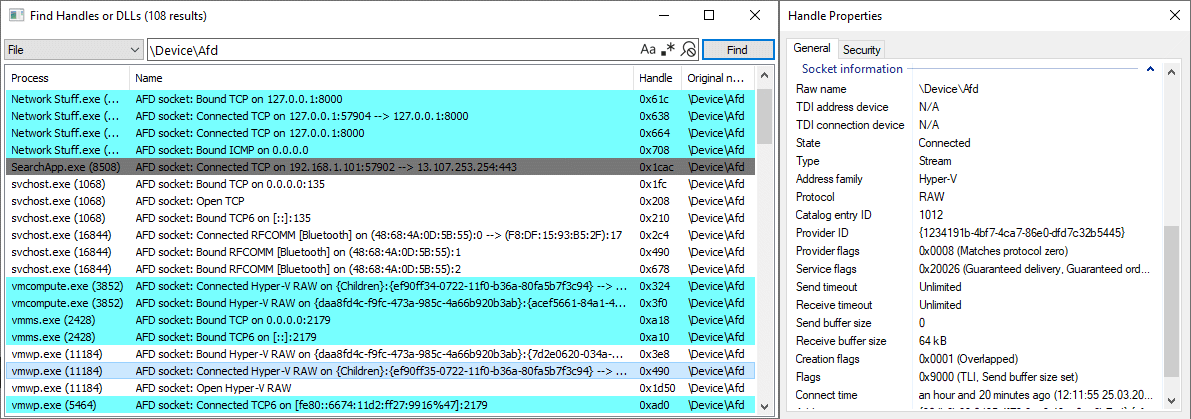



My new blog post 🥳 Improving AFD Socket Visibility for Windows Forensics & Troubleshooting It discusses the low-level API under Winsock (IOCTLs on \Device\Afd handles) and explores the workings of the new socket inspection feature in System Informer 🔥 huntandhackett.com/blog/improving…