Jared Atkinson
@jaredcatkinson
| CTO @specterops | Host @dcpthepodcast | Ex PowerShell MVP | USAF Vet | FC Bayern Supporter | Language Learner 🇳🇴 🇮🇹 🇧🇷 |
ID: 1608740100
https://posts.specterops.io/on-detection/home 20-07-2013 18:13:53
7,7K Tweet
10,10K Followers
1,1K Following

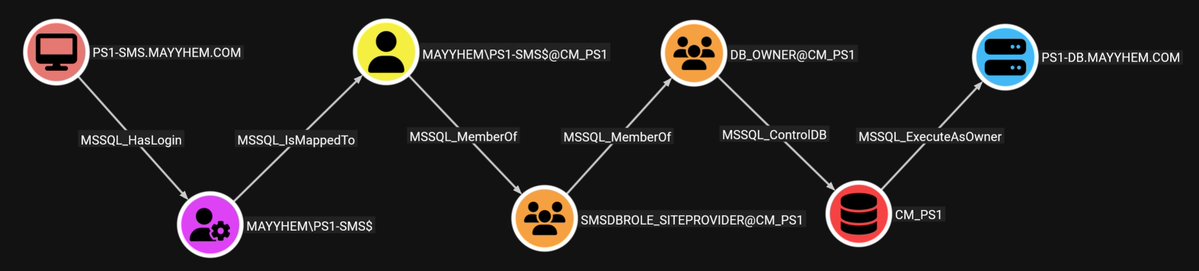
How attackers move between AD domains via trusts depends on trust type & config. We're replacing TrustedBy edge in BloodHound with new trust edges for better attack path mapping. Check out Jonas Bülow Knudsen's blog post to learn more. ghst.ly/4lj9C5T


ICYMI: The BloodHound Enterprise team recently pushed out Privilege Zones, one of the most requested features from our community. Irshad Ajmal Ahmed shares a brief overview of how this feature literally expands the capabilities of BloodHound Enterprise. ▶️ ghst.ly/45VdSnX


BloodHound v7.6.0 from SpecterOps is live! This massive release adds Azure PIM Role coverage for all users and introduces our first expansion for Enterprise customers, Privilege Zone Analysis! Full release notes here: bloodhound.specterops.io/resources/rele…

What can you expect next from BloodHound? 👀 Join Justin Kohler & Stephen Hinck (he/him) as they chat with Andy Robbins & Jared Atkinson about some of the exciting new features coming to the platform. Register today! ▶️ ghst.ly/july-web-tw






BloodHound v8.0 is here! 🎉 This update introduces BloodHound OpenGraph, revolutionizing Identity Attack Path Management by exposing attack paths throughout your entire tech stack, not just AD/Entra ID. Read more from Justin Kohler: ghst.ly/bloodhoundv8 🧵: 1/7

Join us for the BloodHound v8.0 deep dive this Thursday! Justin Kohler, Andy Robbins, Jared Atkinson & Stephen Hinck (he/him) will walk through all the new features & show you how to implement these updates in your environment. Register at ghst.ly/july-web-tw 🧵: 7/7


I cannot begin to explain how excited I am about this release. Justin Kohler did a fantastic job explaining the most important new features in his blog and we plan to explain and demo them in even more depth at our webinar on Thursday. Register here: ghst.ly/july-web-tw


Yesterday, I had the pleasure of sitting down with George V. Hulme to discuss BloodHound 8.0, the new BloodHound OpenGraph feature, and the State of Attack Path Management report. His thoughtful coverage dives deep into the nuances of our work. securityboulevard.com/2025/07/mappin…



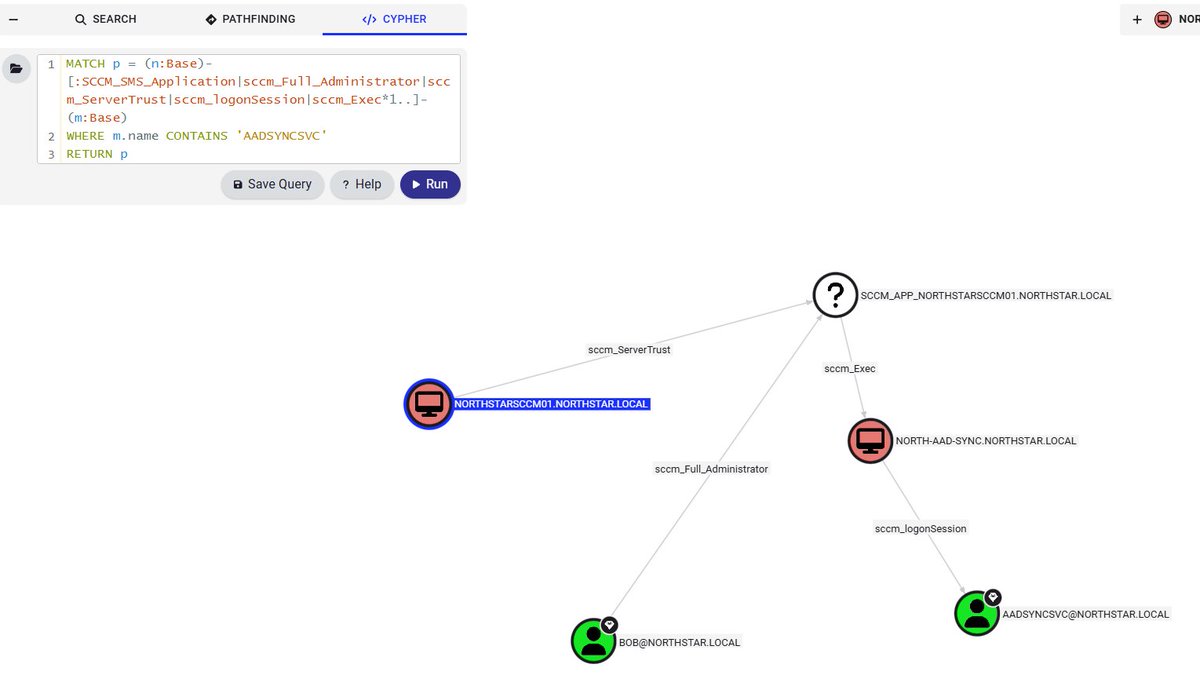
Entra Connect sync accounts can be exploited to hijack device userCertificate properties, enabling device impersonation and conditional access bypass. Daniel Heinsen explores cross-domain compromise tradecraft within the same tenant. Read more ⤵️ ghst.ly/3ISMGN9