Kévin Tellier
@k3vintell
🥷@Synacktiv
Moved to : bsky.app/profile/kevint…
ID: 1470465850297798657
13-12-2021 18:50:10
63 Tweet
88 Followers
160 Following


During a recent engagement, Justin Bollinger discovered how an attacker can craft a CSR by using default system certificates. After finding out this method was novel, the team kept digging. Read what they found in our new #blog! hubs.la/Q02SCqpG0

Administrator Protection, introduced in the latest Windows Insider Canary build, is a solid security enhancement... uhh.. really?? can be bypassed with Antonio Cocomazzi's clever SspiUacBypass tool. Check it out here: github.com/antonioCoco/Ss…





SCCMSecrets.py. SCCM policies exploitation tool, by Quentin Roland github.com/synacktiv/SCCM…




You can now use LDAP/LDAPs protocols with the SOCKS proxy of ntlmrelayx thanks to the PR from Pierre Milioni (now merged upstream). Here is an example with ldeep using relayed authentication from HTTP to LDAPs :




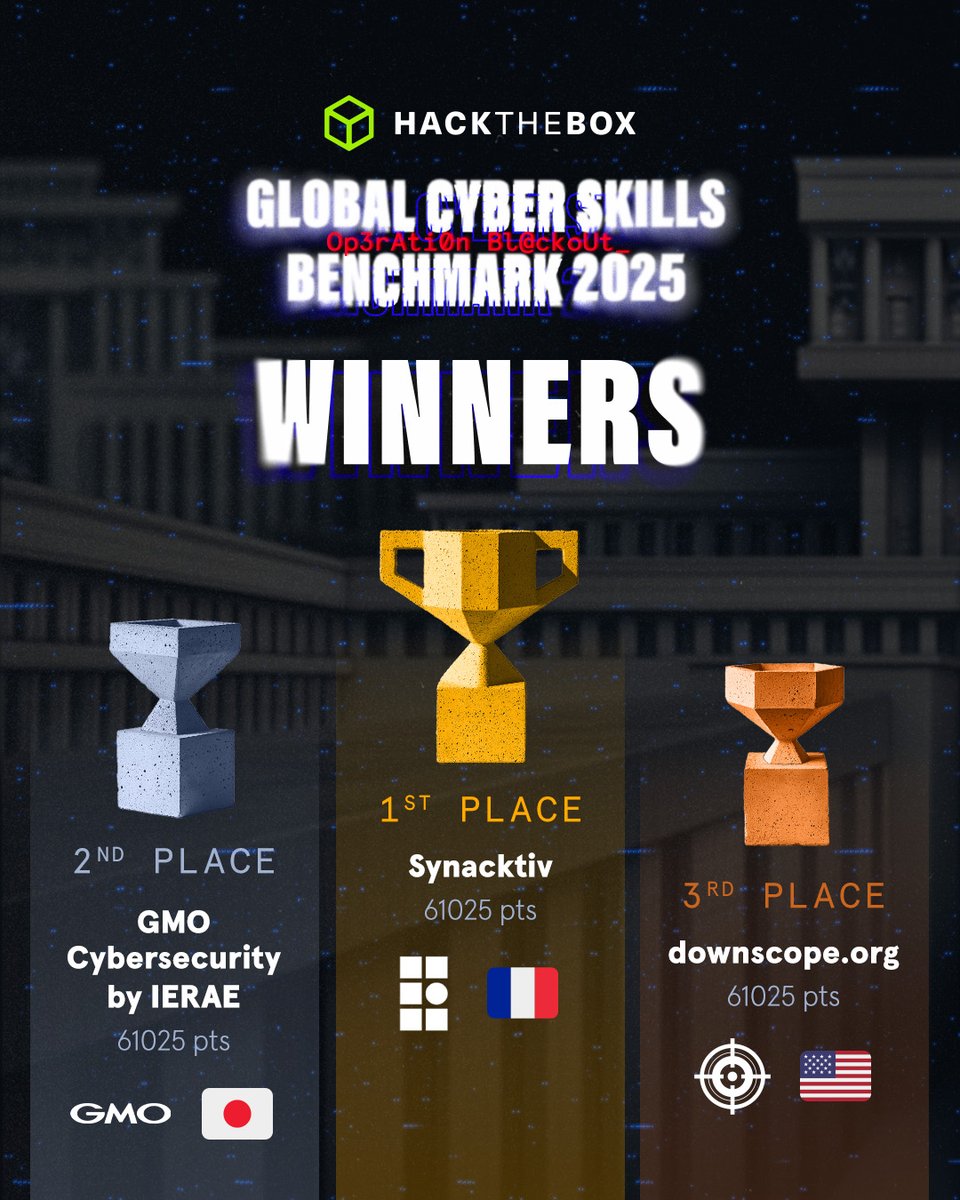
For the second year in a row, we managed to get first place at the #HackTheBox Business #CTF 2025! 🥇 Congratulations to GMOサイバーセキュリティ byイエラエ株式会社【公式】 and Downscope and thanks to Hack The Box for the fun challenges! 🥳


To those who set the bar 🥂 Global Cyber Skills Benchmark 2025 is over, and the leaderboard has spoken. Huge congrats to the top corporate #cybersecurity teams who crushed it in this global competition: 🥇 Synacktiv 🥈 GMOセキュリティ24 |Webサイトリスク・パスワード漏洩診断 | セキュリティAI相談 🥉 downscope.org #HackTheBox