G2
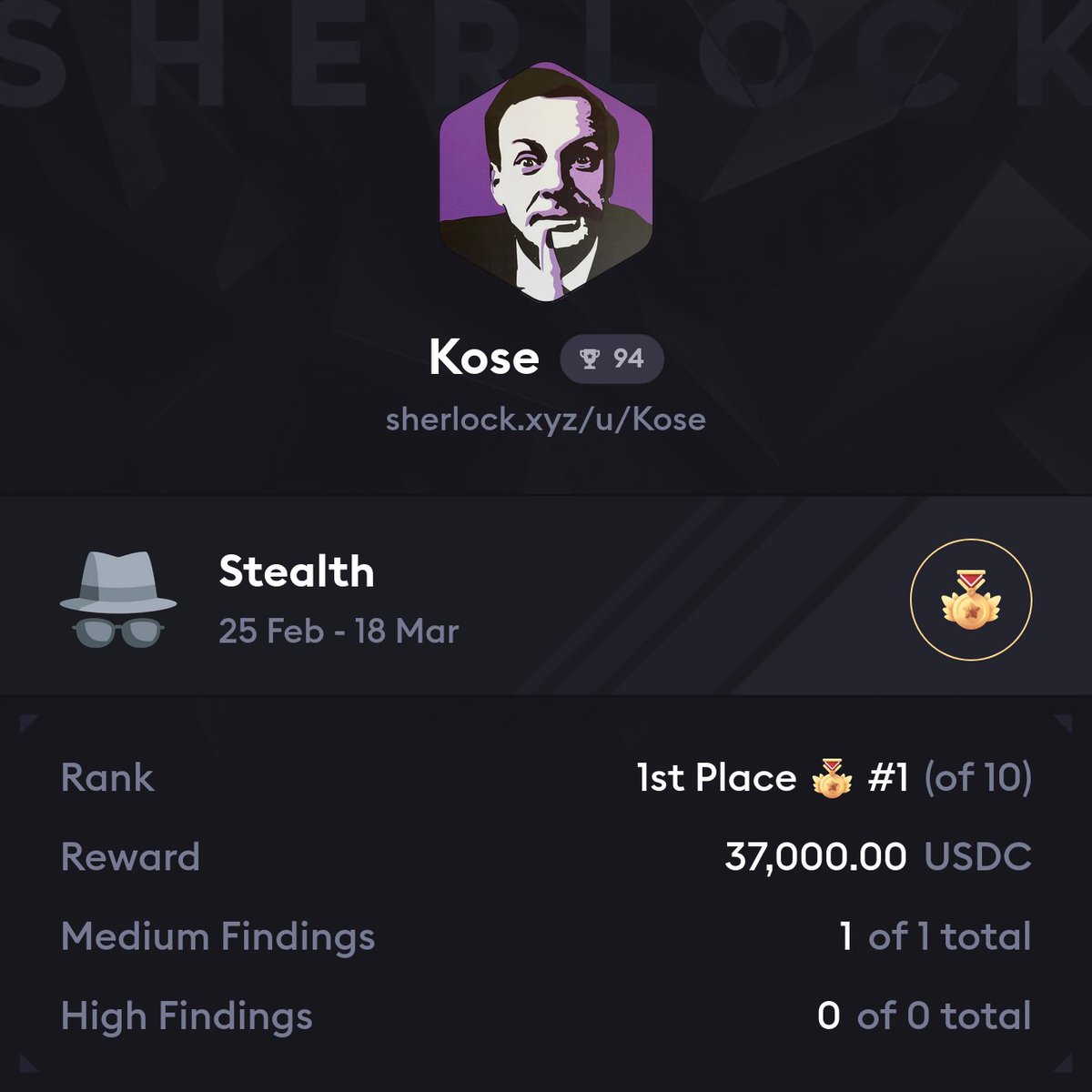
@maymax777
#Crypto Investor | #NFT Builder | #FullStack Engineer |#P2E Maker | #Idea Creator | #Security Researcher
ID: 1256237623913467905
01-05-2020 15:03:08
443 Tweet
87 Followers
1,1K Following






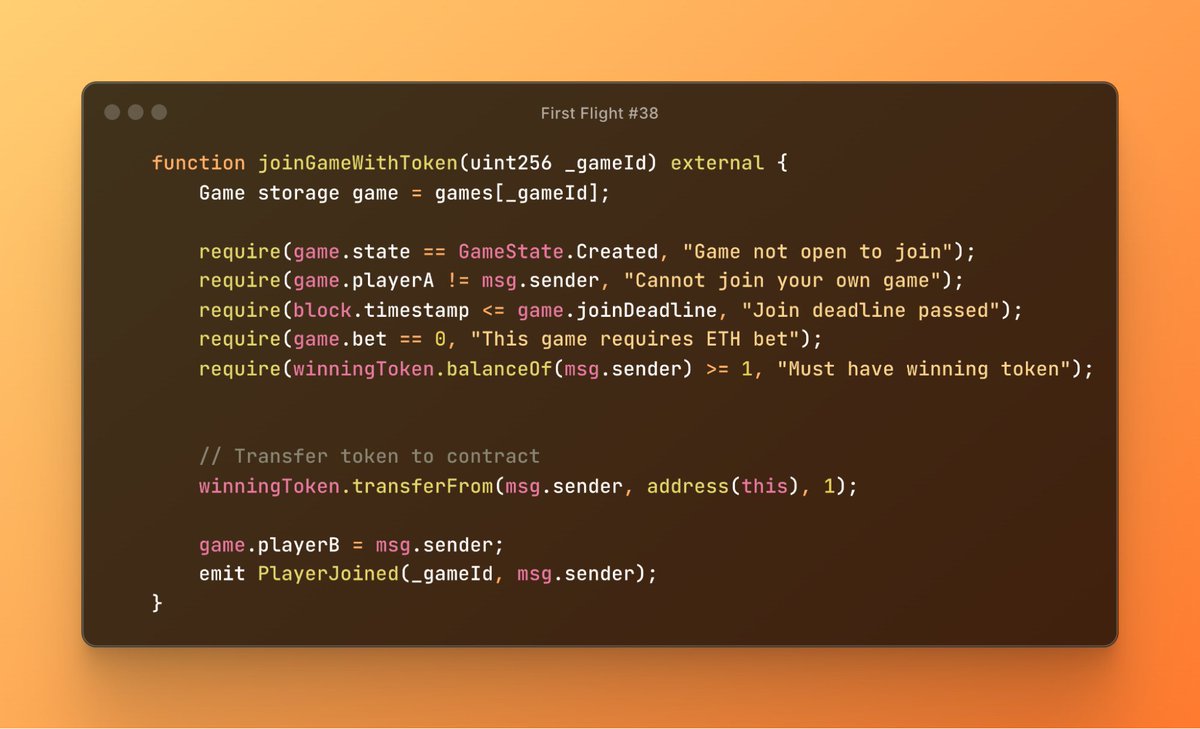
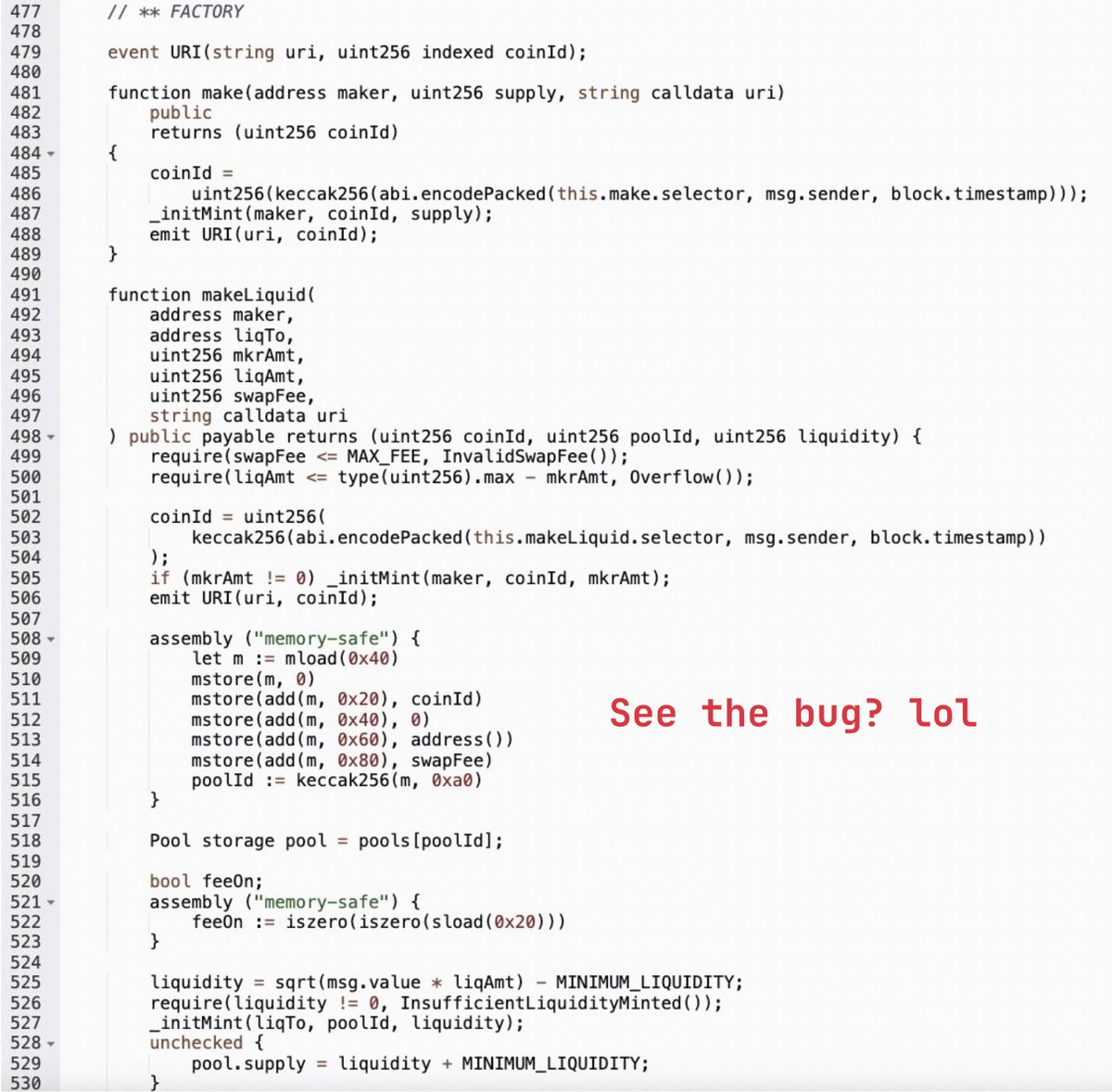
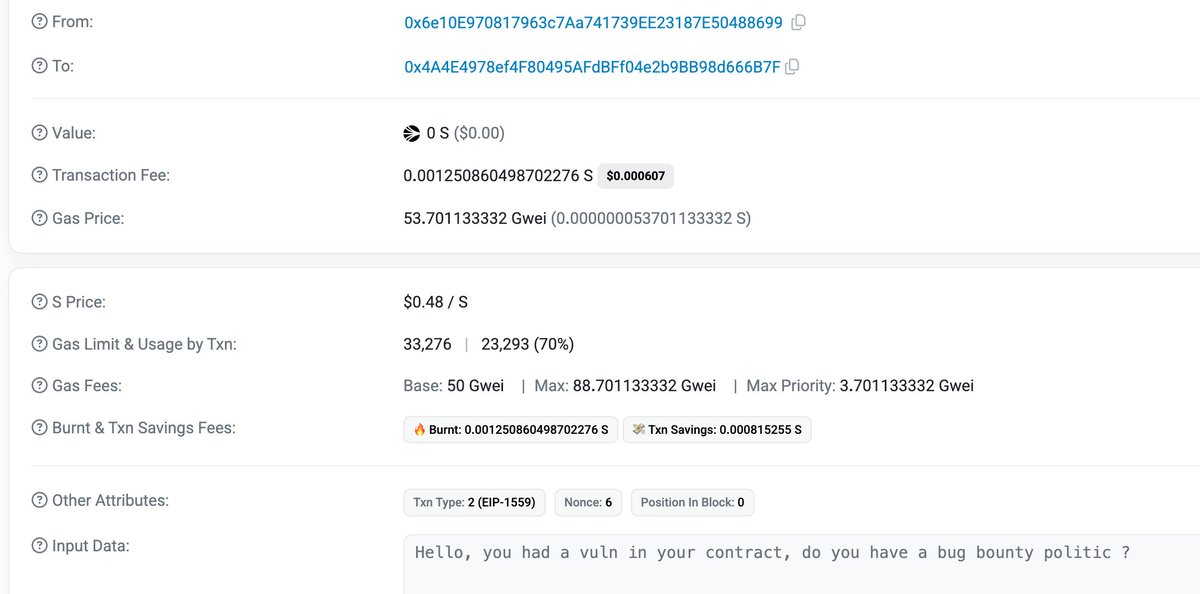
🚨 ALERT! Our system has detected a suspicious transaction on Sonic Labs, resulting in a loss of ~$45K. While the relevant unknown contracts are not open source, the issue appears to be an accounting flaw that allows repaying 0 to withdraw collateral and profit. The 'hacker' is



What a great night at the Web 3 Developers Underground Meetup Web3 Devs Underground 🚀 Had the honour to be a speaker at the event, talk about Web3 security and connect with some great professionals in the industry in person🤝Definitely excited to speak at more meetups to come🎙️