Markus Wulftange
@mwulftange
Principal Security Researcher and Pâtissier at @codewhitesec
ID: 2242897958
12-12-2013 20:45:28
517 Tweet
2,2K Followers
190 Following

We are nominated again for PortSwigger's "Top 10 Web Hacking Techniques" and we're even in with two entries for 2023: ➡️ Java Exploitation Restrictions in Modern JDK Times ➡️ JMX Exploitation Revisited ✍️ Vote now: portswigger.net/polls/top-10-w…





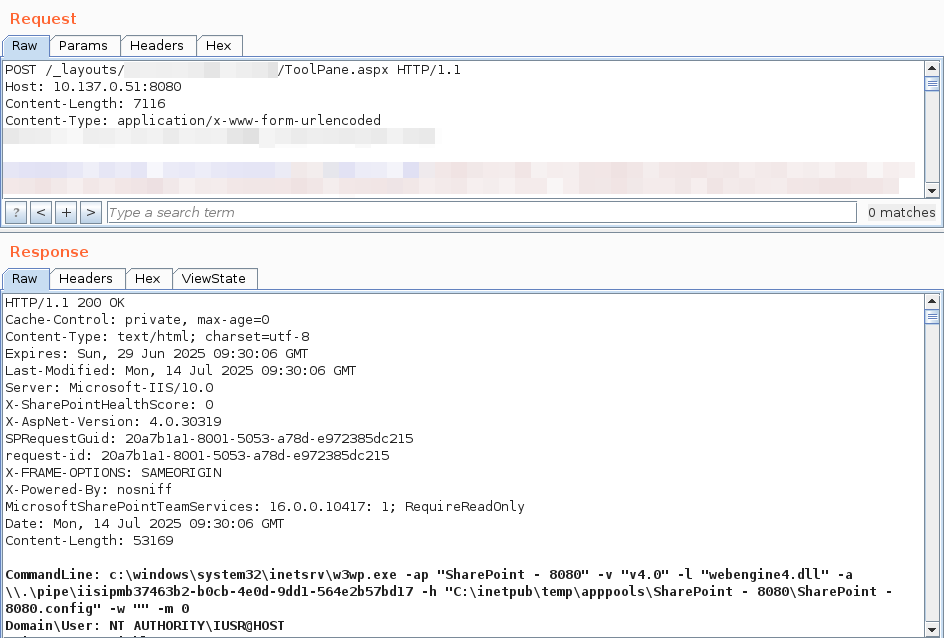
After reassessment by Security Response, this is now tracked as CVE-2024-29059.




Another product, another deserialization vulnerability, another RCE from Markus Wulftange: Patch your Telerik Report Server (CVE-2024-6327 & CVE-2024-6096) code-white.com/public-vulnera…

Teaching the Old .NET Remoting New Exploitation Tricks – read how Markus Wulftange developed novel techniques to exploit Apache log4net's hardened .NET Remoting service: code-white.com/blog/teaching-…


Using Telerik Reporting or Report Server? Patch now to fix 3 RCEs Markus Wulftange found (CVE-2024-8015, CVE-2024-8014, CVE-2024-8048). Telerik vulns have a history of being exploited by threat actors according to CISA Cyber Details at code-white.com/public-vulnera…



Our crew members Markus Wulftange & frycos discovered & responsibly disclosed several new RCE gadgets that bypass #Veeam's blacklist for CVE-2024-40711 & CVE-2025-23120 as well as further entry points following SinSinology & Piotr Bazydło's blog. Don’t blacklist, replace BinaryFormatter.