Chris Au
@netero_1010
Red teamer, my tools for red teaming: github.com/netero1010, my blog to share offensive security stuff: netero1010-securitylab.com
ID: 1066211423653552128
24-11-2018 06:06:27
160 Tweet
1,1K Followers
568 Following











Microsoft Excel now blocking untrusted XLL add-ins by default - Sergiu Gatlan bleepingcomputer.com/news/microsoft…




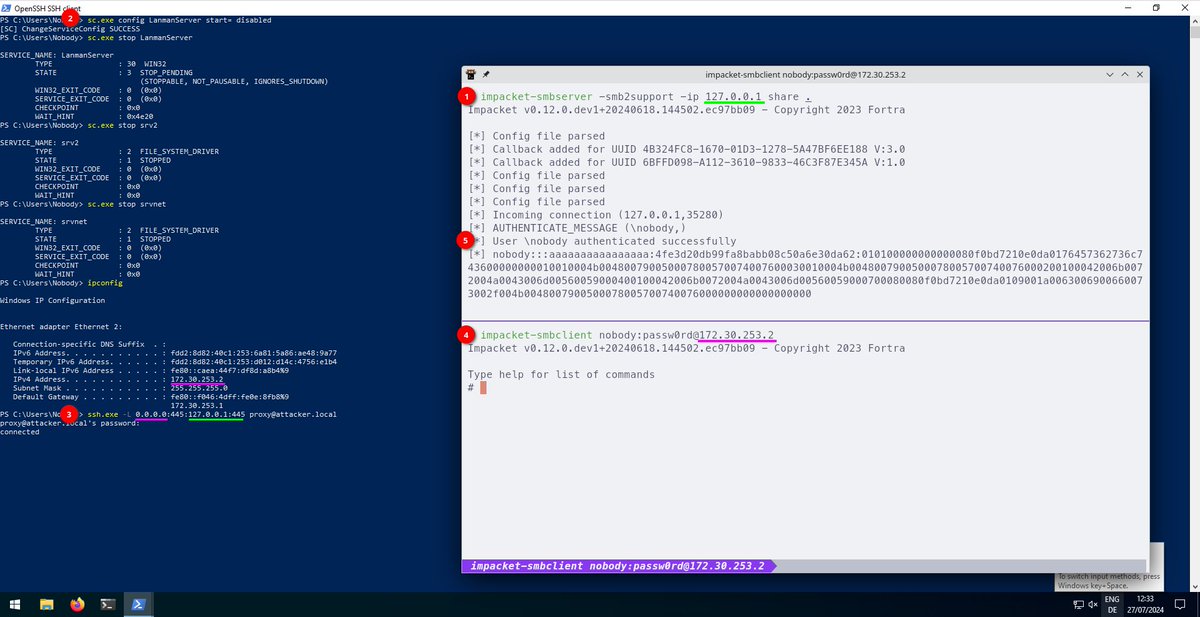
Binding to port 445 on Windows without WinDivert. This is highly useful for NTLM relaying. Big thanks to Nick Powers for the talk.