Duty
@duty_1g
Application Security Specialist | Red Teamer | Researcher at Synack Red Team | OSCP-OSCE-OSWE-ECPPT-CRTE/P/O | CTF Player @DeadSecCTF
Capturing flags since 2011
ID: 1248712237663084544
10-04-2020 20:39:39
41 Tweet
377 Followers
117 Following

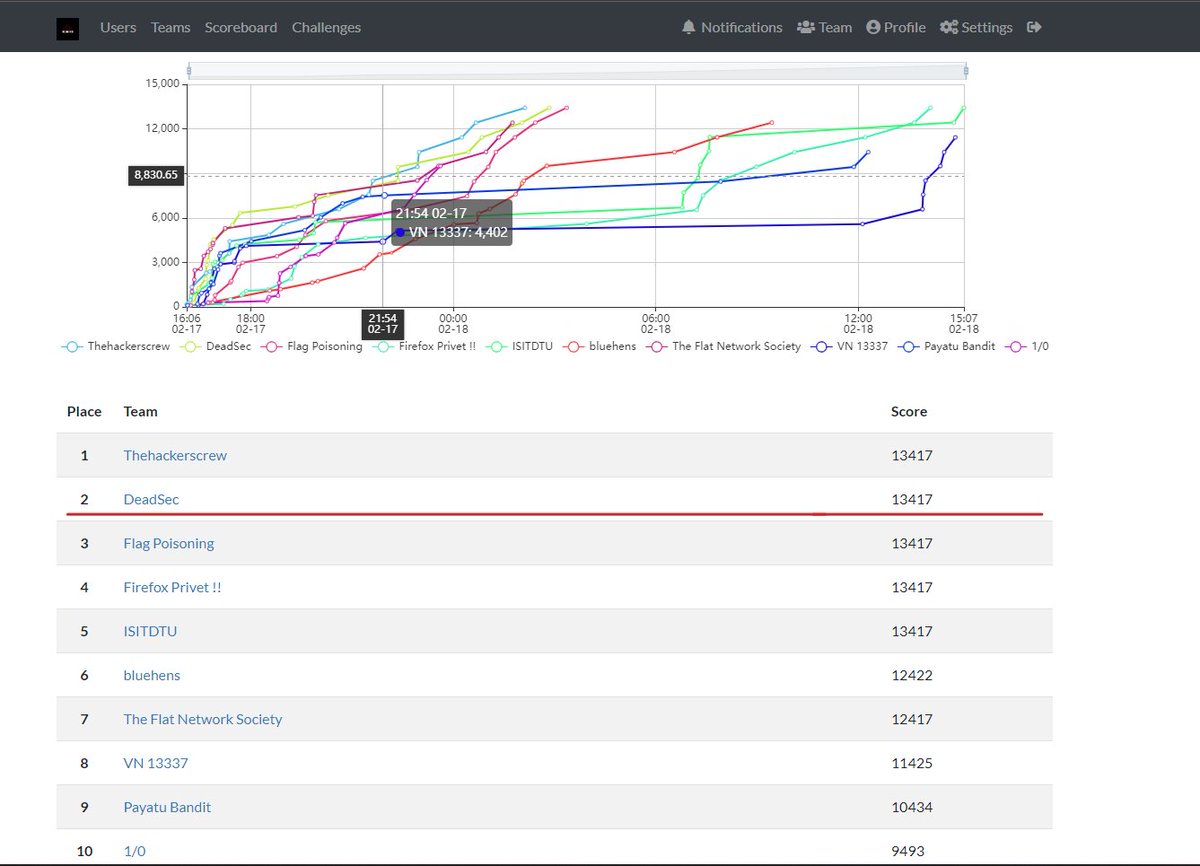
DeadSec has just achieved an impressive 2nd place finish in the Incognito 4.0 CTF! Our team worked tirelessly to secure this achievement, and we're incredibly proud! And Congratulations to thehackerscrew for the 1st place!













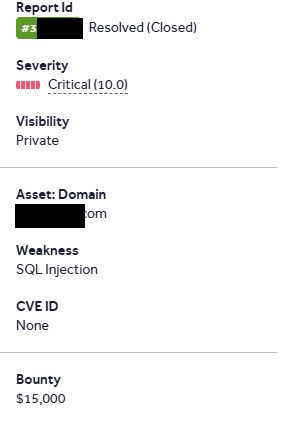
Check out my latest Exploit Explained Bug Bounty writeup for Synack Red Team 🚨 Turning Frontend Clues into Backend Compromise: Insecure Routing to RCE #Synack #CyberSecurity #ExploitExplained #AppSec #BugBounty #RCE #InfoSec synack.com/exploits-expla…


LOLdrivers.io now has SIEM queries and a tool section for those looking to operationalize the data. Thanks to Mehmet Ergene and The Haag™ for sharing the queries with the community! Also shout out to Tenable for sharing the Nessus plugin, Oddvar Moe for the