
MalwareHunterTeam
@malwrhunterteam
Official MHT Twitter account.
Check out ID Ransomware (created by @demonslay335).
More photos & gifs, less malware.
ID: 2847021941
https://id-ransomware.malwarehunterteam.com 27-10-2014 17:46:31
68,68K Tweet
239,239K Followers
39 Following





"Atualizacao-Plugin-06-2025-1748972931.js" seen from Brazil: 3bbc57b4a9220df17c25e107579ec6ade2542c1e516f55aa68c646d73d302dcc From: https://javasplugin[.]com/plugin-atualizacao/ 5.189.168[.]52 Germán Fernández
![MalwareHunterTeam (@malwrhunterteam) on Twitter photo "Atualizacao-Plugin-06-2025-1748972931.js" seen from Brazil: 3bbc57b4a9220df17c25e107579ec6ade2542c1e516f55aa68c646d73d302dcc
From: https://javasplugin[.]com/plugin-atualizacao/
5.189.168[.]52
<a href="/1ZRR4H/">Germán Fernández</a> "Atualizacao-Plugin-06-2025-1748972931.js" seen from Brazil: 3bbc57b4a9220df17c25e107579ec6ade2542c1e516f55aa68c646d73d302dcc
From: https://javasplugin[.]com/plugin-atualizacao/
5.189.168[.]52
<a href="/1ZRR4H/">Germán Fernández</a>](https://pbs.twimg.com/media/Gs3lSxxXYAA_sXy.jpg)








When we talk backdoors, we think C2 comms, auth bypasses, persistence. But some leave subtle traces. 🔍 Tools like THOR APT Scanner pick up on weak signals traditional AV/EDR often miss. Sample One of our detection signatures flagged an unusual Linux x64 sample - a stealthy





1/ 🚨🇨🇱 Alerta por comportamiento anómalo en el registro de dominios .CL . H/T CronUp Ciberseguridad 👁️ Se trata de una serie de dominios sospechosos compuestos de 5 letras aleatorias, registrados con poca diferencia de tiempo, utilizando el mismo agente registrador y la misma



![MalwareHunterTeam (@malwrhunterteam) on Twitter photo "查阅6.6\.zip": 42c7f4f0aef68e7de2b06dd7c8409b9248550419c2330a8097cc35c006722f2c
23.235.165[.]126 "查阅6.6\.zip": 42c7f4f0aef68e7de2b06dd7c8409b9248550419c2330a8097cc35c006722f2c
23.235.165[.]126](https://pbs.twimg.com/media/Gs0xpgxXYAAX-zp.jpg)

![MalwareHunterTeam (@malwrhunterteam) on Twitter photo "memfd:a (deleted)": 1b56142f8457af1b488607dc9c004a0e2fc6bb097e472f6c4a3ce83ad513e12e
13.213.71[.]156 "memfd:a (deleted)": 1b56142f8457af1b488607dc9c004a0e2fc6bb097e472f6c4a3ce83ad513e12e
13.213.71[.]156](https://pbs.twimg.com/media/Gs3kLN0WMAA6sYI.jpg)
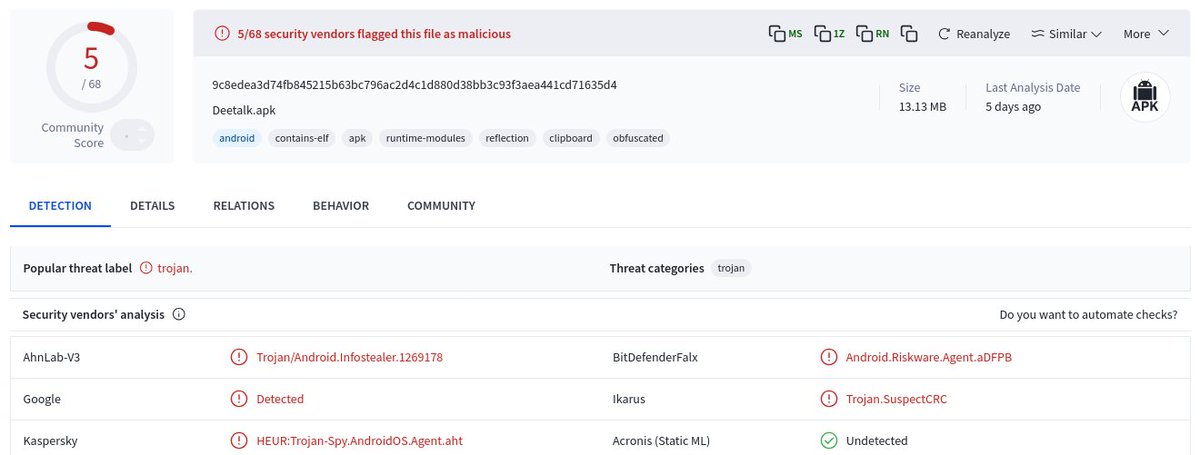
![MalwareHunterTeam (@malwrhunterteam) on Twitter photo "cb59.apk": 61729bab8a31bb183fdeff0914324286b90f5a37adb55349796f2926df274150
188.127.251[.]70 "cb59.apk": 61729bab8a31bb183fdeff0914324286b90f5a37adb55349796f2926df274150
188.127.251[.]70](https://pbs.twimg.com/media/Gs3uJb6XMAArolX.png)
![MalwareHunterTeam (@malwrhunterteam) on Twitter photo "pic_73.apk": 0407cf4b13eebae155632a3b439fe58544aff02638151c5522c8c12cb961a58c
5.252.155[.]145 "pic_73.apk": 0407cf4b13eebae155632a3b439fe58544aff02638151c5522c8c12cb961a58c
5.252.155[.]145](https://pbs.twimg.com/media/Gs3vEMXXEAAq1Mq.jpg)
![MalwareHunterTeam (@malwrhunterteam) on Twitter photo "agent.exe" / "svchost.exe" seen from Turkey: 6416beda6b4273788d3b2197534573a0dfd43a8fde07038ec0776e1b4eccae84
195.154.176[.]101 "agent.exe" / "svchost.exe" seen from Turkey: 6416beda6b4273788d3b2197534573a0dfd43a8fde07038ec0776e1b4eccae84
195.154.176[.]101](https://pbs.twimg.com/media/Gs3wVFlX0AERSVE.jpg)
![Kseniia \n (@naumovax) on Twitter photo 🚨 new C2 communication of #SVCStealer (1st screen) and #stealer version changing (3.3 -> 4.4) with sending uuid in uid (2nd screen) ⬇️
C2: 62.60.226[.]191:27015, 80
app.any.run/tasks/f99aab90…
tria.ge/250604-e7e91sd… 🚨 new C2 communication of #SVCStealer (1st screen) and #stealer version changing (3.3 -> 4.4) with sending uuid in uid (2nd screen) ⬇️
C2: 62.60.226[.]191:27015, 80
app.any.run/tasks/f99aab90…
tria.ge/250604-e7e91sd…](https://pbs.twimg.com/media/Gs_XfioXQAAKtxz.jpg)

![Germán Fernández (@1zrr4h) on Twitter photo Seen from 🇷🇺 "Вложение без имени 00003.doc": 6ce99690955241a306fba345da4c2cc0c747d803eedfe8819bccde848839a781 👁️
Comms to:
http://gemme-cotti[.]ru/zibaba.hta
http://lieri[.]ru:8443/
http://mytho[.]su/bg.rtf
http://emec[.]su/bg.rtf
#CobaltStrike
C2: http://cba.abc92[.]ru:8443/ Seen from 🇷🇺 "Вложение без имени 00003.doc": 6ce99690955241a306fba345da4c2cc0c747d803eedfe8819bccde848839a781 👁️
Comms to:
http://gemme-cotti[.]ru/zibaba.hta
http://lieri[.]ru:8443/
http://mytho[.]su/bg.rtf
http://emec[.]su/bg.rtf
#CobaltStrike
C2: http://cba.abc92[.]ru:8443/](https://pbs.twimg.com/media/GtDe3P0XUAAhSaz.jpg)

![Germán Fernández (@1zrr4h) on Twitter photo ♦️ Meta ad leads to a website that impersonates "TradingView" and downloads an MSI signed by "LLC Torgovyi Dom Energia" (now revoked).
⚠️ Final URL is different from the one shown in the ad.
https://apps-download-pc[.]com/ (malicious site is only displayed if you come from ♦️ Meta ad leads to a website that impersonates "TradingView" and downloads an MSI signed by "LLC Torgovyi Dom Energia" (now revoked).
⚠️ Final URL is different from the one shown in the ad.
https://apps-download-pc[.]com/ (malicious site is only displayed if you come from](https://pbs.twimg.com/media/GtHLPPZXAAArB49.png)
![Germán Fernández (@1zrr4h) on Twitter photo 🚩 Website impersonating AnyDesk on anydeske[.]icu, downloads a .NET loader which then launches a stealer, both unknown to me 🤔
Nexts stages:
- https://pastebin[.]com/raw/YwvHhwUk
- https://pastebin[.]com/raw/WrgrtxSu
- http://45.145.7[.]134/hook/upgrade.php
- 🚩 Website impersonating AnyDesk on anydeske[.]icu, downloads a .NET loader which then launches a stealer, both unknown to me 🤔
Nexts stages:
- https://pastebin[.]com/raw/YwvHhwUk
- https://pastebin[.]com/raw/WrgrtxSu
- http://45.145.7[.]134/hook/upgrade.php
-](https://pbs.twimg.com/media/GtRDtqHXwAAqWlK.png)