Daniel Heinsen
@hotnops
doin thangs @specterops
ID: 1237387084899516416
https://github.com/hotnops/ 10-03-2020 14:38:12
266 Tweet
1,1K Followers
315 Following



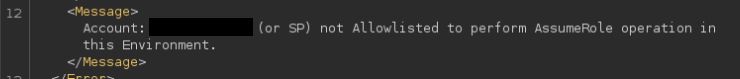
PSA: Apeman exposes a Neo4J panel under the hood. Here is a query to detect roles that are vulnerable to the Amplify vulnerabilities that Nick Frichette presented at Blackhat. Gist here: gist.github.com/hotnops/a1d4ab…








Don't miss our next webinar w/ Daniel Heinsen, which will showcase how Apeman can quickly identify Attack Paths by solving AWS CTF challenges. Each challenge will highlight a common misconfiguration & how Apeman can help identify them. Register today ▶️ ghst.ly/4dCog48









MSSQLHound leverages BloodHound's OpenGraph to visualize MSSQL attack paths with 7 new nodes & 37 new edges, all without touching the SharpHound & BloodHound codebases. Chris Thompson unpacks this new feature in his blog post. 👇 ghst.ly/4leRFFn