Ian Thiel
@ianthiel
Human. Co-Founder @sublime_sec Formerly @AltoPharmacy @Optimizely @SpaceAngels
ID: 271445035
http://ianthiel.io 24-03-2011 14:34:54
5,5K Tweet
2,2K Followers
2,2K Following


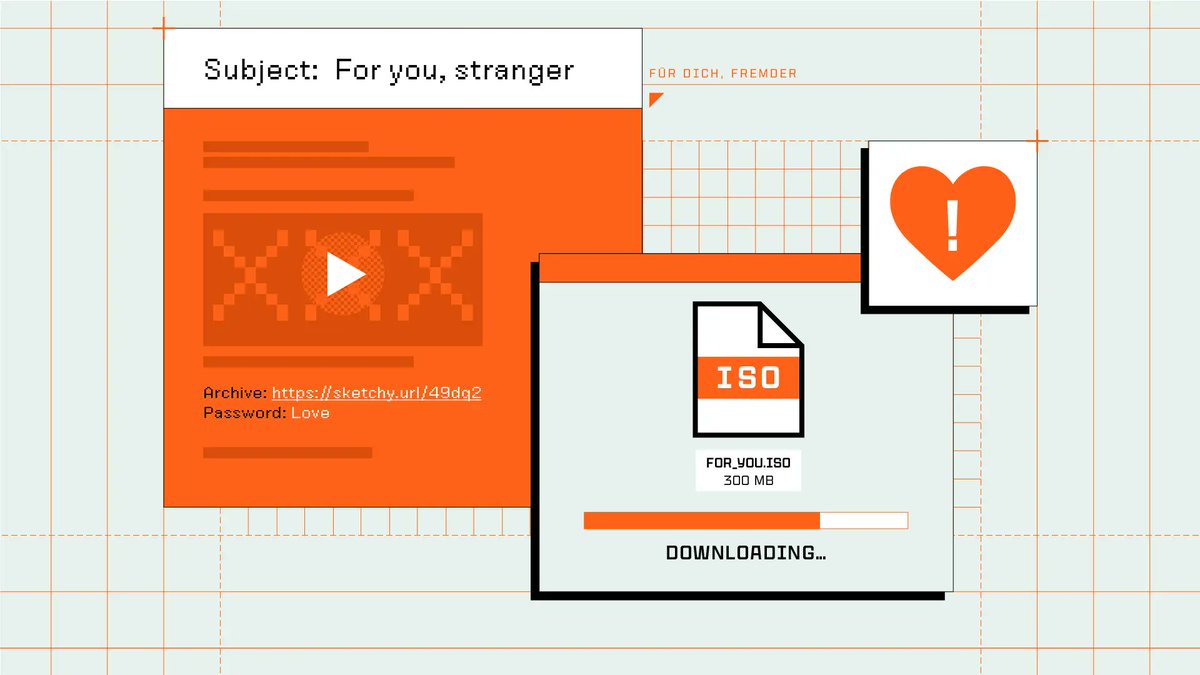
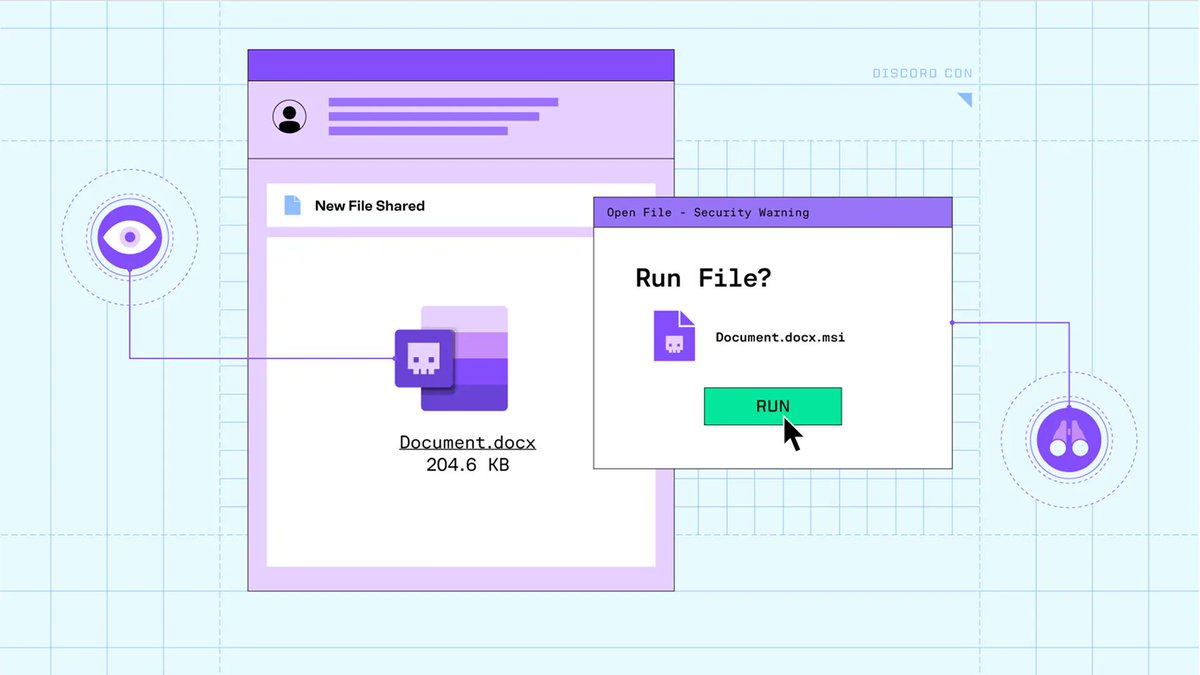
Andrew Levy Hey Andrew, great catch. We’ve seen the same spike lately and just published a write-up breaking it down: 🔗 sublime.security/blog/living-of… TL;DR: Attackers are abusing Zoom’s trusted docs.zoom[.]us domain to host credential phishing pages. Because Zoom is often allowed through