
Josh Stroschein | The Cyber Yeti
@jstrosch
Reverse engineer at FLARE/@Google | @pluralsight author | 😱 1M+ views on YT | 🎙️ Host of Behind the Binary podcast 👇
ID: 53809084
https://thecyberyeti.com 05-07-2009 01:40:42
4,4K Tweet
11,11K Followers
1,1K Following






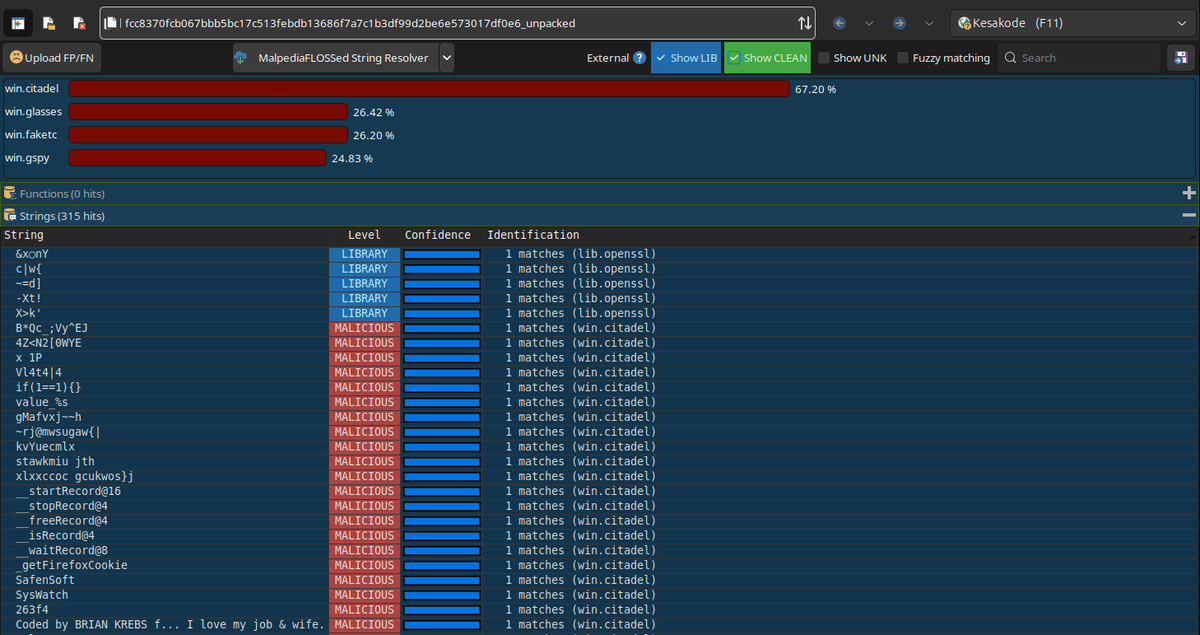
You can now check your strings in #malcat against an online library of #Malpedia FLOSSed strings. Just copy this plugin, courtesy of Daniel Plohmann : github.com/malpedia/malpe…








Honored to join Josh Stroschein | The Cyber Yeti on his podcast "Behind the Binary"! We discussed my RE journey, identifying & analyzing obfuscated code, software protection in industry vs malware, the dynamic between building & breaking protections, ... open.spotify.com/episode/7yJBuB…





