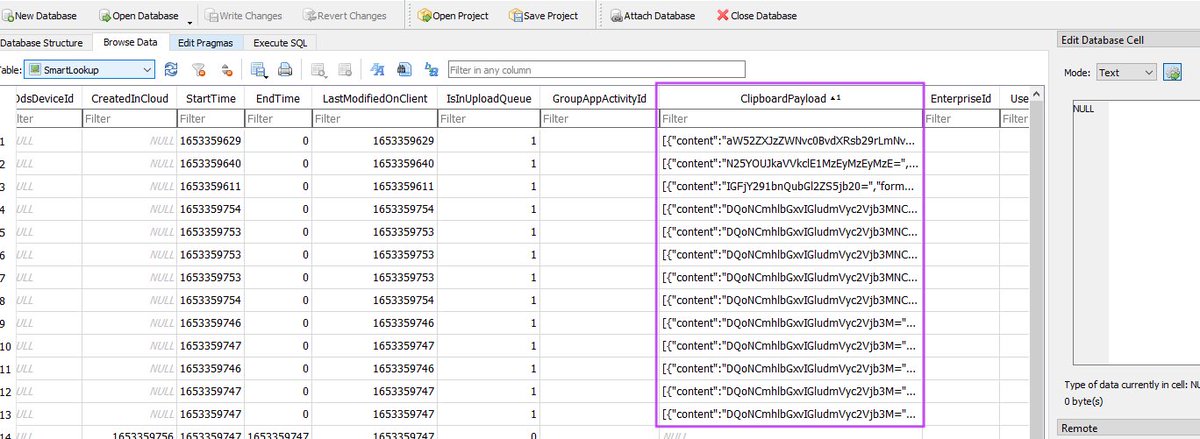
NCV
@nickvourd
Just your friendly neighborhood APT
ID: 1256748254802382848
https://medium.com/@nickvourd 03-05-2020 00:52:03
2,2K Tweet
1,1K Followers
325 Following











Hey everyone! Check out my Crowdcruit profile. I find it extremely useful, especially now that LinkedIn is starting to feel more like Facebook. crowdcruit.com/user/nickvourd






Building off of Cody Burkard's prior work, I put together a tool for automating the decryption of Entra ID application tokens from Azure App Services resources. Here's a blog that outlines the tooling: netspi.com/blog/technical…


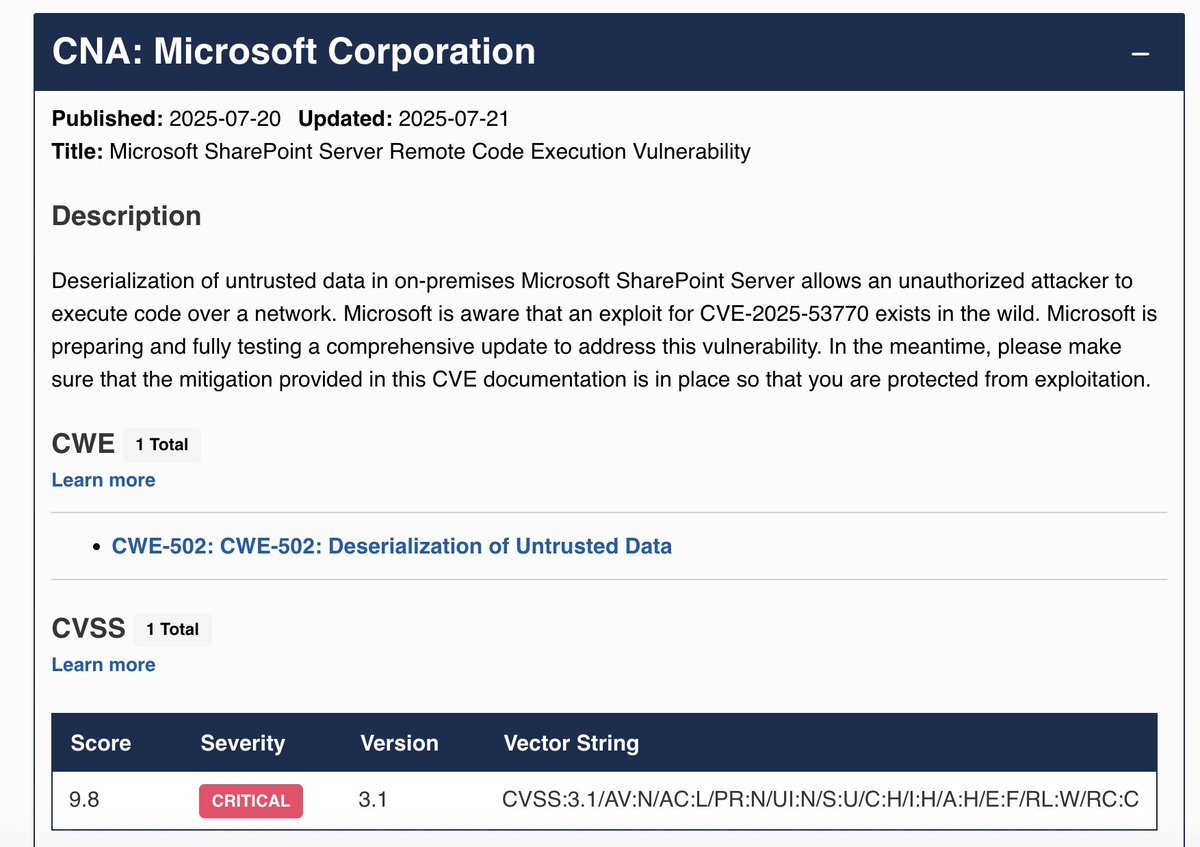
![Black Hills Information Security (@bhinfosecurity) on Twitter photo "If you only have access to a valid machine hash, you can leverage the Kerberos S4U2Self proxy for local privilege escalation [...]"
Read more: blackhillsinfosec.com/abusing-s4u2se…
Abusing S4U2Self for Active Directory Pivoting
by: Hunter Wade
Cross-Posted: 6/11/2025 "If you only have access to a valid machine hash, you can leverage the Kerberos S4U2Self proxy for local privilege escalation [...]"
Read more: blackhillsinfosec.com/abusing-s4u2se…
Abusing S4U2Self for Active Directory Pivoting
by: Hunter Wade
Cross-Posted: 6/11/2025](https://pbs.twimg.com/media/GwFbNQWXwAA3X8p.jpg)