Maxim Goryachy
@h0t_max
Hardware/Software/Firmware/IntelME Researcher. Opinions are my own and not the views of my employer. [email protected] |
github.com/h0t
ID: 780349202337529856
https://keyserver.ubuntu.com/pks/lookup?op=get&search=0x4634aeee2ea8993f 26-09-2016 10:12:02
826 Tweet
6,6K Followers
259 Following





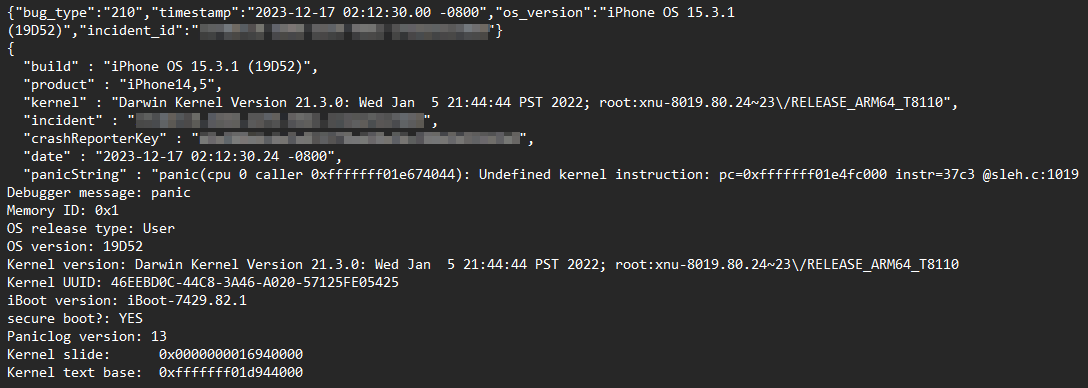
All the details about this vuln and much more will be revealed tomorrow by us (me, Leonid Bezvershenko, Georgy Kucherin) during our talk “Operation Triangulation: What You Get When Attack iPhones of Researchers” at #37c3 (14:45 CET). There will also be a live stream. fahrplan.events.ccc.de/congress/2023/…

We're revealing details of an obscure debugging feature in the Apple A12-A16 SoC’s that bypasses all of the hard-to-hack hardware-based memory protections on new iPhones. Its not used by the firmware and we don't know how the attackers found out about it. securelist.com/operation-tria…



François-Philippe Champagne (FPC) 🇨🇦 Dear François-Philippe, We'd appreciate it if you could provide any evidence of Flipper Zero being involved in any criminal activities of this kind. We're not aware of any events like this and frankly speaking not sure what was the reason for this discussion to begin with.










We're going to be moving forward under the expectation that future Pixel devices may not meet the requirements to run GrapheneOS (grapheneos.org/faq#future-dev…) and may not support using another OS. We've been in talks with a couple OEMs about making devices and what it would cost.