
itszn
@itszn13
Amy | Security researcher | stackchk.fail/ctf.txt | bsky: nyanbox.stackchk.fail |
LLM ART: bsky.app/profile/altern…
ID: 320851335
https://ret2.io/ 20-06-2011 16:46:39
1,1K Tweet
9,9K Followers
693 Following





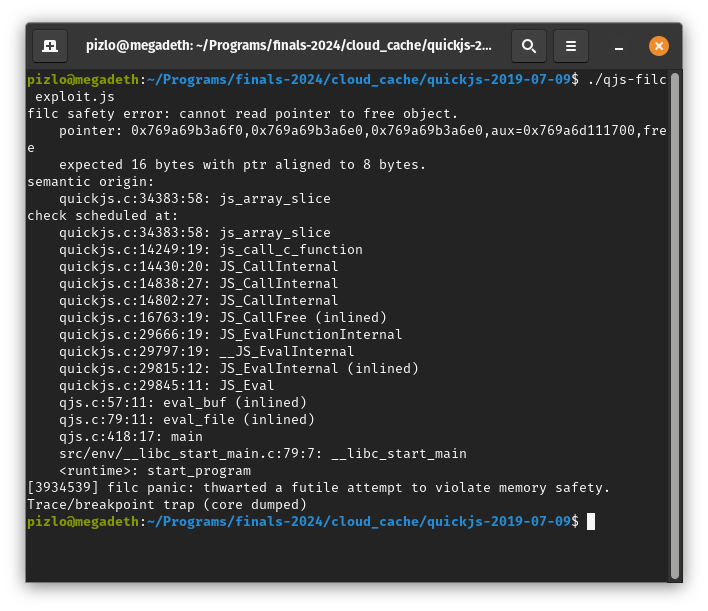
This is what I mean by Fil-C being memory safe. On the left, quickjs from 2019-07-09 compiled with GCC (i.e. Yolo-C) running Christopher Argüelle's exploit. Exploit works. On the right, same quickjs compiled with Fil-C running the same exploit. Memory safety error caught! According to






New blogpost! Want to see how we exploited Synology Inc. network-attached-storage devices at Pwn2Own Ireland? RCE to root via out-of-bounds NULL-byte writes, click the embed for a fun little writeup of CVE-2024-10442 🔎🎉 blog.ret2.io/2025/04/23/pwn…


I'm proud to announce that myself and Ati Priya Bajaj have created the Workshop on Software Understanding and Reverse Engineering (SURE), which will be co-located at CCS 2025. sure-workshop.org Please follow our workshop account ACM SURE Workshop and RT it for visibility :).








