Neville Grech
@neville_grech
Co-Founder @dedaub & Lecturer @UMMalta
Prev: CS research fellow @uoaofficial @BristolUni @unisouthampton
ID: 721353093
https://www.nevillegrech.com 18-10-2013 22:27:42
509 Tweet
526 Followers
326 Following


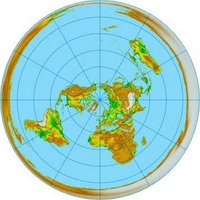












Wondering what happened with the Cetus hack? Join Mitchell Amador and Magnus partner Dedaub Monday for a line by line analysis with Neville Grech and how you can build safely in the most hostile environments. 🗓️ Date: June 2 ⏰ Time: 6pm London x.com/i/spaces/1RDGl…