frycos
@frycos
Private account! Red teamer @codewhitesec. @[email protected] @frycos.bsky.social
ID: 991384637841735681
https://github.com/Frycos 01-05-2018 18:31:31
3,3K Tweet
3,3K Followers
514 Following






Oh shit I missed the registration deadline for Off-By-One Conference ! Do I know anyone that can still get me a ticket?! I don't mind paying some penalty fee for being so lazy/late.. !!





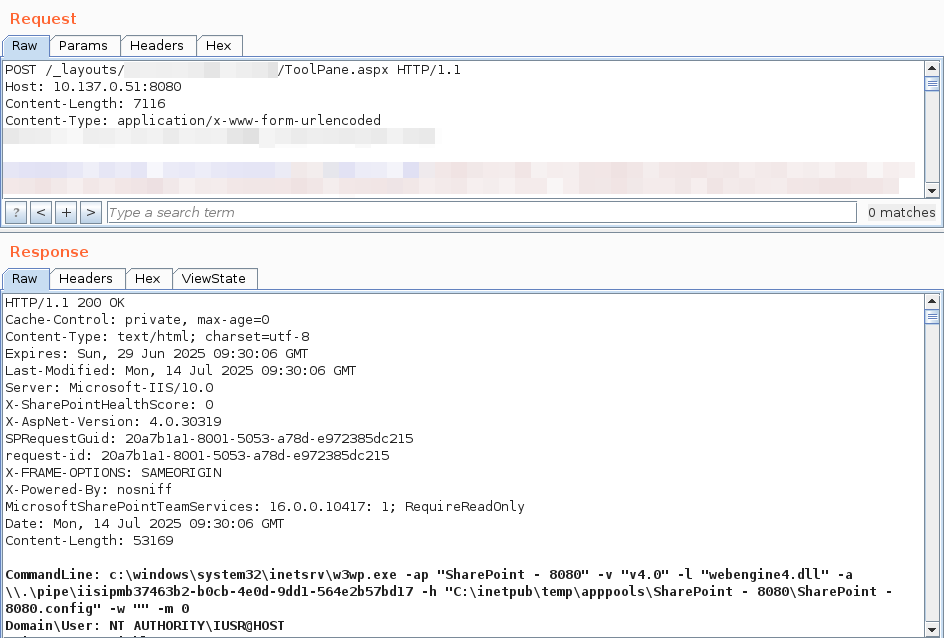
And domain-level RCE in Veeam B&R fixed today (CVE-2025-23121). My first (and hopefully not last) CVE, where I'm credited together with CODE WHITE GmbH 😎







I’m not gonna attend this year. For the rest of you, happy partying with Security Response